Quantum Signature Method And Quantum Secret Sharing Method Using Quantum Trapdoor One-way Function
HAN; Sang Wook ; et al.
U.S. patent application number 16/739526 was filed with the patent office on 2020-09-10 for quantum signature method and quantum secret sharing method using quantum trapdoor one-way function. This patent application is currently assigned to KOREA INSTITUTE OF SCIENCE AND TECHNOLOGY. The applicant listed for this patent is KOREA INSTITUTE OF SCIENCE AND TECHNOLOGY. Invention is credited to Young Wook CHO, Ji Woong CHOI, Sang Wook HAN, Min Sung KANG, Yong Su KIM, Sang Yun LEE, Sung Wook MOON.
| Application Number | 20200287714 16/739526 |
| Document ID | / |
| Family ID | 1000004606427 |
| Filed Date | 2020-09-10 |











View All Diagrams
| United States Patent Application | 20200287714 |
| Kind Code | A1 |
| HAN; Sang Wook ; et al. | September 10, 2020 |
QUANTUM SIGNATURE METHOD AND QUANTUM SECRET SHARING METHOD USING QUANTUM TRAPDOOR ONE-WAY FUNCTION
Abstract
This specification discloses a quantum public-key cryptosystem. The quantum public-key cryptosystem may use two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution. The two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) do not have a commutation relation or an anti-commutation relation with each other. The commutation relation or the anti-commutation relation is established when either of the following conditions is satisfied: .theta.=2i.pi., .phi.=2j.pi., or {circumflex over (n)}{circumflex over (m)}=1 (i, j=integer), and .theta.=(2k+1).pi., .phi.=(2l+1).pi., or {circumflex over (n)}{circumflex over (m)}=0 (k, l=integer).
| Inventors: | HAN; Sang Wook; (Seoul, KR) ; MOON; Sung Wook; (Seoul, KR) ; KIM; Yong Su; (Seoul, KR) ; LEE; Sang Yun; (Seoul, KR) ; CHO; Young Wook; (Seoul, KR) ; KANG; Min Sung; (Seoul, KR) ; CHOI; Ji Woong; (Seoul, KR) | ||||||||||
| Applicant: |
|
||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Assignee: | KOREA INSTITUTE OF SCIENCE AND
TECHNOLOGY Seoul KR |
||||||||||
| Family ID: | 1000004606427 | ||||||||||
| Appl. No.: | 16/739526 | ||||||||||
| Filed: | January 10, 2020 |
| Current U.S. Class: | 1/1 |
| Current CPC Class: | H04L 9/0852 20130101; H04L 9/0861 20130101; H04L 9/0825 20130101 |
| International Class: | H04L 9/08 20060101 H04L009/08 |
Foreign Application Data
| Date | Code | Application Number |
|---|---|---|
| Mar 6, 2019 | KR | 10-2019-0025896 |
Claims
1. A quantum public-key cryptosystem using two rotation operators) R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution, wherein R n ^ ( .theta. ) = cos ( .theta. 2 ) I - i sin ( .theta. 2 ) ( n x .sigma. x + n y .sigma. y + n z .sigma. z ) and ##EQU00008## R m ^ ( .PHI. ) = cos ( .PHI. 2 ) I - i sin ( .PHI. 2 ) ( m x .sigma. x + m y .sigma. y + m z .sigma. z ) ##EQU00008.2## where {circumflex over (n)}=(n.sub.x,n.sub.y,n.sub.z) and {circumflex over (m)}=(m.sub.x,m.sub.y,m.sub.z) and are rotation axes, and .theta. and .phi. are rotation angles.
2. The quantum public-key cryptosystem of claim 1, wherein the two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfy neither of the following conditions: .theta.=2i.pi., .phi.=2j.pi., or {circumflex over (n)}{circumflex over (m)}=1 (i,j=integer), and .theta.=(2k+1).pi., .phi.=(2l+1).pi., or {circumflex over (n)}{circumflex over (m)}=0 (k,l=integer).
3. The quantum public-key cryptosystem of claim 1, comprising: a unitary transformation configured to encrypt a message in a quantum state |.psi.; and trapdoor information T configured to decrypt an encrypted quantum state |.psi., wherein the unitary transformation equals R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.), and the trapdoor information T equals R.sub.{circumflex over (n)}.sup..dagger.(.theta.).
4. A quantum signature method comprising: (a) generating, by a transmitter, a quantum message |M; (b) generating, by the transmitter, a private key and a public key by using two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution; (c) generating, by the transmitter, a quantum signature |S by applying the rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.); and (d) transmitting, by the transmitter, a quantum signature pair |M|S including the quantum message |M and the quantum signature |S to a receiver.
5. The quantum signature method of claim 4, wherein the two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfy neither of the following conditions: .theta.=2i.pi., .phi.=2j.pi., or {circumflex over (n)}{circumflex over (m)}=1 (i,j=integer), and .theta.=(2k+1).pi., .phi.=(2l+1).pi., or {circumflex over (n)}{circumflex over (m)}=0 (k,l=integer).
6. The quantum signature method of claim 4, wherein operation (b) comprises: (b-1) generating, by the transmitter, an arbitrary quantum state |.psi. and generating a private key R.sub.{circumflex over (n)}(.theta.) satisfying |M=R.sub.{circumflex over (n)}(.theta.)|.psi.; and (b-2) generating, by the transmitter, a public key R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution.
7. The quantum signature method of claim 6, wherein operation (b) further comprises (b-3) transmitting, by the transmitter, the public key R.sub.{circumflex over (m)}(.phi.) through a public channel.
8. The quantum signature method of claim 4, wherein the quantum signature |S is an equation below: |S=R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi..
9. The quantum signature method of claim 4, further comprising (e) verifying, by the receiver, the quantum signature |S by applying a public key R.sub.{circumflex over (m)}.sup..dagger.(.phi.) to the quantum signature pair |M|S received from the transmitter as shown in an equation below: |M|R{circumflex over (m)}.sup..dagger.(.phi.)|S|=|.psi.|R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi.|=|.psi.|e.sup.i.epsilon.|.psi.|=|e.sup.i.epsilon..paral- lel..psi.|.psi.|=1
10. A method of sharing a quantum secret, the method comprising: (a) generating, by a secret generator, a quantum secret |S; (b) generating, by the secret generator, an encryption key and a decryption key by using two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution; (c) generating, by the secret generator, an encrypted quantum secret |S' from the quantum secret by using the encryption key; (d) dividing, by the secret generator, the decryption key into N pieces and transmitting the N pieces of decryption key to a plurality of secret receivers; and (e) transmitting, by the secret generator, the encrypted quantum secret |S'' to a secret verifier.
11. The method of claim 10, wherein the two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfy neither of the following conditions: .theta.=2i.pi., .phi.=2j.pi., or {circumflex over (n)}{circumflex over (m)}=1 (i,j=integer), and .theta.=(2k+1).pi., .phi.=(2l+1).pi., or {circumflex over (n)}{circumflex over (m)}=0 (k,l=integer).
12. The method of claim 10, wherein the encryption key is R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.), the decryption key is R.sub.{circumflex over (n)}.sup..dagger.(.theta.), and the encrypted quantum secret is |S'=R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|S.
Description
CROSS-REFERENCE TO RELATED APPLICATION
[0001] This application claims priority to and the benefit of Korean Patent Application No. 2019-0025896, filed on Mar. 6, 2019, the disclosure of which is incorporated herein by reference in its entirety.
BACKGROUND
1. Field of the Invention
[0002] The present disclosure relates to a quantum public-key cryptosystem, a quantum signature method, and a method of sharing a quantum secret and more particularly, to a quantum public-key system employing a quantum trapdoor one-way function.
2. Discussion of Related Art
[0003] The security of modern cryptography is seriously threatened by development of a quantum computer. In particular, public key cryptography based on computational complexity, such as factoring and discrete logarithm, is easily analyzed by Shor's algorithm implemented by a quantum computer. As an alternative of such modern cryptography, quantum cryptography was proposed. Since quantum cryptography is based on basic principles, such as the no-cloning theorem, the uncertainty principle, and the irreversibility of quantum measurement, security is fundamentally ensured even in a quantum computing environment.
[0004] Quantum Key Distribution (QKD) is a representative quantum cryptography protocol. The QKD protocol enables communicators to share a secret key without meeting together in person. In terms of cryptology, the QKD protocol is symmetric key cryptography and provides only confidentiality among characteristics of a cryptography service, such as confidentiality, integrity, authentication, and non-repudiation. To overcome this limitation, an arbitrated quantum signature scheme, a quantum digital signature scheme, etc. were proposed. However, these protocols are also applications of the QKD protocol and thus cannot be fundamental solutions. Consequently, quantum public-key cryptosystem is required for quantum cryptography to provide confidentiality, integrity, authentication, and non-repudiation.
[0005] In order to implement a quantum public-key cryptosystem, it is necessary to develop a quantum trapdoor one-way function first.
SUMMARY OF THE INVENTION
[0006] The present disclosure is directed to providing a quantum public-key cryptosystem.
[0007] Objects of the present disclosure are not limited to the aforementioned object, and other objects which have not been mentioned will be clearly understood by those of ordinary skill in the art from the following descriptions.
[0008] According to an exemplary embodiment of the present disclosure, a quantum public-key cryptosystem uses two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution.
R n ^ ( .theta. ) = cos ( .theta. 2 ) I - i sin ( .theta. 2 ) ( n x .sigma. x + n y .sigma. y + n z .sigma. z ) and ##EQU00001## R m ^ ( .theta. ) = cos ( .PHI. 2 ) I - i sin ( .PHI. 2 ) ( m x .sigma. x + m y .sigma. y + m z .sigma. z ) ##EQU00001.2##
[0009] where {circumflex over (n)}=(n.sub.x,n.sub.y,n.sub.z) and {circumflex over (m)}=(m.sub.x,m.sub.y,m.sub.z) are rotation axes, and
[0010] .theta. and .phi. are rotation angles.
[0011] According to an exemplary embodiment of the present disclosure, the two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) may satisfy neither of the following conditions:
.theta.=2i.pi., .phi.=2j.pi., or {circumflex over (n)}{circumflex over (m)}=1 (i,j=integer), and
.theta.=(2k+1).pi., .phi.=(2l+1).pi., or {circumflex over (n)}{circumflex over (m)}=0 (k,l=integer).
[0012] According to an exemplary embodiment of the present disclosure, the quantum public-key cryptosystem may include: a unitary transformation configured to encrypt a message in a quantum state |.psi. and trapdoor information T configured to decrypt an encrypted quantum state |.psi.'. The unitary transformation may equal R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.), and the trapdoor information T may equal R.sub.{circumflex over (n)}.sup..dagger.(.theta.).
[0013] According to an exemplary embodiment of the present disclosure, a quantum signature method includes: (a) generating, by a transmitter, a quantum message |M; (b) generating, by the transmitter, a private key and a public key by using two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution; (c) generating, by the transmitter, a quantum signature |S by applying the rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.); and (d) transmitting, by the transmitter, a quantum signature pair |M|S including the quantum message |M and the quantum signature |S to a receiver.
[0014] According to an exemplary embodiment of the present disclosure, operation (b) may include: (b-1) generating, by the transmitter, an arbitrary quantum state |.psi. and generating a private key R.sub.{circumflex over (n)}(.theta.) satisfying |M=R.sub.{circumflex over (n)}(.theta.)|.psi.; and (b-2) generating, by the transmitter, a public key R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution.
[0015] According to an exemplary embodiment of the present disclosure, operation (b) may further include (b-3) transmitting, by the transmitter, the public key R.sub.{circumflex over (m)}(.phi.) through a public channel.
[0016] According to an exemplary embodiment of the present disclosure, the quantum signature |S may be an equation below:
|S=R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi.
[0017] According to an exemplary embodiment of the present disclosure, the quantum signature method may further include (e) verifying, by the receiver, the quantum signature |S by applying a public key R.sub.{circumflex over (m)}.sup..dagger.(.phi.) to the quantum signature pair |M|S received from the transmitter as shown in an equation below:
|M|R.sub.{circumflex over (m)}.sup..dagger.(.phi.)|S|=|.psi.|R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi.|=|.psi.|e.sup.i.epsilon.|.psi.|=|e.sup.i.epsilon.||.psi- .|.psi.|=1
[0018] According to an exemplary embodiment of the present disclosure, a method of sharing a quantum secret includes: (a) generating, by a secret generator, a quantum secret |S; (b) generating, by the secret generator, an encryption key and a decryption key by using two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution; (c) generating, by the secret generator, an encrypted quantum secret |S from the quantum secret by using the encryption key; (d) dividing, by the secret generator, the decryption key into N pieces and transmitting the N pieces of decryption key to a plurality of secret receivers; and (e) transmitting, by the secret generator, the encrypted quantum secret |S' to a secret verifier.
[0019] According to an exemplary embodiment of the present disclosure, the encryption key may be R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.), the decryption key may be R.sub.{circumflex over (n)}.sup..dagger.(.theta.), and the encrypted quantum secret may be |S'=R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|S.
[0020] Other details of the present disclosure are included in the detailed description and drawings.
BRIEF DESCRIPTION OF THE DRAWINGS
[0021] The above and other objects, features and advantages of the present disclosure will become more apparent to those of ordinary skill in the art by describing in detail exemplary embodiments thereof with reference to the accompanying drawings, in which:
[0022] FIG. 1 is a conceptual diagram schematically showing a cyclic evolution under a non-(anti-)commutation relation condition and a non-cyclic evolution under a (anti) commutation relation condition in the Special Unitary Group of Degree 2 (SU(2));
[0023] FIG. 2 is an exemplary diagram showing a cyclic evolution of an arbitrary quantum state |.psi. realized by rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) on the Bloch sphere;
[0024] FIGS. 3 to 6 are exemplary diagrams separately showing cyclic evolutions of an arbitrary quantum state |.psi. realized by rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.), which satisfy a non-commutation relation condition or a non-anti-commutation relation condition, on the Bloch sphere;
[0025] FIG. 7 is a set of exemplary diagrams showing non-cyclic evolutions of an arbitrary quantum state |.psi. realized by rotation operators and R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.), which satisfy a commutation relation condition, on the Bloch sphere;
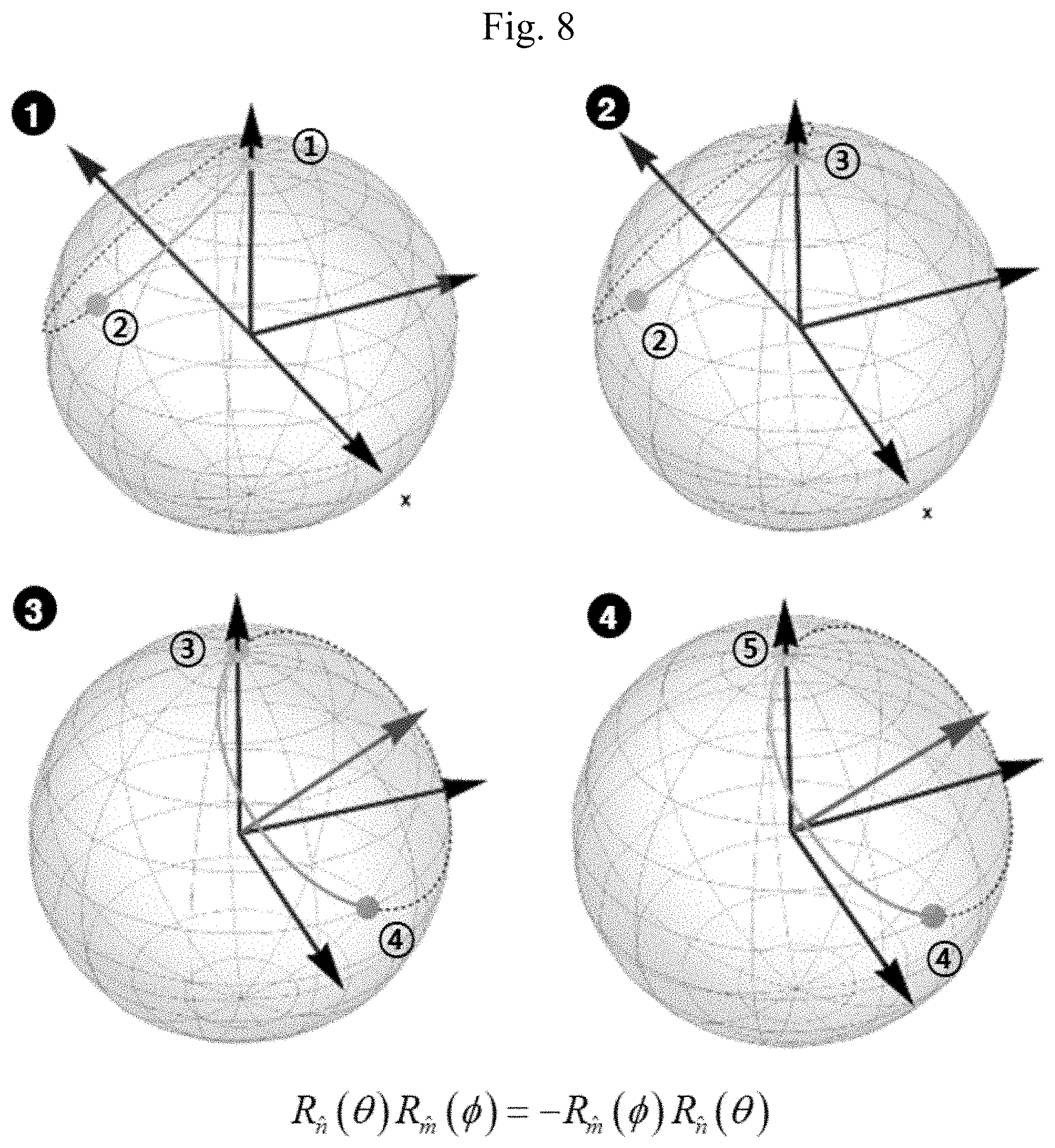
[0026] FIG. 8 is a set of exemplary diagrams showing non-cyclic evolutions of an arbitrary quantum state |.psi. realized by rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.), which satisfy an anti-commutation relation condition, on the Bloch sphere;
[0027] FIGS. 9 to 11 show an average Uhlmann's fidelity |.psi.|R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi.| of R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi. and |.psi.;
[0028] FIG. 12 is a flowchart of a quantum signature method according to an exemplary embodiment of the present disclosure;
[0029] FIG. 13 is a conceptual diagram of a quantum signature method according to an exemplary embodiment of the present disclosure;
[0030] FIG. 14 is a flowchart of a method of sharing a quantum secret according to an exemplary embodiment of the present disclosure; and
[0031] FIG. 15 is a conceptual diagram of a method of sharing a quantum secret according to an exemplary embodiment of the present disclosure.
DETAILED DESCRIPTION OF EXEMPLARY EMBODIMENTS
[0032] Advantages and features of the present disclosure and methods for achieving them will be made clear from embodiments described below with reference to the accompanying drawings. However, the present disclosure may be embodied in many different forms and should not be construed as being limited to the embodiments set forth herein. Rather, these embodiments are provided so that this disclosure will be thorough and complete and will fully convey the scope of the present disclosure to those of ordinary skill in the technical field to which the present disclosure pertains. The present disclosure is only defined by the claims.
[0033] This specification discloses a quantum signature method and a quantum secret sharing method employing a quantum trapdoor one-way function. A quantum trapdoor one-way function uses a cyclic evolution of an arbitrary quantum state and uses a condition under which such a cyclic evolution occurs as trapdoor information. The trapdoor information of a quantum trapdoor one-way function may be used as a public key of a quantum public-key system, and in this way, the trapdoor information may be used in a quantum signature method and a quantum secret sharing method. In this specification, it will be disclosed that that a quantum trapdoor one-way function may be designed by using a cyclic evolution of an arbitrary quantum state, and a quantum signature method and a quantum secret sharing method, which are application techniques of a quantum public-key cryptosystem based on the fact, will be described.
[0034] As for a trapdoor one-way function, like a one-way function, it is easy to calculate an output y when an input x is given. In reverse, however, when the output y is given, it is difficult to calculate the input x. Only when special information referred to as a trapdoor is given, it is possible to easily calculate the input x. It is known that a quantum trapdoor one-way function having the same function as the trapdoor one-way function does not exist substantially in quantum cryptography. However, this specification will disclose that it is possible to design a quantum trapdoor one-way function by using a cyclic evolution of an arbitrary quantum state.
[0035] In quantum mechanics, a cyclic evolution refers to a case in which an arbitrary quantum state undergoes a unitary transformation and returns to itself not via the same route. Due to such a cyclic evolution, a global phase e.sup.i.epsilon. of an arbitrary quantum state
.psi. = cos ( .alpha. 2 ) 0 + e i .beta. sin ( .alpha. 2 ) 1 ##EQU00002##
is obtained as follows.
|.psi.=e.sup.i.epsilon.|.psi. [Equation 1]
[0036] Here, is a unitary operator, and the global phase e.sup.i.epsilon. is not .+-.1. The cyclic evolution of Equation 1 is represented as Equation 2 and Equation 3 below by using two single qubit unitary operators.
R n ^ ( .theta. ) = cos ( .theta. 2 ) I - i sin ( .theta. 2 ) ( n x .sigma. x + n y .sigma. y + n z .sigma. z ) [ Equation 2 ] R m ^ ( .theta. ) = cos ( .PHI. 2 ) I - i sin ( .PHI. 2 ) ( m x .sigma. x + m y .sigma. y + m z .sigma. z ) [ Equation 3 ] ##EQU00003##
[0037] Four evolutions may be represented as Equation 4 below by using Equation 2 and Equation 3.
R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi.=e.sup.i.epsilon.|.psi. [Equation 4]
[0038] Here, {circumflex over (n)}=(n.sub.x,n.sub.y,n.sub.z) and {circumflex over (m)}=(m.sub.x,m.sub.y,m.sub.z) are rotation axes, and .theta. and .phi. are rotation angles
[0039] R.sub.{circumflex over (n)}(.theta.) of Equation 2 and R.sub.{circumflex over (m)}(.phi.) of Equation 3 are not in a commutation relation or an anti-commutation relation so that Equation 4 may become a cyclic evolution. A condition under which R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) have a commutation relation [R.sub.{circumflex over (n)}(.theta.),R.sub.{circumflex over (m)}(.phi.)]=R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)-R.sub.{circumflex over (m)}(.phi.)R.sub.{circumflex over (n)}(.theta.)=0 or an anti-commutation relation [R.sub.{circumflex over (n)}(.theta.),R.sub.{circumflex over (m)}(.phi.)]=R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)-R.sub.{circumflex over (m)}(.phi.)R.sub.{circumflex over (n)}(.theta.)=0 is shown in Equation 5 or Equation 6 below.
.theta.=2i.pi., .phi.=2j.pi., or {circumflex over (n)}{circumflex over (m)}=1 (i,j=integer) [Equation 5]
.theta.=(2k+1).pi., .phi.=(2l+1).pi., or {circumflex over (n)}{circumflex over (m)}=0 (k,l=integer) [Equation 6]
[0040] When {circumflex over (n)}{circumflex over (m)}=1 is satisfied, {circumflex over (n)}=(n.sub.x,n.sub.y,n.sub.z) and {circumflex over (m)}=(m.sub.x,m.sub.y,m.sub.z) are equal to each other. When {circumflex over (n)}{circumflex over (m)}=0 is satisfied, {circumflex over (n)}=(n.sub.x,n.sub.y,n.sub.z) and {circumflex over (m)}=(m.sub.x,m.sub.y,m.sub.z) are orthogonal to each other.
[0041] When R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfy the commutation relation of Equation 5 and the anti-commutation relation of Equation 6, a global phase e.sup.i.alpha. in Equation 4 becomes .+-.1 as shown in Equation 7 below.
R{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi.=.+-.R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (m)}(.phi.)|.psi.=1|.psi. [Equation 7]
[0042] FIG. 1 is a conceptual diagram schematically showing a cyclic evolution under a non-(anti) commutation relation condition and a non-cyclic evolution under a (anti) commutation relation condition in the Special Unitary Group of Degree 2 (SU(2)).
[0043] FIG. 2 is an exemplary diagram showing a cyclic evolution of an arbitrary quantum state |.psi. realized by rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) on the Bloch sphere.
[0044] Referring to FIG. 2, the arbitrary quantum state |.psi. initially starts at a location {circle around (1)} and moves to locations {circle around (2)}, {circle around (3)}, {circle around (4)}, and {circle around (5)} in sequence. It is possible to see that the final location {circle around (5)} is identical to the initial location {circle around (1)}.
[0045] FIGS. 3 to 6 are exemplary diagrams separately showing cyclic evolutions of the arbitrary quantum state |.psi. realized by the rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.), which satisfy a non-commutation relation condition or a non-anti-commutation relation condition, on the Bloch sphere.
[0046] Referring to FIG. 3, the arbitrary quantum state |.psi. rotates counterclockwise from the initial location {circle around (1)} to the location {circle around (2)} by the rotation operator R.sub.{circumflex over (m)}(.phi.).
[0047] Referring to FIG. 4, the quantum state at the location {circle around (2)} rotates counterclockwise to the location {circle around (3)} by the rotation operator R.sub.{circumflex over (n)}(.theta.).
[0048] Referring to FIG. 5, the quantum state at the location {circle around (3)} rotates to the location {circle around (4)} by a rotation operator R.sub.{circumflex over (m)}.sup..dagger.(.phi.). The rotation operator R.sub.{circumflex over (m)}.sup..dagger.(.phi.) is an inverse rotation operator of the rotation operator R.sub.{circumflex over (m)}(.phi.) and rotates clockwise about the same rotation axis.
[0049] Referring to FIG. 6, the quantum state at the location {circle around (4)} rotates to the location {circle around (5)} by a rotation operator R.sub.{circumflex over (n)}.sup..dagger.(.theta.). The rotation operator R.sub.{circumflex over (n)}.sup..dagger.(.theta.) is an inverse rotation operator of the rotation operator R.sub.{circumflex over (n)}(.theta.) and rotates clockwise about the same rotation axis.
[0050] FIGS. 3 to 6 show an example in which an arbitrary quantum state rotates counterclockwise first and then inversely rotates clockwise. However, this is merely an example, and rotation directions are not limited to the example shown in the drawings.
[0051] FIG. 7 is a set of exemplary diagrams showing non-cyclic evolutions of an arbitrary quantum state |.psi. realized by the rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.), which satisfy a commutation relation condition, on the Bloch sphere.
[0052] FIG. 8 is a set of exemplary diagrams showing non-cyclic evolutions of an arbitrary quantum state |.psi. realized by the rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.), which satisfy an anti-commutation relation condition, on the Bloch sphere.
[0053] It is possible to see that the rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) shown in FIGS. 7 and 8 satisfy a commutation relation condition or an anti-commutation relation condition and thus the arbitrary quantum state |.psi. returns to its original location. Therefore, the rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfying a commutation relation condition or an anti-commutation relation condition are not suitable for use in a quantum public-key cryptosystem.
[0054] FIGS. 9 to 11 show an average Uhlmann's fidelity |.psi.|R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi.| of R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi. and |.psi..
[0055] In FIGS. 9 to 11, R.sub.{circumflex over (m)}(.phi.) is fixed, and a rotation axis {circumflex over (n)} and a rotation angle .theta. of R.sub.{circumflex over (n)}(.theta.) are changed. In FIGS. 9 to 11, |.psi. is |z.+-., |x.+-., and |y.+-., respectively.
[0056] Referring to FIGS. 9 to 11, a point at which a cyclic evolution occurs varies according to |.psi. as shown by a green point (a point indicated by a solid-line arrow). However, a point at which a non-cyclic evolution occurs is fixed as shown by a blue solid line (a line indicated by a broken-line arrow).
[0057] In this specification, the unitary transformation which transforms the arbitrary quantum state |.psi. into another quantum state |.psi.' is defined as a quantum trapdoor one-way function, and trapdoor information is defined as T. Details thereof are as follows: [0058] Input state:
[0058] .psi. = cos ( .alpha. 2 ) 0 + e i .beta. sin ( .alpha. 2 ) 1 ##EQU00004## [0059] Output state: |.psi.'=|.psi. [0060] Unitary transformation: =R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.), [R.sub.{circumflex over (n)}(.theta.),R.sub.{circumflex over (m)}(.phi.)].noteq.0, {R.sub.{circumflex over (n)}(.theta.),R.sub.{circumflex over (m)}(.phi.)}.noteq.0 [0061] Trapdoor information: T=R.sub.{circumflex over (n)}.sup..dagger.(.theta.)
[0062] The unitary transformation is a combination R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.) of the rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.). In this case, R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfy [R.sub.{circumflex over (n)}(.theta.),R.sub.{circumflex over (m)}(.phi.)].noteq.0 and {R.sub.{circumflex over (n)}(.theta.),R.sub.{circumflex over (m)}(.phi.)}.noteq.0. When the output state |.psi.'=|.psi. is given, it is very difficult to obtain the input state |.psi. by inverse operation. In this case, it is possible to easily acquire the quantum state e.sup.i.alpha.|.psi. by applying the trapdoor information T=R.sub.{circumflex over (n)}.sup..dagger.(.theta.) to the output state |.psi.'=|.psi.. This is represented by Equation 8 below.
T|.psi.'=T|.psi.R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi.=e.sup.i.alpha.|.psi. [Equation 8]
[0063] e.sup.i.alpha.|.psi. of Equation 8 differs from the input state |.psi. only in the global phase e.sup.i.alpha.. When e.sup.i.alpha.|.psi. and |.psi. are input to a swap test, the result is given by Equation 9 below.
1/2{|0.sub.ancilla[e.sup.i.alpha.|.psi..sub.1)|.psi..sub.2+|.psi..sub.1(- e.sup.i.alpha.|.psi..sub.2)]+|1.sub.ancilla[(e.sup.i.alpha.|.psi..sub.1)|.- psi..sub.2-|.psi..sub.1(e.sup.i.alpha.|.psi..sub.2)]} [Equation 9]
[0064] Since Equation 9 becomes Equation 10 given below, the measurement results of ancilla qubits become |0.sub.ancilla at all times.
0 ancilla [ 1 2 ( e i .alpha. | .psi. 1 ) | .psi. 2 + .psi. 1 ( e - i .alpha. | .psi. 2 ) ] [ Equation 10 ] ##EQU00005##
[0065] Consequently, it is determined in the swap test that the two quantum states e.sup.i.alpha.|.psi. and |.psi. are identical. It has been described above that the green point (indicated by a solid-line arrow) of FIGS. 9 to 11 represents a point at which an Uhlmann's fidelity |.psi.|e.sup.i.alpha.|.psi. of the quantum states e.sup.i.alpha.|.psi. and |.psi. equals 1. Another important characteristic of a trapdoor one-way function is that it is not possible to know what kind of operation corresponds to a function only from trapdoor information. A point at which a cyclic evolution occurs varies according to |.psi. as shown by the green point (indicated by a solid-line arrow) of FIGS. 9 to 11. Therefore, although the trapdoor information T=R.sub.{circumflex over (n)}.sup..dagger.(.theta.) is acquired, it is not possible to know R.sub.{circumflex over (m)}(.phi.) when |.psi. is not acquired. Consequently, the quantum trapdoor one-way function according to this specification does not allow estimation of the unitary transformation =R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.) only based on the trapdoor information T=R.sub.{circumflex over (n)}.sup..dagger.(.theta.) like a trapdoor one-way function of current cryptography. Due to this characteristic of a quantum trapdoor one-way function, when the quantum trapdoor one-way function is applied to a cryptosystem, it is possible to ensure security and also provide various cryptography services.
[0066] A quantum signature method and a quantum secret sharing method of a quantum public-key cryptosystem employing a quantum trapdoor one-way function will be described below.
[0067] A quantum signature method will be described first. Communicators include a transmitter Alice and a receiver Bob.
[0068] FIG. 12 is a flowchart of a quantum signature method according to an exemplary embodiment of the present disclosure.
[0069] FIG. 13 is a conceptual diagram of a quantum signature method according to an exemplary embodiment of the present disclosure.
[0070] Referring to FIGS. 12 and 13, in a quantum signature method according to an exemplary embodiment of the present disclosure, the transmitter Alice generates a quantum message |M corresponding to a message first (Operation S10).
[0071] Subsequently, the transmitter Alice may generate a private key and a public key using two rotation operators R.sub.{circumflex over (n)}(.theta.) and R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution (Operation S20).
[0072] More specifically, the transmitter Alice generates an arbitrary quantum state
.psi. = cos ( .alpha. 2 ) 0 + e i .beta. sin ( .alpha. 2 ) 1 ##EQU00006##
and generates a private key R.sub.{circumflex over (n)}(.theta.) satisfying |M=R.sub.{circumflex over (n)}(.theta.)|.psi.. Also, the transmitter Alice generates a public key R.sub.{circumflex over (m)}(.phi.) satisfying a cyclic evolution such R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi.=e.sup.i.alpha.|.psi.. Additionally, the transmitter Alice may transmit a generated public key R.sub.{circumflex over (m)}.sup..dagger.(.phi.) to the receiver Bob through a public channel.
[0073] Subsequently, the transmitter Alice may generate a quantum signature |S=R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi. by consecutively applying the operators R.sub.{circumflex over (m)}(.phi.) and R.sub.{circumflex over (n)}(.theta.) to the arbitrary quantum state |.psi. (Operator S30).
[0074] Subsequently, the transmitter Alice may transmit a quantum signature pair |M|S including the quantum message |M corresponding to the message and the quantum signature |S to the receiver Bob (Operation S40).
[0075] Subsequently, to verify the quantum signature pair |M|S received from the transmitter Alice, the receiver Bob may apply the public key R.sub.{circumflex over (m)}.sup..dagger.(.phi.) to the quantum signature |S as shown in Equation 11 below (Operation S50).
R.sub.{circumflex over (m)}.sup..dagger.(.phi.)|S=R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi. [Equation 11]
[0076] More specifically, as shown in Equation 12 below, the receiver Bob may check an Uhlmann's fidelity |M|R.sub.{circumflex over (m)}.sup..dagger.(.phi.)|S| with respect to R.sub.{circumflex over (m)}.sup..dagger.(.phi.)|S of FIG. 11 to which the quantum message |M and the public key R.sub.{circumflex over (m)}.sup..dagger.(.phi.) are applied.
|M|R{circumflex over (m)}.sup..dagger.(.phi.)|S|=|.psi.|R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|.psi.|=|.psi.|e.sup.i.epsilon.|.psi.|=|e.sup.i.epsilon..paral- lel..psi.|.psi.|=1 [Equation 12]
[0077] At this time, the receiver Bob accepts the quantum signature pair of the transmitter Alice when a value of the Uhlmann's fidelity |M|R.sub.{circumflex over (m)}.sup..dagger.(.phi.)|S| is 1, and rejects the quantum signature otherwise. The Uhlmann's fidelity may be implemented through a swap test.
[0078] Next, a quantum secret sharing method will be described. Communicators include a secret generator Alice, a plurality of secret receivers Bob #1 to Bob # N, and a secret verifier Charlie.
[0079] FIG. 14 is a flowchart of a method of sharing a quantum secret according to an exemplary embodiment of the present disclosure.
[0080] FIG. 15 is a conceptual diagram of a method of sharing a quantum secret according to an exemplary embodiment of the present disclosure. Referring to FIGS. 14 and 15, first, the secret generator Alice may generate a quantum secret
S = cos ( .alpha. 2 ) 0 + e i .beta. sin ( .alpha. 2 ) 1 ##EQU00007##
(Operation S100).
[0081] Subsequently, the secret generator Alice may generate an encryption key R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.) and a decryption key R.sub.{circumflex over (n)}.sup..dagger.(.theta.) by applying operators R.sub.{circumflex over (m)}(.phi.) and R.sub.{circumflex over (n)}(.theta.) to the quantum secret |S (Operation S200). Here, R.sub.{circumflex over (m)}(.phi.) and R.sub.{circumflex over (n)}(.theta.) may satisfy a cyclic evolution such as R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|S=e.sup.i.epsilon.|S
[0082] Subsequently, the secret generator Alice may generate an encrypted quantum secret |S' from the quantum secret |S using the encryption key R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.) (Operation S300). More specifically, the encrypted quantum secret satisfies |S'=R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|S.
[0083] Subsequently, the secret generator Alice may divide the decryption key R.sub.{circumflex over (n)}.sup..dagger.(.theta.) into N pieces such as R.sub.{circumflex over (n)}.sup..dagger.(.theta..sub.1)R.sub.{circumflex over (n)}.sup..dagger.(.theta..sub.2) . . . R.sub.{circumflex over (n)}.sup..dagger.(.theta..sub.N). Then, the secret generator Alice may transmit the divided pieces of decryption key R.sub.{circumflex over (n)}.sup..dagger.(.theta..sub.1)R.sub.{circumflex over (n)}.sup..dagger.(.theta..sub.2) . . . R.sub.{circumflex over (n)}.sup..dagger.(.theta..sub.N) to the plurality of secret receivers Bob #1 to Bob # N (Operation S400). In this case, the divided pieces of decryption key may be obtained by dividing the whole rotation angle of the decryption key with respect to the same rotation axis.
[0084] Subsequently, the secret generator Alice may transmit the encrypted quantum secret |S' to the secret verifier Charlie (Operation S500). Operation S400 and Operation S500 may be simultaneously performed or may be understood in reverse order.
[0085] A subsequent secret restoration process is as follows.
[0086] Each of the plurality of secret receivers Bob #1 to Bob # N meets the secret verifier Charlie while carrying a divided piece of decryption key R.sub.{circumflex over (n)}(.theta..sub.i) received from the secret generator Alice. The plurality of secret receivers Bob #1 to Bob # N restores the quantum secret |S by applying the divided piece of decryption key R.sub.{circumflex over (n)}(.theta..sub.i) to the encrypted quantum secret |S' of the secret verifier Charlie. This is represented by Equation 13 below.
R.sub.{circumflex over (n)}.sup..dagger.(.theta..sub.1)R.sub.{circumflex over (n)}.sup..dagger.(.theta..sub.2) . . . R.sub.{circumflex over (n)}.sup..dagger.(.theta..sub.N)|S'=R.sub.{circumflex over (n)}.sup..dagger.(.theta.)R.sub.{circumflex over (m)}.sup..dagger.(.phi.)R.sub.{circumflex over (n)}(.theta.)R.sub.{circumflex over (m)}(.phi.)|S=e.sup.i.epsilon.|S [Equation 13]
[0087] Meanwhile, in the descriptions of the quantum public-key cryptosystem, the quantum signature method, and the quantum secret sharing method according to exemplary embodiments of the present disclosure, communicators are basically communication devices which are connected to each other through a quantum channel and a public channel. The quantum channel is a communication channel which may transmit and receive photon signals, and the public channel is a communication channel which may transmit and receive electrical signals. In the quantum public-key cryptosystem, the quantum signature method, and the quantum secret sharing method according to exemplary embodiments of the present disclosure, a quantum state which is difficult to store or handle is not used as trap information, and quantum operator information rather than a quantum state is used as trapdoor information. Consequently, it is possible to solve problems that are difficult to solve in existing quantum cryptosystems. The quantum operator information is transmitted and received through the public channel.
[0088] According to an aspect of the present disclosure, a public-key cryptosystem may be provided in a quantum communication environment.
[0089] According to another aspect of the present disclosure, since quantum operator information rather than a quantum state which is difficult to store or handle is used as trap information, it is possible to ensure quantum stability and provide the same function as a trapdoor one-way function of current cryptography.
[0090] According to another aspect of the present disclosure, it is possible to use a single quantum state operator rather than a multidimensional quantum state operator, such as controlled not (CNOT), Quantum Fourier Transform, and Grover Iteration.
[0091] Effects of the present disclosure are not limited to those mentioned above, and other effects which have not been mentioned will be clearly understood by those of ordinary skill in the art from the above descriptions.
[0092] Although exemplary embodiments of the present disclosure have been described with reference to the accompanying drawings, those of ordinary skill in the art will appreciate that various modifications and equivalents may be made from the exemplary embodiments without departing from the technical spirit or essential characteristics of the present disclosure. Therefore, the above-described embodiments should be construed as illustrative rather than limiting in all aspects.
* * * * *
D00000

D00001

D00002

D00003

D00004

D00005

D00006

D00007

D00008

D00009

D00010

D00011

D00012

D00013

D00014
D00015


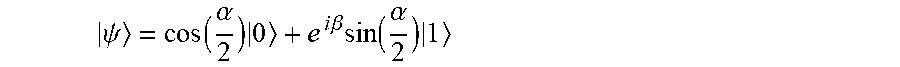






P00001

P00002
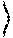
P00003

P00004
XML
uspto.report is an independent third-party trademark research tool that is not affiliated, endorsed, or sponsored by the United States Patent and Trademark Office (USPTO) or any other governmental organization. The information provided by uspto.report is based on publicly available data at the time of writing and is intended for informational purposes only.
While we strive to provide accurate and up-to-date information, we do not guarantee the accuracy, completeness, reliability, or suitability of the information displayed on this site. The use of this site is at your own risk. Any reliance you place on such information is therefore strictly at your own risk.
All official trademark data, including owner information, should be verified by visiting the official USPTO website at www.uspto.gov. This site is not intended to replace professional legal advice and should not be used as a substitute for consulting with a legal professional who is knowledgeable about trademark law.