Asset Allocation And Reconciliation System
Bertot; German ; et al.
U.S. patent application number 15/794906 was filed with the patent office on 2019-04-04 for asset allocation and reconciliation system. The applicant listed for this patent is ServiceNow, Inc.. Invention is credited to German Bertot, Colby Blakeman.
| Application Number | 20190102849 15/794906 |
| Document ID | / |
| Family ID | 65896116 |
| Filed Date | 2019-04-04 |








View All Diagrams
| United States Patent Application | 20190102849 |
| Kind Code | A1 |
| Bertot; German ; et al. | April 4, 2019 |
ASSET ALLOCATION AND RECONCILIATION SYSTEM
Abstract
Systems and methods for a software asset management, license compliance, and reconciliation techniques are disclosed. Software licenses come in many different types, including but not limited to, subscription based licenses, geographically restricted licenses, globally available licenses, production only licenses, standard shrink wrap licenses, network concurrent usage licenses, etc. With fewer applications being installed directly onto end-users machines, tools that only scan local networks and search hard drives are becoming less effective. Disclosed techniques introduce additional capabilities for software asset discovery, tracking, license allocation, and other functions as part of a comprehensive software asset reconciliation engine. For example, the disclosed software asset reconciliation engine may be configured with sub-engines to perform groupings of discovered information to allow system administrators and license administrators to properly allocate and monitor software application usage across an enterprise and ensure compliance against a purchased inventory of licenses of different types.
| Inventors: | Bertot; German; (San Carlos, CA) ; Blakeman; Colby; (San Jose, CA) | ||||||||||
| Applicant: |
|
||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Family ID: | 65896116 | ||||||||||
| Appl. No.: | 15/794906 | ||||||||||
| Filed: | October 26, 2017 |
Related U.S. Patent Documents
| Application Number | Filing Date | Patent Number | ||
|---|---|---|---|---|
| 62568087 | Oct 4, 2017 | |||
| Current U.S. Class: | 1/1 |
| Current CPC Class: | G06Q 30/0603 20130101; G06F 21/577 20130101; G06Q 30/018 20130101; G06F 16/951 20190101; H04L 41/0803 20130101; H04L 63/1433 20130101; H04L 67/34 20130101; G06F 3/0482 20130101; H04L 41/0859 20130101; H04L 41/22 20130101; G06F 16/27 20190101; H04L 41/0893 20130101; H04L 67/26 20130101; G06Q 10/06314 20130101; G06F 11/3452 20130101; G06F 9/451 20180201; G06F 9/461 20130101; G06F 9/5038 20130101; G06F 9/547 20130101; G06F 11/3006 20130101; G06F 21/53 20130101; H04L 67/32 20130101; G06Q 10/06315 20130101; G06Q 10/06393 20130101; G06F 3/0484 20130101; H04L 41/12 20130101; G06F 40/18 20200101; H04L 63/20 20130101; G06Q 30/0641 20130101; H04L 63/10 20130101; G06F 16/24578 20190101; H04L 67/12 20130101; G06Q 50/184 20130101; G06Q 30/0635 20130101; G06Q 40/12 20131203; H04L 43/08 20130101; G06F 9/4881 20130101; G06F 11/14 20130101; H04L 41/0879 20130101; H04L 43/045 20130101; H04L 43/50 20130101; H04L 41/0843 20130101; G06F 40/186 20200101; G06F 16/30 20190101; G06F 3/0481 20130101; G06F 3/04847 20130101; G06F 16/904 20190101; G06Q 10/067 20130101; G06F 16/2423 20190101; G06F 9/44505 20130101; G06Q 10/0635 20130101; G06F 3/0486 20130101; G06F 16/248 20190101 |
| International Class: | G06Q 50/18 20060101 G06Q050/18; G06Q 30/00 20060101 G06Q030/00; G06Q 10/06 20060101 G06Q010/06 |
Claims
1. A cloud-based computer system, comprising: a memory partition; a network interface communicatively coupled to one or more processing units and the memory partition, wherein the memory partition comprises computer instructions that when executed by the one or more processing units cause the cloud-based computer system to: initiate a probe of one or more computer systems of an enterprise, the probes configured to determine software application usage statistics for each of the one or more computer systems, the software application usage statistics comprising information for identifying compliance with license requirements for software applications corresponding to the application usage statistics; obtain license information identifying software application license availability across the one or more computer systems of the enterprise; correlate the software application usage statistics with a first grouping selected from at least one of a department of the business, business unit of the enterprise, cost center of the enterprise, and a country of use; prepare a compliance report indicating discrepancies between the software application usage statistics and the software application license availability, the compliance report including information about the country of use for at least one software application having license information indicating a restriction of use based on country; and identify a plurality of remediation options available for non-compliant usage of at least one of the software applications, the remediation options including purchase rights and at least one of: creating allocations, removing allocations, removing unallocated installations, and removing unlicensed installations.
2. The cloud-based computer system of claim 1, wherein the compliance report provides information restricted based on an identified publisher or set of publishers.
3. The cloud-based computer system of claim 1, further comprising instructions to cause the cloud-based computer system to: correlate the software application usage statistics with a subgrouping different from the first grouping and selected from at least one of a department of the business, business unit of the enterprise, cost center of the enterprise, and a country of use.
4. The cloud-based computer system of claim 3, further comprising instructions to cause the cloud-based computer system to: apply a right of entitlement only to users or devices that have a software installation and match the first grouping and the subgrouping as defined in the right of entitlement.
5. The cloud-based computer system of claim 4, wherein the requirement of matching the subgrouping increases a number of dimensions that must be matched between the user or device prior to applying the right of entitlement.
6. The cloud-based computer system of claim 4, wherein users or devices that have a software installation and do not match the first grouping and the subgrouping as defined in the right of entitlement are considered unlicensed installations.
7. The cloud-based computer system of claim 1, wherein the compliance report comprises a true-up cost to correct for at least one identified discrepancy.
8. The cloud-based computer system of claim 1, wherein the software application usage statistics identify use of a subscription based software application.
9. A cloud-based computer system, comprising: a memory partition; a network interface communicatively coupled to one or more processing units and the memory partition, wherein the memory partition comprises computer instructions that when executed by the one or more processing units cause the cloud-based computer system to: obtain information describing attributes of one or more computer systems of an enterprise, the attributes identifying software application usage statistics for each of the one or more computer systems, the software application usage statistics comprising information for identifying compliance with license requirements for software applications corresponding to the application usage statistics; obtain license information identifying software application license availability across the one or more computer systems of the enterprise; correlate the software application usage statistics with a first grouping selected from at least one of a department of the business, business unit of the enterprise, cost center of the enterprise, and a country of use; correlate the software application usage statistics with a subgroup selected from at least one of a department of the business, business unit of the enterprise, cost center of the enterprise, and a country of use, wherein the subgroup is different from the first grouping; prepare a compliance report indicating discrepancies between the software application usage statistics and the software application license availability, the compliance report including information pertaining to users or devices not matching the first grouping and the subgrouping as defined in the license information; and identify a plurality of remediation options available for non-compliant usage of at least one of the software applications, the remediation options including purchase rights and at least one of: creating allocations, removing allocations, removing unallocated installations, and removing unlicensed installations.
10. The cloud-based computer system of claim 9, wherein the compliance report comprises a true-up cost to correct for at least one identified discrepancy.
11. The cloud-based computer system of claim 9, wherein users or devices that have a software installation and do not match the first grouping and the subgrouping as defined in the license information are considered unlicensed installations.
12. The cloud-based computer system of claim 9, wherein the compliance report provides information restricted based on an identified publisher or set of publishers.
13. The cloud-based computer system of claim 9, wherein the compliance report comprises information regarding potential upgrades of software applications identified in the software application usage statistics to address at least one identified discrepancy.
14. The cloud-based computer system of claim 9, wherein a global right of entitlement may be applied during correlation and considered to match any value of the first grouping or the subgroup.
15. A non-transitory computer readable medium storing instructions that when executed by a processor cause the processor to configure a computer system to: obtain information describing attributes of one or more computer systems of an enterprise, the attributes identifying software application usage statistics for each of the one or more computer systems, the software application usage statistics comprising information for identifying compliance with license requirements for software applications corresponding to the application usage statistics; obtain license information identifying software application license availability across the one or more computer systems of the enterprise; correlate the software application usage statistics with a first grouping selected from at least one of a department of the business, business unit of the enterprise, cost center of the enterprise, and a country of use; correlate the software application usage statistics with a subgroup selected from at least one of a department of the business, business unit of the enterprise, cost center of the enterprise, and a country of use, wherein the subgroup is different from the first grouping; prepare a compliance report indicating discrepancies between the software application usage statistics and the software application license availability, the compliance report including information pertaining to users or devices not matching the first grouping and the subgrouping as defined in the license information; and identify a plurality of remediation options available for non-compliant usage of at least one of the software applications, the remediation options including purchase rights and at least one of: creating allocations, removing allocations, removing unallocated installations, and removing unlicensed installations.
16. The non-transitory computer readable medium of claim 15, wherein the compliance report comprises a true-up cost to correct for at least one identified discrepancy.
17. The non-transitory computer readable medium of claim 15, wherein users or devices that have a software installation and do not match the first grouping and the subgrouping as defined in the license information are considered unlicensed installations.
18. The non-transitory computer readable medium of claim 15, wherein the compliance report provides information restricted based on an identified publisher or set of publishers.
19. The non-transitory computer readable medium of claim 15, wherein the compliance report comprises information regarding potential upgrades of software applications identified in the software application usage statistics to address at least one identified discrepancy.
20. The non-transitory computer readable medium of claim 15, wherein a global right of entitlement may be applied during correlation and considered to match any value of the first grouping or the subgroup.
Description
RELATED CASES
[0001] This application claims priority to and benefit of U.S. Provisional Patent Application Ser. 62/568,087, filed Oct. 4, 2017, entitled "Platform Computing Environment and Functionality thereof," by Amradkar, et. al, for all applicable purposes, including a right of priority, the contents of which are incorporated by reference herein, in their entirety.
TECHNICAL FIELD
[0002] Embodiments described herein generally relate to enterprise computing and, in particular, to providing a software license management, compliance, and reconciliation system. In today's enterprise systems there may be a mix of cloud-based, traditional hardware, traditional software, and subscription based software application installations. Disclosed techniques address proper discovery, management of allocations, and compliance requirements for software installation and license management across such hybrid systems.
BACKGROUND
[0003] Cloud computing relates to the sharing of computing resources that are generally accessed via the Internet. In particular, cloud computing infrastructure allows users to access a shared pool of computing resources, such as servers, storage devices, networks, applications, and/or other computing-based services. By doing so, users, such as individuals and/or enterprises, are able to access computing resources on demand that are located at remote locations in order to perform a variety of computing functions that include storing and/or processing computing data. For enterprise and other organization users, cloud computing provides flexibility in accessing cloud computing resources without accruing up-front costs, such as purchasing network equipment and investing time in establishing a private network infrastructure. Instead, by utilizing cloud computing resources, users are able redirect their resources to focus on core business functions.
[0004] In today's communication networks, examples of cloud computing services a user may utilize include software as a service (SaaS) and platform as a service (PaaS) technologies. SaaS is a delivery model that provides software as a service rather than an end product. Instead of utilizing local network or individual software installations, software is typically licensed on a subscription basis, hosted on a remote machine, and accessed as needed. For example, users are generally able to access a variety of business and/or information technology (IT) related software via a web browser. PaaS acts as an extension of SaaS that goes beyond providing software services by offering customizability and expandability features to meet a user's needs. For example, PaaS can provide a cloud-based developmental platform for users to develop, modify, and/or customize applications and/or automate business operations without maintaining network infrastructure and/or allocating computing resources normally associated with these functions.
[0005] Within the context of cloud computing solutions, software license management and compliance reporting may be complicated. Enterprise's may consist of traditional hardware infrastructure maintained by an internal information technology staff with local software application installations, cloud-based pay for use applications (e.g., SaaS), cloud-based or mainframe based pay for use software, and subscription web-based applications, among other possibilities. Disclosed techniques for a software compliance, discovery, and management system address many of the issues encountered in such a hybrid environment and allow customization capabilities for increased flexibility to insure compliance with license requirements. Additionally, disclosed techniques help to identify improper allocations of software licenses, identify improper installations of software, ensure adherence to geographical licensing restrictions, and compliance with other license management requirements for enterprise solutions.
BRIEF DESCRIPTION OF DRAWINGS
[0006] For a more complete understanding of this disclosure, reference is now made to the following brief description, taken in connection with the accompanying drawings and detailed description, wherein like reference numerals represent like parts.
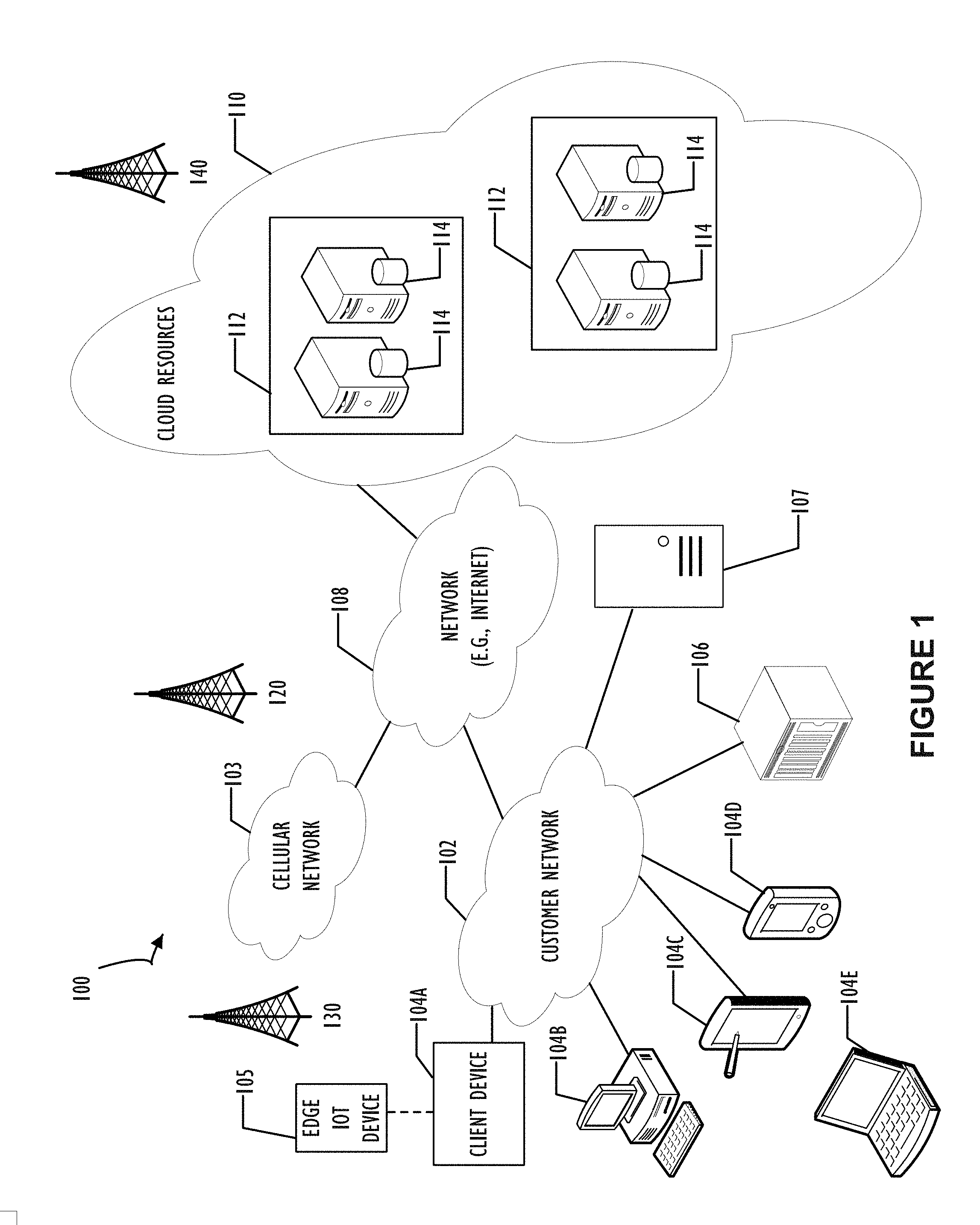
[0007] FIG. 1 illustrates a block diagram of an embodiment of a cloud computing infrastructure 100 where embodiments of the present disclosure may operate.
[0008] FIG. 2 illustrates a block diagram of an embodiment of a multi-instance cloud architecture 200 where embodiments of the present disclosure may operate.
[0009] FIG. 3 illustrates a block diagram 300 depicting a possible reconciliation framework including multiple engines and sub-engines (e.g., operational units) that may be used to configure a system for software license monitoring and management according to the present disclosure.
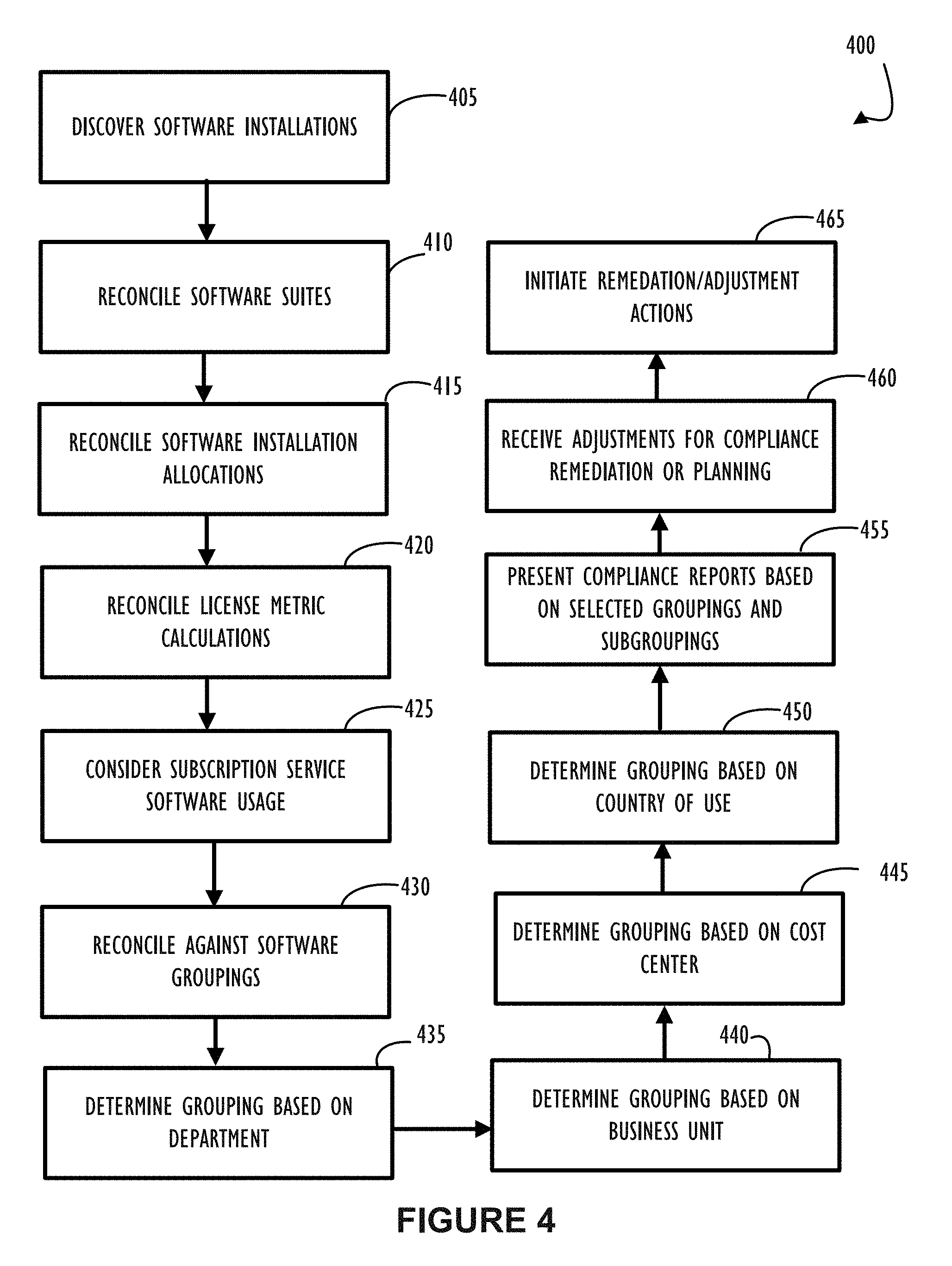
[0010] FIG. 4 illustrates a flow chart 400 explaining possible steps to automate a process of software license discovery, reconciliation, and remediation as may be implemented in one or more disclosed embodiments of a system for license monitoring and management.
[0011] FIG. 5 illustrates a screen shot 500 of an example interface screen as may be shown to an end-user defining parameters of a software entitlement (e.g., license set) according to one or more disclosed embodiments.
[0012] FIG. 6 illustrates a screen shot 600 of an example interface screen as may be shown to an end-user defining a custom license metric according to one or more disclosed embodiments.
[0013] FIG. 7 illustrates a screen shot 700 of an example interface screen as may be shown to an end-user viewing a set of software entitlements and their high-level properties representing multiple license agreements (e.g., for an enterprise or corporation) according to one or more disclosed embodiments.
[0014] FIG. 8 illustrates a screen shot 800 of an example interface screen as may be shown to an end-user monitoring compliance of a Processor Value Unit (PVU) sub-capacity license model according to one or more disclosed embodiments.
[0015] FIG. 9 illustrates a screen shot 900 of an example interface screen as may be shown to an end-user defining parameters for a compliance report, generated as a step in reconciliation, according to one or more disclosed embodiments.
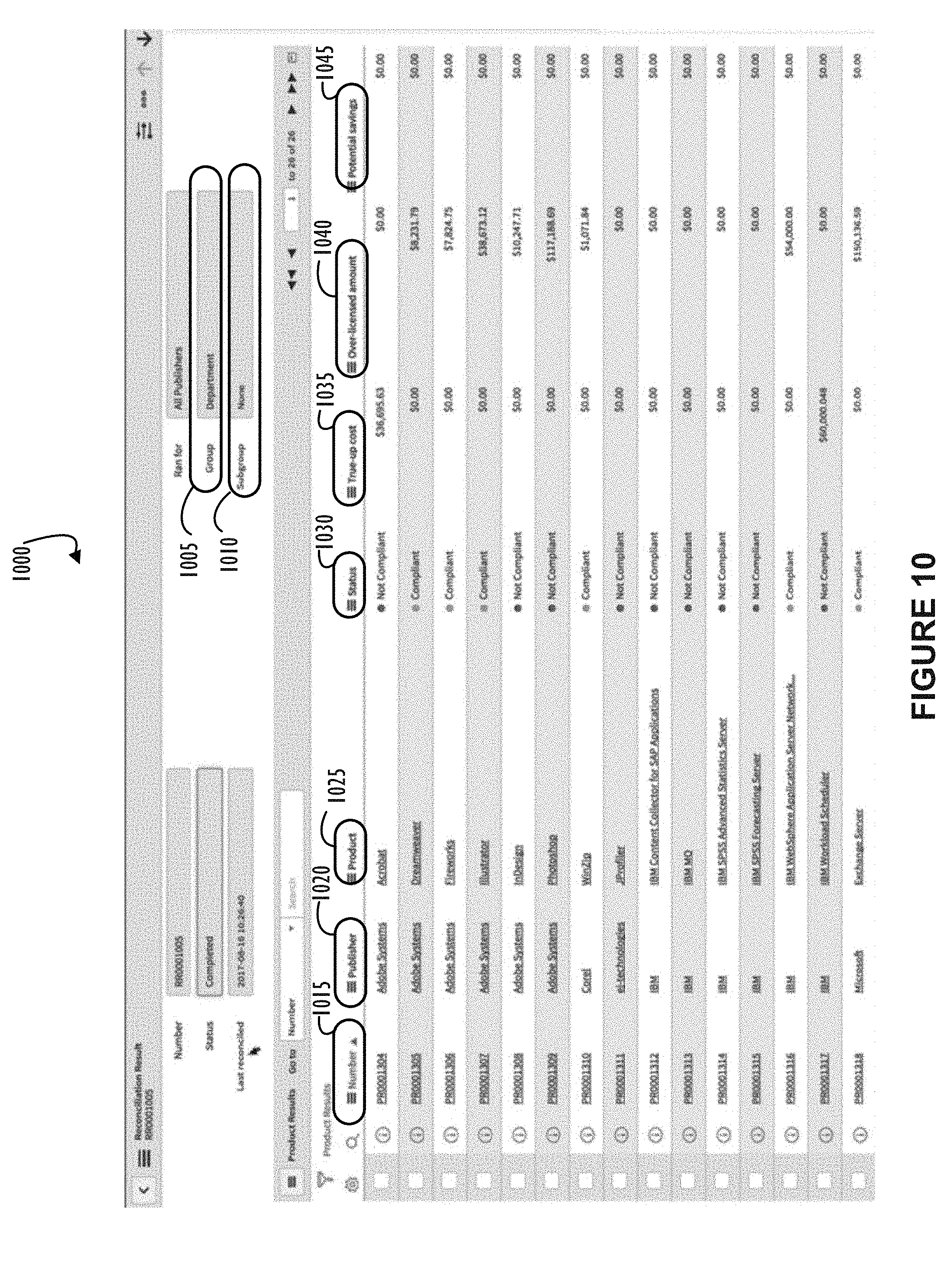
[0016] FIG. 10 illustrates a screen shot 1000 of an example interface screen as may be shown to an end-user viewing reconciliation results according to one or more disclosed embodiments.
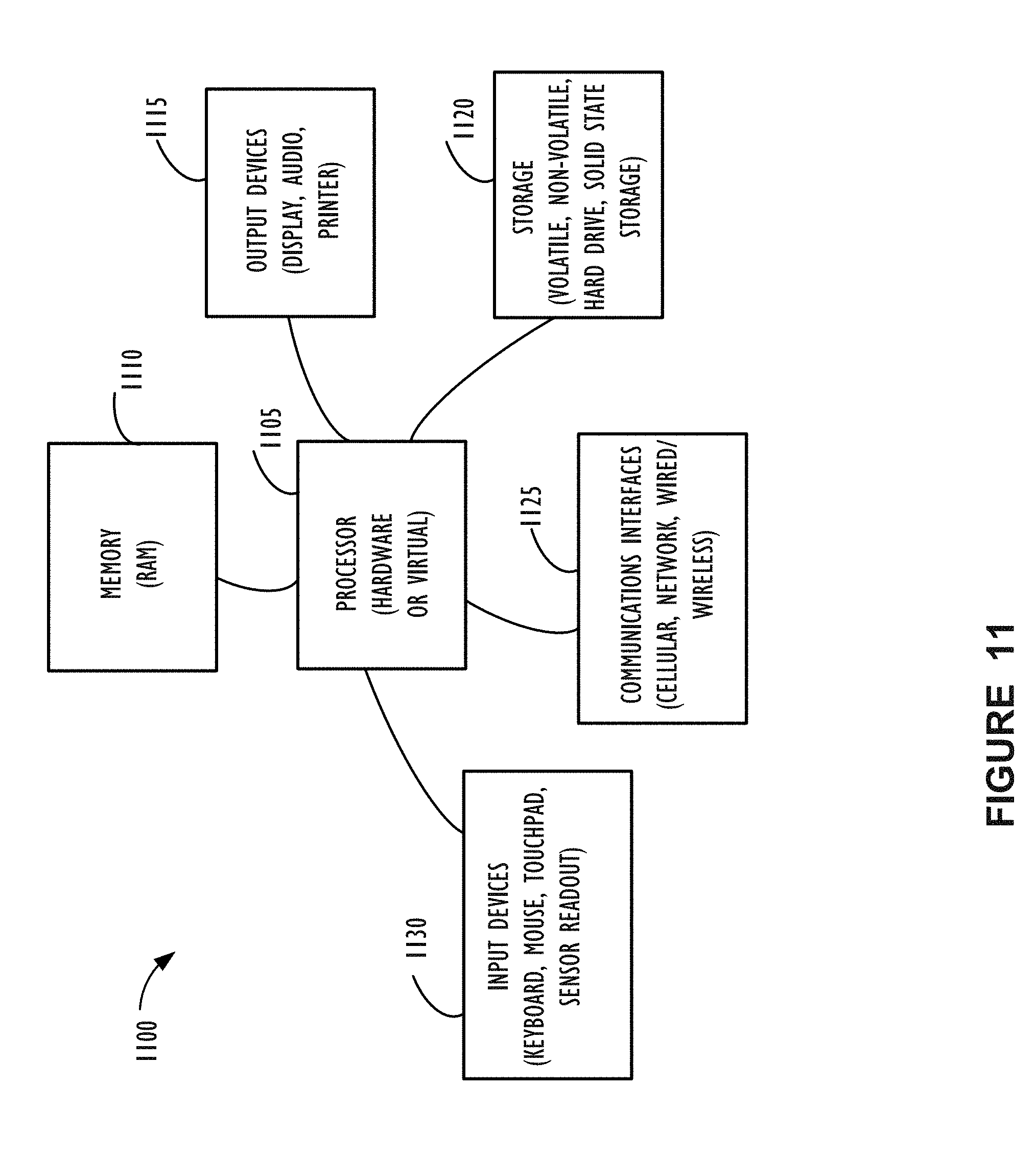
[0017] FIG. 11 illustrates a high-level block diagram 1100 of a processing device (computing system) that may be used to implement one or more disclosed embodiments.
DESCRIPTION OF EMBODIMENTS
[0018] In the following description, for purposes of explanation, numerous specific details are set forth in order to provide a thorough understanding of the embodiments disclosed herein. It will be apparent, however, to one skilled in the art that the disclosed embodiments may be practiced without these specific details. In other instances, structure and devices are shown in block diagram form in order to avoid obscuring the disclosed embodiments. Moreover, the language used in this disclosure has been principally selected for readability and instructional purposes, and may not have been selected to delineate or circumscribe the inventive subject matter, resorting to the claims being necessary to determine such inventive subject matter. Reference in the specification to "one embodiment" or to "an embodiment" means that a particular feature, structure, or characteristic described in connection with the embodiments is included in at least one embodiment.
[0019] The terms "a," "an," and "the" are not intended to refer to a singular entity unless explicitly so defined, but include the general class of which a specific example may be used for illustration. The use of the terms "a" or "an" may therefore mean any number that is at least one, including "one," "one or more," "at least one," and "one or more than one." The term "or" means any of the alternatives and any combination of the alternatives, including all of the alternatives, unless the alternatives are explicitly indicated as mutually exclusive. The phrase "at least one of" when combined with a list of items, means a single item from the list or any combination of items in the list. The phrase does not require all of the listed items unless explicitly so defined.
[0020] The term "computing system" is generally taken to refer to at least one electronic computing device that includes, but is not limited to, a single computer, virtual machine, virtual container, host, server, laptop, and/or mobile device or to a plurality of electronic computing devices working together to perform the function described as being performed on or by the computing system.
[0021] As used herein, the term "medium" refers to one or more non-transitory physical media that together store the contents described as being stored thereon. Embodiments may include non-volatile secondary storage, read-only memory (ROM), and/or random-access memory (RAM).
[0022] As used herein, the terms "application" and "function" refer to one or more computing modules, programs, processes, workloads, threads and/or a set of computing instructions executed by a computing system. Example embodiments of applications and functions include software modules, software objects, software instances and/or other types of executable code.
[0023] Software licenses represent legal contracts between a software vendor (sometimes referred to as a software publisher) and a purchaser of the associated software application(s). Often, the contract is between the software vendor and a corporation or enterprise for use by their employees as end-users. In some cases, software licenses are referred to as software "entitlements," in part, because they entitle a corporation to utilize a number of copies of software across their enterprise. Terms of software licenses vary greatly and generally depend on a type of use for applications subject to a particular license. In a simple case, a software license allows specific corporate employees to use a specific software application for an undefined length of time after a single payment. Sometimes, this may be referred to as a named-user shrink wrap license. In what may be considered the simplest case, when a named-user restriction is not present the software license may simply be referred to as a shrink wrap license. Many more complicated variations of software licenses, in the form of entitlements, exist and generally describe restrictions on how a particular application may be used. Restrictions include, but are not restricted to, use over a network by a concurrent number of users (referred to as a floating license or a network license), use for a specific time period over the Internet (referred to as a subscription based license), use of a particular application on a particular server (referred to as a node locked license), use of a set of applications that are not individually licensed (referred to as an application suite license), and even Processor Value Unit sub-capacity licensing (where a portion of a processor's total capacity is licensed). There are simply too many variations to list each model as an example. However, in the majority of cases there exist common elements regarding the restrictions imposed on the purchaser or licensee. Enterprises must adhere to all applicable restrictions to be in compliance with their vendor's software license terms. Compliance is important because being out of compliance may result in substantial fines or other penalties.
[0024] License enforcement methods used by software vendors vary greatly and industry trends change over time. Some methods completely lock down a system and prevent unlicensed software from loading. Other systems allow software to execute, possibly in a degraded operational state, when out of compliance. Some vendors rely on a paper license with no automatic enforcement. This disclosure includes embodiments to cover all current and possibly future cases, in part, by allowing customization capabilities discussed later. When a company runs in a non-compliant environment a "true-up" cost may be calculated. The true-up cost represents an additional cost (paid by the corporation to the software vendor) to purchase enough additional licenses to correct non-compliance issues (with or without additional fees or penalties). Purchasing additional licenses (e.g., rights or entitlements) is one remediation option. Other remediation options are discussed throughout this disclosure. Some disclosed embodiments recognize a plurality of remediation options and allow a software license administrator (corporation employee) to adjust an enterprise's allocations to regain a compliant environment. In some cases, compliance may be achieved without purchasing anything new. Obviously, these cases result in bottom line savings for the enterprise. Metrics made available in compliance reports may also assist an enterprise or corporation with future budget planning. Planning may be assisted by the system because identification of non-compliant (or fully allocated) software may indicate a future purchase requirement at the corporate, enterprise, cost center, or country level. Also, some cases may not allow simple re-allocation of licenses. For example, existing licenses may be restricted by country or may not match requirements for desired use of the software application(s). In this case, an enterprise may need to interface with the software vendor to trade their excess licenses of one type and acquire more appropriate licenses. Again, the enterprise or corporation may save money because the software vendor may give a credit toward new licenses if other licenses are relinquished. Disclosed embodiments also include reports that allow visibility into an enterprise's actual needs and may assist in making business decisions regarding software use across the corporation or enterprise.
[0025] Restrictions appearing in software licenses have some common attributes. Restrictions, at a very high level, may be thought of as placing a limit on user, location, duration, amount, etc. for a specific application (or suite). Each software application may have its own restrictions imposed and these restrictions may change over time. Reasons for change may include, but not be limited to: enterprise growth; changes in usage patterns; re-negotiation of license terms; availability of new or different applications; end of life of applications; and technological or business factors.
[0026] It is clear from the discussion above that management of software entitlements (licenses) for a corporation may be complicated. Systems have been built to assist in managing compliance and identifying methods to regain compliance once a non-compliance has been identified. Regaining of compliance may be referred to as "reconciliation" and may require one or more "remediation" operations to achieve. Existing systems have limitations in their ability to flexibly manage the vast variety of restrictions appearing in license contracts. Particularly, flexibility is needed with respect to discovery of virtual, subscription, global, and cloud-based applications. To address these and other issues, this disclosure presents several embodiments of systems designed to handle new methods of grouping, tracking, discovering, and applying defined restrictions to software applications in use by a corporation. Disclosed embodiments include the ability to assign departments, cost centers, locations, and other groups to Software Entitlements so that rights may be accordingly assigned to the correct group during reconciliation. Disclosed systems also offer a variety of remediation options previously unavailable to assist software license managers in their goal of running within a compliant system and quickly performing reconciliation to address any non-compliance issues.
[0027] In some disclosed embodiments, a system has the ability to track any number of attributes and associate them with software applications and their licenses. Tracking at the level of department, country, cost center, company within organization (e.g., subsidiary), may all be important aspects to ensure compliance. These same four attributes may be tracked on individual software installations so as discovery runs and identifies that a user has a software application (in one example a particular version of an application), those attributes may be tied to that particular installation. When software reconciliation is performed, calculations across a plurality of engines may be performed and their results correlated to consider a compliance position. Group attributes may also be considered so that rights are properly applied. If, for example, rights are purchased for a particular department, users only in that department are part of the allocation of those rights. Similarly, if rights are purchased for a particular country, software application licenses will only be allocated where the user or device exists in that country. The disclosed reconciliation framework also supports global entitlements, rights that have been purchased across any department, cost center, company. Further, multiple subgroup classifications may be performed. For example a compliance report may be generated that sorts by country and then by department.
[0028] In addition to the grouping reconciliation noted above, some embodiments include an ability to define a custom license metric calculation. Custom license metric calculation represents the ability for customers to enter a custom script or program that defines how to calculate the number of rights that need to be applied to a software installation or a set of software installations. For example, as part of discovery process. Then, when reconciliation runs information identified by any custom script or program may be included in the overall reconciliation logic. In this manner, anything that the customer has decided may be important to track may be maintained and utilized across the entire reconciliation framework.
[0029] Publisher specific discovery plugins (e.g., IBM or VMWARE) may also be applied. Publisher specific discovery plugins may be provided by software vendors or as part of the reconciliation framework for popular vendors as needed. In yet another example, a software vendor's raw inventory feed may be processed by the reconciliation framework. A software vendor's raw feed may be data maintained as part of applications monitoring their own license status (e.g., license file information, run-time license checking, license server information, etc.). Subscription services may also be discovered and monitored via specialization logic implemented as either a custom script of publisher specific add-on. Subscription based monitoring for compliance has special factors to consider because often the use is on-line across a network and there may be very little software installation foot print or other usage information by which to track subscription software and perform reconciliation.
[0030] A discovery map, as used in this disclosure, refers to a configuration or rules file that provides information about attributes of one or more software applications. The information from a discovery map may be used as part of discovery to aid in proper application of rights as part of reconciliation. An attribute referred to as an "installation consideration" may be also tracked as an attribute of each discovered software application installation. For example, the "installation consideration" may define an installation as part of a system used for testing or disaster recovery backup. This attribute may be important because some software agreements count only production use. In these cases, any test or disaster recovery backup site need not be monitored for compliance. Accordingly, added attributes for each software installation may be used to further refine how information from each identified software installation is tracked for compliance. Further information about a reconciliation framework to ensure license compliance is discussed below with reference to FIGS. 3-10.
[0031] FIG. 1 illustrates a block diagram of an embodiment of a cloud computing infrastructure 100 where embodiments of the present disclosure may operate. Cloud computing infrastructure 100 comprises a customer network 102, network 108, and a cloud resources platform/network 110. In one embodiment, the customer network 102 may be a local private network, such as local area network (LAN) that includes a variety of network devices that include, but are not limited to switches, servers, and routers. Each of these networks can contain wired or wireless programmable devices and operate using any number of network protocols (e.g., TCP/IP) and connection technologies (e.g., WiFi.RTM. networks, Bluetooth.RTM.). Wi-Fi is a registered trademark of the Wi-Fi Alliance. Bluetooth is a registered trademark of Bluetooth Special Interest Group. In another embodiment, customer network 102 represents an enterprise network that could include or be communicatively coupled to one or more local area networks (LANs), virtual networks, data centers, and/or other remote networks (e.g., 108, 112). As shown in FIG. 1, customer network 102 may be connected to one or more client devices 104A-E and allow the client devices to communicate with each other and/or with cloud resources platform/network 110. Client devices 104A-E may be computing systems such as desktop computer 104B, tablet computer 104C, mobile phone 104D, laptop computer (shown as wireless) 104E, and/or other types of computing systems generically shown as client device 104A. Cloud computing infrastructure 100 may also include other types of devices generally referred to as Internet of Things (IoT) (e.g., edge IOT device 105) that may be configured to send and receive information via a network to access cloud computing services or interact with a remote web browser application (e.g., to receive configuration information). FIG. 1 also illustrates that customer network 102 may be connected to a local compute resource 106 that may include a server, access point, router, or other device configured to provide for local computational resources and/or to facilitate communication amongst networks and devices. For example, local compute resource 106 may be one or more physical local hardware devices configured to communicate with wireless network devices and/or facilitate communication of data between customer network 102 and other networks such as network 108 and cloud resources platform/network 110. Local compute resource 106 may also facilitate communication between other external applications, data sources, and services, and customer network 102. FIG. 1 also illustrates that customer network 102 may be connected to a computer configured to execute a management, instrumentation, and discovery (MID) server 107. For example, MID server 107 may be a Java application that runs as a Windows service or UNIX daemon. MID server 107 may be configured to assist functions such as, but not necessarily limited to, discovery, orchestration, service mapping, service analytics, and event management. MID server 107 may be configured to perform tasks for a cloud-based instance while never initiating communication directly to the cloud-instance by utilizing a work queue architecture. This configuration may assist in addressing security concerns by eliminating that path of direct communication initiation.
[0032] Cloud computing infrastructure 100 also includes cellular network 103 for use with mobile communication devices. Mobile cellular networks support mobile phones and many other types of mobile devices such as laptops etc. Mobile devices in cloud computing infrastructure 100 are illustrated as mobile phone 104D, laptop 104E, and tablet 104C. A mobile device such as mobile phone 104D may interact with one or more mobile provider networks as the mobile device moves, typically interacting with a plurality of mobile network towers 120, 130, and 140 for connecting to the cellular network 103. Although referred to as a cellular network in FIG. 1, a mobile device may interact with towers of more than one provider network, as well as with multiple non-cellular devices, such as wireless access points and routers (e.g., local compute resource 106). In addition, the mobile devices may interact with other mobile devices or with non-mobile devices such as desktop computer 104B and various types of client devices 104A for desired services. Although not specifically illustrated in FIG. 1, customer network 102 may also include a dedicated network device (e.g., gateway or router) or a combination of network devices that implement a customer firewall or intrusion protection system.
[0033] FIG. 1 illustrates that customer network 102 is coupled to a network 108. Network 108 may include one or more computing networks available today, such as other LANs, wide area networks (WANs), the Internet, and/or other remote networks, in order to transfer data between client devices 104A-E and cloud resources platform/network 110. Each of the computing networks within network 108 may contain wired and/or wireless programmable devices that operate in the electrical and/or optical domain. For example, network 108 may include wireless networks, such as cellular networks in addition to cellular network 103. Wireless networks may utilize a variety of protocols and communication techniques (e.g., Global System for Mobile Communications (GSM) based cellular network) wireless fidelity Wi-Fi networks, Bluetooth, Near Field Communication (NFC), and/or other suitable radio-based networks as would be appreciated by one of ordinary skill in the art upon viewing this disclosure. Network 108 may also employ any number of network communication protocols, such as Transmission Control Protocol (TCP) and Internet Protocol (IP). Although not explicitly shown in FIG. 1, network 108 may include a variety of network devices, such as servers, routers, network switches, and/or other network hardware devices configured to transport data over networks.
[0034] In FIG. 1, cloud resources platform/network 110 is illustrated as a remote network (e.g., a cloud network) that is able to communicate with client devices 104A-E via customer network 102 and network 108. The cloud resources platform/network 110 acts as a platform that provides additional computing resources to the client devices 104A-E and/or customer network 102. For example, by utilizing the cloud resources platform/network 110, users of client devices 104A-E may be able to build and execute applications, such as automated processes for various business, IT, and/or other organization-related functions. In one embodiment, the cloud resources platform/network 110 includes one or more data centers 112, where each data center 112 could correspond to a different geographic location. Within a particular data center 112 a cloud service provider may include a plurality of server instances 114. Each server instance 114 may be implemented on a physical computing system, such as a single electronic computing device (e.g., a single physical hardware server) or could be in the form a multi-computing device (e.g., multiple physical hardware servers). Examples of server instances 114 include, but are not limited to, a web server instance (e.g., a unitary Apache installation), an application server instance (e.g., unitary Java Virtual Machine), and/or a database server instance (e.g., a unitary MySQL catalog).
[0035] To utilize computing resources within cloud resources platform/network 110, network operators may choose to configure data centers 112 using a variety of computing infrastructures. In one embodiment, one or more of data centers 112 are configured using a multi-tenant cloud architecture such that a single server instance 114, which can also be referred to as an application instance, handles requests and serves more than one customer. In some cases, data centers with multi-tenant cloud architecture commingle and store data from multiple customers, where multiple customer instances are assigned to a single server instance 114. In a multi-tenant cloud architecture, the single server instance 114 distinguishes between and segregates data and other information of the various customers. For example, a multi-tenant cloud architecture could assign a particular identifier for each customer in order to identify and segregate the data from each customer. In a multitenancy environment, multiple customers share the same application, running on the same operating system, on the same hardware, with the same data-storage mechanism. The distinction between the customers is achieved during application design, thus customers do not share or see each other's data. This is different than virtualization where components are transformed, enabling each customer application to appear to run on a separate virtual machine. Generally, implementing a multi-tenant cloud architecture may have a production limitation, such as the failure of a single server instance 114 causing outages for all customers allocated to the single server instance 114.
[0036] In another embodiment, one or more of the data centers 112 are configured using a multi-instance cloud architecture to provide every customer its own unique customer instance. For example, a multi-instance cloud architecture could provide each customer instance with its own dedicated application server and dedicated database server. In other examples, the multi-instance cloud architecture could deploy a single server instance 114 and/or other combinations of server instances 114, such as one or more dedicated web server instances, one or more dedicated application server instances, and one or more database server instances, for each customer instance. In a multi-instance cloud architecture, multiple customer instances could be installed on a single physical hardware server where each customer instance is allocated certain portions of the physical server resources, such as computing memory, storage, and processing power. By doing so, each customer instance has its own unique software stack that provides the benefit of data isolation, relatively less downtime for customers to access the cloud resources platform/network 110, and customer-driven upgrade schedules. An example of implementing a customer instance within a multi-instance cloud architecture will be discussed in more detail below when describing FIG. 2.
[0037] FIG. 2 illustrates a block diagram of an embodiment of a multi-instance cloud architecture 200 where embodiments of the present disclosure may operate. FIG. 2 illustrates that the multi-instance cloud architecture 200 includes a customer network 202 that connects to two data centers 206A and 206B via network 204. Customer network 202 and network 204 may be substantially similar to customer network 102 and network 108 as described in FIG. 1, respectively. Data centers 206A and 206B can correspond to FIG. 1's data centers 112 located within cloud resources platform/network 110. Using FIG. 2 as an example, a customer instance 208 is composed of four dedicated application server instances 210A-210D and two dedicated database server instances 212A and 212B. Stated another way, the application server instances 210A-210D and database server instances 212A and 212B are not shared with other customer instances 208. Other embodiments of the multi-instance cloud architecture 200 could include other types of dedicated server instances, such as a web server instance. For example, the customer instance 208 could include the four dedicated application server instances 210A-210D, two dedicated database server instances 212A and 212B, and four dedicated web server instances (not shown in FIG. 2).
[0038] To facilitate higher availability of the customer instance 208, application server instances 210A-210D and database server instances 212A and 212B are shown to be allocated to two different data centers 206A and 206B, where one of data centers 206A and 206B may act as a backup data center. In reference to FIG. 2, data center 206A acts as a primary data center that includes a primary pair of application server instances 210A and 210B and primary database server instance 212A for customer instance 208, and data center 206B acts as a secondary data center to back up primary data center 206A for a customer instance 208. To back up primary data center 206A for customer instance 208, secondary data center 206B includes a secondary pair of application server instances 210C and 210D and a secondary database server instance 212B. Primary database server instance 212A is able to replicate data to secondary database server instance 212B. As shown in FIG. 2, primary database server instance 212A replicates data to secondary database server instance 212B using a replication operation such as, for example, a Master-Master My SQL Binlog replication operation. The replication of data between data centers could be implemented in real time or by implementing full backup weekly and daily incremental backups in both data centers 206A and 206B. Having both a primary data center 206A and secondary data center 206B allows data traffic that typically travels to the primary data center 206A for the customer instance 208 to be diverted to the second data center 206B during a failure and/or maintenance scenario. Using FIG. 2 as an example, if application server instances 210A and 210B and/or primary data server instance 212A fails and/or is under maintenance, data traffic for customer instances 208 can be diverted to secondary application server instances 210C and 210D and secondary database server instance 212B for processing.
[0039] Although FIGS. 1 and 2 illustrate specific embodiments of a cloud computing system 100 and a multi-instance cloud architecture 200, respectively, the disclosure is not limited to the specific embodiments illustrated in FIGS. 1 and 2. For instance, although FIG. 1 illustrates that cloud resources platform/network 110 is implemented using data centers, other embodiments of the of the cloud resources platform/network 110 are not limited to data centers and can utilize other types of remote network infrastructures. Moreover, other embodiments of the present disclosure may combine one or more different server instances into a single server instance. Using FIG. 2 as an example, application server instances 210A-210D and database server instances 212A-212B can be combined into a single server instance. The use and discussion of FIGS. 1 and 2 are only examples to facilitate ease of description and explanation.
[0040] Referring now to FIG. 3, block diagram 300 illustrates a possible reconciliation framework design that includes multiple engines and sub-engines (e.g., operational units). Diagram 300 represents one configuration of a system for software license monitoring and management according to the present disclosure. Discovery engine 305 includes a plurality of sub-processes that may be used to identify software installations across an enterprise infrastructure such as customer network 102 of FIG. 1 and its connected devices. Discovery engine 305 includes installation probes 320 that may be used to probe systems to discover a software installation footprint. Probes may be run locally on different systems to interrogate the hard disks of each system to identify files that may be an indication of a software installation that must be associated with a license. For example, the probes may identify executable modules, configuration files, or license files that are known to represent a particular software installation. Raw feed interrogator 322 represents a monitoring function that can identify and gather data from information maintained by a software vendor's application running in a customer's environment. For example, a network license server may expose an API or other interface whereby license information may be obtained. Custom scripts 324 (or other types of programs) may be supplied to identify particular software applications expected to exist in a customer network that may not be easily identified by standard probing techniques. Custom scripts 324 represent an available extension to the base functionality that may be tailored as needed (e.g., a plug-in capability). Discovery maps 326 represent configuration files to instruct the system how to discover software applications within the customer network. Publisher packs 328 represent either configuration files such as a publisher specific discovery map or scripts designed to discover software application from a particular publisher (e.g., software vendor). Network monitors 330 represent functional components that may be configured to monitor network traffic to identify software installations or use of subscription based software from particular devices within an enterprise network. Pay per use monitors 332 represent monitors that may be configured to identify software use that is charged based on its use as opposed to the fact that it is merely installed on a particular device. Examples include mainframe applications such as provided by IBM that may be licensed using a Processor Value Unit (PVU). The number of PVU entitlements required is based on the processor technology defined within the PVU Table by Processor Vendor, Brand, Type and Model Number and by the number of processors made available to the program or application being monitored. IBM continues to define a processor, for the purpose of PVU-based licensing, to be each processor core on a chip. A dual-core processor chip, for example, has two processor cores.
[0041] Reconciliation engine 310 represents a second engine of reconciliation framework 300. Reconciliation engine 310 incorporates several sub-engines or operational units to perform functions associated with reconciling information obtained by discovery engine 305 against information pertaining to software licenses (e.g., a license data base). Software suites sub-engine 340 represents a sub-engine configured to manage software applications that may be made available to devices as part of a suite license as opposed to individual application licenses. Some software applications are available both individually and as part of a suite. Allocation sub-engine 342 may be configured to make a determination as to which type of license to allocate to a device as part of reconciliation. License metric sub-engine 346 represents a sub-engine configured to manage information collected by custom license metric logic as may be designed by a customer (See FIG. 6 below). Groupings sub-engine 348 represents a sub-engine configured to perform software licenses groupings. For example, groupings sub-engine 348 may be configured to group allocations and entitlements by geographic region, subsidiary of a lager enterprise, country, cost center, department or other grouping that may be used to track software allocations and cost within an enterprise. Reporting operations 350 represent components of reconciliation engine 310 responsible for presenting reconciliation reports and correlation information for presentation by the reconciliation engine 310.
[0042] Remediation engine 315 contains multiple functional components to assist in performing remediation options to maintain or achieve overall compliance. Allocation creation component 360 allows a user to create allocations for software installations and assign licenses to particular users or devices. Allocation removal component 362 allows removal of licenses previously assigned to user devices. For example, a license may have been assigned to a device and but not be installed thereon. Accordingly, that allocation may be moved to a device that requires a license to address an out of compliance situation. Software uninstallation component 364 represents functionality to automatically initiate uninstallation of software from a target device within the customer network. After uninstallation from that device an allocated license may be reassigned to another device that may have been identified as non-compliant. Allocation purchase component 366 represents functionality to initiate purchase of additional licenses and "true-up" an out of compliance situation. An enterprise may want to exhaust other options to become compliant prior to paying a true-up cost to a software vendor. In one example, allocation purchase component 366 may automatically generate a purchase order containing information appropriate to address non-compliance and submit the purchase order to a purchasing system to facilitate acquisition of additional licenses.
[0043] Referring now to FIG. 4, flow chart 400 includes possible steps to automate a process of software license discovery, reconciliation, and remediation as may be implemented in one or more embodiments of a system for license monitoring and management in accordance with this disclosure. Each of these steps may be performed in the order shown or in a different order. Some steps may be omitted from some implementations and other custom steps may be added as required for different requirements. Beginning at block 405 software installations may be discovered throughout a corporate network. Note that software installations may not be actual installations on a hard disk of a device but may also represent access to subscription based software or pay per use software. At block 410, discovered applications that may be assigned as part of a software suite may be determined to require a suite license rather than an individual application license. At block 415, allocations assigned to devices may be reconciled (e.g., correlated and assigned) against actual software installations. At block 420, license metric calculations (see FIG. 6 discussion below) may be considered and included in the overall reconciliation process. Block 425 indicates that subscription software usage from a particular device may need to be included in an overall reconciliation process. Block 430 indicates that software installations may be associated with one or more groupings to assist in maintaining overall compliance. For example, block 435 indicates a grouping-based-on-department is needed to properly allocate cost within an organization's departments. Similarly, blocks 440, 445, and 450 indicate that software installations may be further associated with groups based on business unit, cost center, or country of use respectively. Block 455 indicates that compliance reports may be generated to provide end-user visibility of a compliance position for the monitored system. Reports may be broken down by groups and subgroups to achieve required levels of granularity (see FIG. 9 discussion below). Block 460 indicates that the system may receive an indication (typically initiated by a license administrator) for adjustments of allocations as part of a remediation plan to address a non-compliance issue as indicated on a report. Block 465 indicates that actions to remediate a non-compliant condition or further adjust licenses that may be compliant (e.g., may be nearly non-compliant) may be initiated by automatically interfacing with other systems of an enterprise. For example, a software license purchase may be initiated or a software uninstallation from one or more devices may be automatically performed.
[0044] Referring now to FIG. 5, screen shot 500 illustrates an example interface screen as may be shown to an end-user defining parameters of a software entitlement (e.g., license set) according to one or more disclosed embodiments. Title 505 indicates that this entitlement is related to a particular product (e.g., Microsoft Project 2016 Professional). Display name 510 defines a name to be used for this entitlement on displays and reports produced by the system. Publisher part number 515 may be used to supply a unique identifier that may be used to associate this software entitlement to a publisher pack used to assist in discovery. License type 520 indicates the type of license model to apply for this software entitlement. Metric group 525 defines a grouping to be used for this entitlement. License metric 530 indicates that this example entitlement is to be applied per device. Agreement type 540 indicates that this entitlement is under a generic agreement. Entry field 545 may be used to enter the number of purchased rights for this entitlement. Active rights 550 indicates that there are fifteen (15) active rights for this entitlement. Allocations available indicates that there are currently twelve (12) allocations of this software entitlement available (e.g., already purchased and not assigned to a device). Data entry area 560 allows for definition of purchase attributes associated with this software entitlement. For example, block 565 allows for entry of a cost center to associate with this entitlement. Data view area 570 indicates a possible downgrade/upgrade scenario applicable to this entitlement. For example, element 575 shows that at least one install of an older version of this product is known to exist within the enterprise network.
[0045] Referring now to FIG. 6, screen shot 600 illustrates of an example interface screen as may be shown to an end-user defining a custom license metric according to one or more disclosed embodiments. The custom license metric in this case is named "Index Volume/Day" as shown at element 605. The calculation (e.g., scripting logic) to be applied to determine this metric is shown at element 610. As explained above, this capability represents an extension that may be used as part of the overall reconciliation logic to include customer specific metrics in their overall software license reconciliation framework. This example custom metric calculates the amount of disk usage on nodes where this custom metric is designated to be run.
[0046] Referring now to FIG. 7, screen shot 700 illustrates one example interface screen as may be shown to an end-user viewing a set of software entitlements and their high-level properties representing multiple license agreements (e.g., for an enterprise or corporation) according to one or more disclosed embodiments. Column 705 includes a display name to indicate which product is represented by each line of the report. Column 710 indicates a metric group with which this product is assigned. For example, the metric group may be custom or may be a particular software vendor associated with the software license information for an associated product. In some embodiments, a product may belong to more than one group. Column 715 indicates the license metric (e.g., per user, per named user, per device, PVU, etc.) providing an indication of the software license model in use for the information provided on the row of the report. Column 720 indicates that all the example licenses shown in screen shot 700 are full licenses (e.g., licenses that are not restricted by use and may be used by anyone, anywhere, in the enterprise). Column 725 indicates the number of active rights for each software entitlement shown. Column 730 indicates the number of purchased rights for each software entitlement shown. Column 735 indicates the cost of the software entitlements shown. This report represents an inventory of available software entitlements for an enterprise and information underlying this report may be used for reconciliation against discovered software installations and usage to produce a compliance report.
[0047] Referring now to FIG. 8, screen shot 800 illustrates an example interface screen as may be shown to an end-user monitoring compliance of a Processor Value Unit (PVU) sub-capacity license model according to one or more disclosed embodiments. Element 805 indicates that there are 21 products currently out of compliance for week 31. Element 810 indicates that the current true-up cost is two hundred twenty thousand dollars for week 31. Graph 825 shows the PVU sub-capacity consumption for weeks 22 through 29. Note in weeks 24, 26, 27 and 28 was below the consumption charge (element 826) whereas in weeks 23, 25 and 29 the PVU sub-capacity consumption exceeded that week's consumption charge. Table 820 lists particular product names and the PVU sub-capacity breakdown of the top 10 products. Screen shot 800 illustrates both the variation possibilities for some software licensing models and further illustrates the potentially large cost of software to enterprise users. Accordingly, software license administrators may benefit from greater visibility and control provided from disclosed embodiments of systems to maintain compliance.
[0048] Referring now to FIG. 9, screen shot 900 illustrates an example interface screen as may be shown to an end-user defining parameters for a compliance report, generated as a step in reconciliation, according to one or more disclosed embodiments. Element 905 indicates that reconciliation may be run for selected publishers (e.g., software vendors). Element 910 indicates that results may be grouped by a primary group and element 915 indicates a sub group within the primary group by which to organize the reconciliation report. Reconciliation is the process of comparing the software entitlements which have been procured, contracted, or subscribed to against the software installations and/or software subscriptions which have been discovered in an environment to determine if the environment is compliant or not compliant with respect to software license usage. The following discussion describes one example process for reconciliation according to disclosed embodiments. When running this example reconciliation, the system takes as input a publisher or publishers for which reconciliation should be run. In addition, a group value may be selected from: country, location, department, cost center, and region. Next, a subgroup may be selected from any of that same set of groupings not selected as the group value. In this example, the system will apply the "right of the entitlement" to only users or devices that both have a software installation and match the specified group and subgroup values from the purchased and/or contracted software entitlement. For example, if the right of entitlement can be applied to users only in the US and there were no rights of entitlement in the UK, then software installations assigned to users located in the UK would be unlicensed. Using a subgroup increases the number of dimensions which must be matched between the user or device and the software entitlement. For example, if a software entitlement exists for users in the IT department within the US, when reconciliation is run with a group of country and subgroup of department, users in the US in the Marketing department that have the software installation would be considered unlicensed. The output of the reconciliation process is a hierarchy of results based on the group and subgroup. The first layer in the hierarchy is a high level product summary of the overall product status across all groups and subgroups, giving the compliance position as well as the potential savings and the over-licensed amount. Within the product results, there is a second level breakdown of product results by group and subgroup. Within this second layer is a third layer giving more granular details about the different versions and editions of the product you own, a fourth layer which gives details about the types of software rights you own for that version and edition of the product, and a fifth layer which gives the users and devices which have a software installation. If reconciliation is run without a group and/or subgroup value, there is only one breakdown of the product result summary. There may also be cases where there is an enterprise or global agreement that is not specific to any one group and subgroup. If this is the case, these global software rights will be considered during reconciliation and can license users or devices across the specified country, department, region, company, or cost center. For example, a global software entitlement will assign a license to users in the US and the UK if reconciliation is run with a group value of country. By structuring the results in a hierarchy, the system may cycle though and calculate how many rights need to be assigned to a user/device for any given software. This is done by creating a rights used by record associated to a license metric result which relates to the software model result. The calculated information from rights used by rolls up to a license metric result, which in turn rolls up to the software model result. Next, everything rolls up to the product result. Each software entitlement record itself has a field called license metric which are calculations used during reconciliation to count the number of rights a user or device needs for a particular piece of software it is using. Each license metric is a distinct calculation (per device assigns a number of rights to a device based on the number of software installations for a product that exist on the device). When reconciliation runs, the process first considers suites and bundles defined in a software model to determine or infer which software installations belong to the suite or bundle. Then the process takes a software product for a publisher and orders all of the license metrics a product uses based on a "reconciliation order--allocated" value and a "reconciliation order--unallocated" value defined on each license metric. Then rights are assigned to software installations based on the rank of the software models within a software product. The rank of the software model is determined by a software models specificity, for example, "Microsoft Project 2016 Professional Windows English" is more specific than "Microsoft Project 2016 Professional." After all of the products within a publisher have been processed, a final pass is done for the publisher to determine if there are any upgrade or downgrade rights which can be used to license any software installations which up until this point are considered unlicensed. After this portion of the process completes, the reconciliation engine moves on to the next publisher until all publishers have been reconciled. When group and subgroup values are used in reconciliation, during the second step, the process will group the software entitlement by the group and subgroup values and then order the license metrics for a software product within a given group and subgroup. At the end of each calculation for product, group and subgroup, downgrades and upgrades are considered. Iterations through the same product are done until all group and subgroup combinations are addressed, then the next product for a publisher is reconciled. This process of ordering license metrics and iterating through products may ensure that software rights are used in an optimal way. For example, two different software entitlements may exist for a software model, one uses the "Per user" license metric while the other uses the "Per named user" metric. In this case, because Per Named User licenses require an allocation those should be allocated first in the allocated round, but in the unallocated round the process would want to consume Per User rights first because those do not require an allocation.
[0049] FIG. 10 illustrates a screen shot 1000 of an example interface screen as may be shown to an end-user viewing reconciliation results according to one or more disclosed embodiments. Element 1005 indicates that this report is grouped by department. Element 1010 indicates that no subgroup was defined for this report. Column 1015 of the report identifies a unique number for each report record. Column 1020 identifies a publisher for each line item. Column 1025 indicates the product for each line item (e.g., display name). Column 1030 indicates a status of "compliant" or "not compliant" for each line item. Column 1035 indicates a true-up cost if applicable. Column 1040 indicates an amount of money spent for licenses that are not in use. Column 1045 indicates a potential savings amount if there is enough information in the system for an actual savings number to be suggested.
[0050] FIG. 11 illustrates a high-level block diagram 1100 of a processing device (computing system) that may be used to implement one or more disclosed embodiments (e.g., service provider cloud infrastructure 110, client devices 104A-104E, server instances 111, data centers 2011A-2011B, etc.). For example, computing device 1100, illustrated in FIG. 11, could represent a client device or a physical server device and could include either hardware or virtual processor(s) depending on the level of abstraction of the computing device. In some instances (without abstraction) computing device 1100 and its elements as shown in FIG. 11 each relate to physical hardware and in some instances one, more, or all of the elements could be implemented using emulators or virtual machines as levels of abstraction. In any case, no matter how many levels of abstraction away from the physical hardware, computing device 1100 at its lowest level may be implemented on physical hardware. As also shown in FIG. 11, computing device 1100 may include one or more input devices 1130, such as a keyboard, mouse, touchpad, or sensor readout (e.g., biometric scanner) and one or more output devices 1115, such as displays, speakers for audio, or printers. Some devices may be configured as input/output devices also (e.g., a network interface or touchscreen display). Computing device 1100 may also include communications interfaces 1125, such as a network communication unit that could include a wired communication component and/or a wireless communications component, which may be communicatively coupled to processor 1105. The network communication unit may utilize any of a variety of proprietary or standardized network protocols, such as Ethernet, TCP/IP, to name a few of many protocols, to effect communications between devices. Network communication units may also comprise one or more transceivers that utilize the Ethernet, power line communication (PLC), Wi-Fi, cellular, and/or other communication methods.
[0051] As illustrated in FIG. 11, processing device 1100 includes a processing element, such as processor 1105, that contains one or more hardware processors, where each hardware processor may have a single or multiple processor cores. In one embodiment, the processor 1105 may include at least one shared cache that stores data (e.g., computing instructions) that are utilized by one or more other components of processor 1105. For example, the shared cache may be a locally cached data stored in a memory for faster access by components of the processing elements that make up processor 1105. In one or more embodiments, the shared cache may include one or more mid-level caches, such as level 2 (L2), level 3 (L3), level 4 (L4), or other levels of cache, a last level cache (LLC), or combinations thereof. Examples of processors include, but are not limited to a central processing unit (CPU) microprocessor. Although not illustrated in FIG. 11, the processing elements that make up processor 1105 may also include one or more other types of hardware processing components, such as graphics processing units (GPUs), application specific integrated circuits (ASICs), field-programmable gate arrays (FPGAs), and/or digital signal processors (DSPs).
[0052] FIG. 11 illustrates that memory 1110 may be operatively and communicatively coupled to processor 1105. Memory 1110 may be a non-transitory medium configured to store various types of data. For example, memory 1110 may include one or more storage devices 1120 that comprise a non-volatile storage device and/or volatile memory. Volatile memory, such as random access memory (RAM), can be any suitable non-permanent storage device. The non-volatile storage devices 1120 can include one or more disk drives, optical drives, solid-state drives (SSDs), tap drives, flash memory, read only memory (ROM), and/or any other type memory designed to maintain data for a duration time after a power loss or shut down operation. In certain instances, the non-volatile storage devices 1120 may be used to store overflow data if allocated RAM is not large enough to hold all working data. The non-volatile storage devices 1120 may also be used to store programs that are loaded into the RAM when such programs are selected for execution.
[0053] Persons of ordinary skill in the art are aware that software programs may be developed, encoded, and compiled in a variety of computing languages for a variety of software platforms and/or operating systems and subsequently loaded and executed by processor 1105. In one embodiment, the compiling process of the software program may transform program code written in a programming language to another computer language such that the processor 1105 is able to execute the programming code. For example, the compiling process of the software program may generate an executable program that provides encoded instructions (e.g., machine code instructions) for processor 1105 to accomplish specific, non-generic, particular computing functions.
[0054] After the compiling process, the encoded instructions may then be loaded as computer executable instructions or process steps to processor 1105 from storage 1120, from memory 1110, and/or embedded within processor 1105 (e.g., via a cache or on-board ROM). Processor 1105 may be configured to execute the stored instructions or process steps in order to perform instructions or process steps to transform the computing device into a non-generic, particular, specially programmed machine or apparatus. Stored data, e.g., data stored by a storage device 1120, may be accessed by processor 1105 during the execution of computer executable instructions or process steps to instruct one or more components within the computing device 1100.
[0055] A user interface (e.g., output devices 1115 and input devices 1130) can include a display, positional input device (such as a mouse, touchpad, touchscreen, or the like), keyboard, or other forms of user input and output devices. The user interface components may be communicatively coupled to processor 1105. When the output device is or includes a display, the display can be implemented in various ways, including by a liquid crystal display (LCD) or a cathode-ray tube (CRT) or light emitting diode (LED) display, such as an OLED display. Persons of ordinary skill in the art are aware that the computing device 1100 may comprise other components well known in the art, such as sensors, powers sources, and/or analog-to-digital converters, not explicitly shown in FIG. 11.
[0056] At least one embodiment is disclosed and variations, combinations, and/or modifications of the embodiment(s) and/or features of the embodiment(s) made by a person having ordinary skill in the art are within the scope of the disclosure. Alternative embodiments that result from combining, integrating, and/or omitting features of the embodiment(s) are also within the scope of the disclosure. Where numerical ranges or limitations are expressly stated, such express ranges or limitations may be understood to include iterative ranges or limitations of like magnitude falling within the expressly stated ranges or limitations (e.g., from about 1 to about 10 includes 2, 3, 4, etc.; greater than 0.10 includes 0.11, 0.12, 0.13, etc.). The use of the term "about" means.+-.10% of the subsequent number, unless otherwise stated.
[0057] Use of the term "optionally" with respect to any element of a claim means that the element is required, or alternatively, the element is not required, both alternatives being within the scope of the claim. Use of broader terms such as comprises, includes, and having may be understood to provide support for narrower terms such as consisting of, consisting essentially of, and comprised substantially of. Accordingly, the scope of protection is not limited by the description set out above but is defined by the claims that follow, that scope including all equivalents of the subject matter of the claims. Each and every claim is incorporated as further disclosure into the specification and the claims are embodiment(s) of the present disclosure.
[0058] It is to be understood that the above description is intended to be illustrative and not restrictive. For example, the above-described embodiments may be used in combination with each other. Many other embodiments will be apparent to those of skill in the art upon reviewing the above description. The scope of the invention therefore should be determined with reference to the appended claims, along with the full scope of equivalents to which such claims are entitled. It should be noted that the discussion of any reference is not an admission that it is prior art to the present invention, especially any reference that may have a publication date after the priority date of this application.
[0059] The subject matter of this disclosure may be applicable to numerous use cases that have not been explicitly discussed here but are contemplated by this disclosure. For example, the provisional applications filed by the same applicant on May 4, 2017 and May 5, 2017 entitled "Service Platform and use thereof" have further examples. The U.S. Provisional applications given filing Ser. Nos. 62/501,646; 62/501,657; 62/502,258; 62/502,308; and 62/502,244 are hereby incorporated by reference.
* * * * *
D00000

D00001

D00002

D00003

D00004

D00005

D00006

D00007

D00008

D00009

D00010

D00011

XML
uspto.report is an independent third-party trademark research tool that is not affiliated, endorsed, or sponsored by the United States Patent and Trademark Office (USPTO) or any other governmental organization. The information provided by uspto.report is based on publicly available data at the time of writing and is intended for informational purposes only.
While we strive to provide accurate and up-to-date information, we do not guarantee the accuracy, completeness, reliability, or suitability of the information displayed on this site. The use of this site is at your own risk. Any reliance you place on such information is therefore strictly at your own risk.
All official trademark data, including owner information, should be verified by visiting the official USPTO website at www.uspto.gov. This site is not intended to replace professional legal advice and should not be used as a substitute for consulting with a legal professional who is knowledgeable about trademark law.