Systems And Methods For Subscription Management Of Specific Classification Groups Based On User's Actions
KRAS; Greg ; et al.
U.S. patent application number 16/806459 was filed with the patent office on 2020-06-25 for systems and methods for subscription management of specific classification groups based on user's actions. The applicant listed for this patent is KnowBe4, Inc.. Invention is credited to Alin IRIMIE, Greg KRAS.
| Application Number | 20200204586 16/806459 |
| Document ID | / |
| Family ID | 59581586 |
| Filed Date | 2020-06-25 |
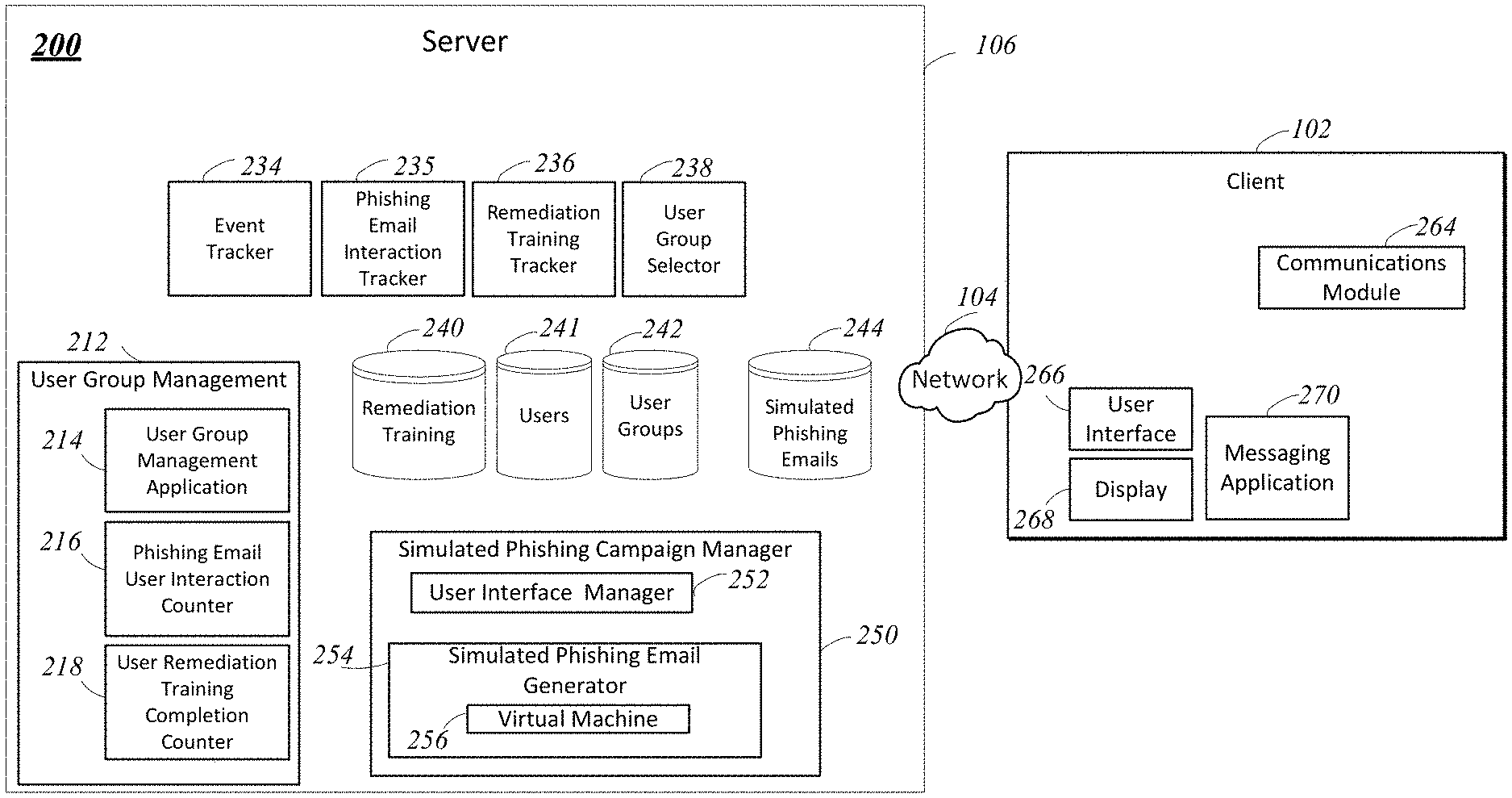









View All Diagrams
| United States Patent Application | 20200204586 |
| Kind Code | A1 |
| KRAS; Greg ; et al. | June 25, 2020 |
SYSTEMS AND METHODS FOR SUBSCRIPTION MANAGEMENT OF SPECIFIC CLASSIFICATION GROUPS BASED ON USER'S ACTIONS
Abstract
Embodiments of the disclosure describe systems and methods for selecting a first group of users, which is selected to receive simulated phishing emails as part of a simulated phishing campaign, and adding users to a second group of users based upon those selected users interacting with a simulated phishing email that is part of a simulated phishing campaign; tracking the completion of remediation training related to phishing emails by users in the second group of users and receiving one or more indications that the users in the second group of users have completed remedial training; and automatically adding users, who are members of the second user group, to the first user group, to a third user group, or to a predetermined user group responsive to the one or more indications that the users in the second group of users have completed remedial training.
| Inventors: | KRAS; Greg; (Dunedin, FL) ; IRIMIE; Alin; (Clearwater, FL) | ||||||||||
| Applicant: |
|
||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Family ID: | 59581586 | ||||||||||
| Appl. No.: | 16/806459 | ||||||||||
| Filed: | March 2, 2020 |
Related U.S. Patent Documents
| Application Number | Filing Date | Patent Number | ||
|---|---|---|---|---|
| 16220502 | Dec 14, 2018 | 10581911 | ||
| 16806459 | ||||
| 15904109 | Feb 23, 2018 | 10158668 | ||
| 16220502 | ||||
| 15674757 | Aug 11, 2017 | 9906555 | ||
| 15904109 | ||||
| 15481041 | Apr 6, 2017 | 9742803 | ||
| 15674757 | ||||
| Current U.S. Class: | 1/1 |
| Current CPC Class: | G06F 21/56 20130101; G06F 21/577 20130101; H04L 63/1483 20130101; H04L 63/1433 20130101; G06F 21/552 20130101 |
| International Class: | H04L 29/06 20060101 H04L029/06; G06F 21/55 20060101 G06F021/55; G06F 21/56 20060101 G06F021/56; G06F 21/57 20060101 G06F021/57 |
Claims
1. A method comprising: (a) receiving, by one or more processors coupled to memory, a first indication of a first user interaction associated with a simulated phishing communication to a user of a first user group of a plurality of user groups; (b) identifying, by the one or more processors, a category from a plurality of categories for the first user interaction, each of the plurality of categories associated with one or more interactions with one or more simulated phishing communications and mapped to at least one of the plurality of user groups; and (c) including, by the one or more processors, the user in a second user group of the plurality of user groups mapped to the category, and (d) communicating, by the one or more processors, a second simulated phishing communication to the user of the second user group.
2. The method of claim 1, wherein the first user interaction comprises a number of times the user interacted with simulated phishing communications.
3. The method of claim 2, wherein (b) further comprises identifying the category based as least on the number of times reaching a threshold.
4. The method of claim 1, wherein (b) further comprises classifying, by the one or more processors, the first user interaction into the category of a plurality of categories,
5. The method of claim 1, wherein (c) further comprises adding, by the one or more processors, the user to the second user group while keeping the user in the first user group.
6. The method of claim 1, wherein (c) further comprises adding, by the one or more processors, the user to the second user group while remover the user from the first user group.
7. A system comprising: one or more processors coupled to memory, and configured to: receive a first indication of a first user interaction associated with a simulated phishing communication to a user of a first user group of a plurality of user groups; identify a category from a plurality of categories for the first user interaction, each of the plurality of categories associated with one or more interactions with one or more simulated phishing communications and mapped to at least one of the plurality of user groups; and include the user in a second user group of the plurality of user groups mapped to the category, and communicate a second simulated phishing communication to the user of the second user group.
8. The system of claim 7, wherein the first user interaction comprises a number of times the user interacted with simulated phishing communications.
9. The system of claim 8, wherein the one or more processors are configured to identify the category based as least on the number of times reaching a threshold.
10. The system of claim 7, wherein the one or more processors are configured to classify the first user interaction into the category of a plurality of categories,
11. The system of claim 7, wherein the one or more processors are configured to add the user to the second user group while keeping the user in the first user group.
12. The system of claim 7, wherein the one or more processors are configured to add the user to the second user group while remover the user from the first user group.
13. A method comprising: (a) communicating, by one or more processors coupled to memory, a first simulated phishing communication to a user of a first user group of a plurality of users groups; (b) detecting, by the one or more processors, an event associated with the first simulated phishing communication to the user; (c) including, by the one or more processors, the user in a second user group of the plurality of user groups based at least on the event, and (d) communicating, by the one or more processors, a second simulated phishing communication to the user of the second user group.
14. The method of claim 13, wherein the event comp
D00000

D00001

D00002

D00003

D00004

D00005

D00006

D00007

D00008

D00009

D00010

D00011

D00012

XML
uspto.report is an independent third-party trademark research tool that is not affiliated, endorsed, or sponsored by the United States Patent and Trademark Office (USPTO) or any other governmental organization. The information provided by uspto.report is based on publicly available data at the time of writing and is intended for informational purposes only.
While we strive to provide accurate and up-to-date information, we do not guarantee the accuracy, completeness, reliability, or suitability of the information displayed on this site. The use of this site is at your own risk. Any reliance you place on such information is therefore strictly at your own risk.
All official trademark data, including owner information, should be verified by visiting the official USPTO website at www.uspto.gov. This site is not intended to replace professional legal advice and should not be used as a substitute for consulting with a legal professional who is knowledgeable about trademark law.