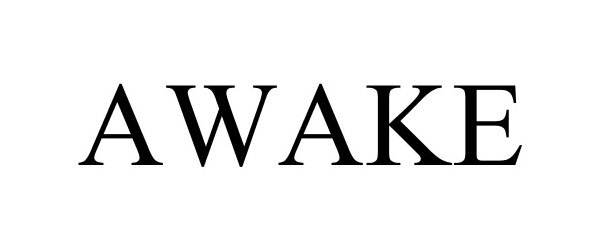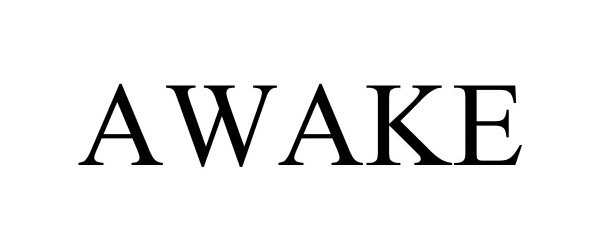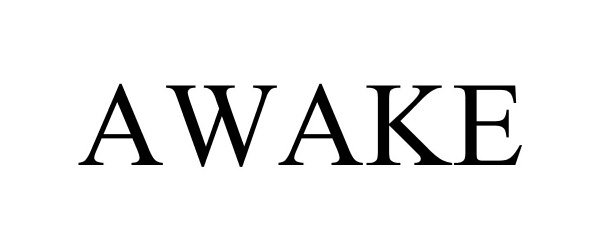IC 037. US 100 103 106. G & S: technical support and consulting services related to customizing, installing, maintaining and repairing cyber-security computer hardware systems for others. FIRST USE: 20170500. FIRST USE IN COMMERCE: 20170500
IC 042. US 100 101. G & S: information technology troubleshooting, namely, investigation, research and diagnosis of computer system and computer network threats; Computer consultation in the field of computer security to detect and assess information security vulnerability; computer services, namely, on-line scanning, detecting, quarantining and eliminating of viruses, worms, trojans, adware, spyware, rootkits, backdoors, zero-day attacks, data exfiltration, phishing, bots, time bombs, cyber-attacks, malicious attacks, advanced persistent threats, malware and unauthorized data and programs on computers, computer systems, networks, hardware, software applications, digital devices, and mobile devices; computer security services for protecting and managing enterprise networks; computer security services, namely, restricting and detecting unauthorized access to enterprise computer networks; technical support and consulting services related to security and vulnerability of, and cyber-attacks and threats against computers, computer systems, networks, hardware, software applications, digital devices, digital data, and mobile devices; technical support and consulting services related to designing, developing, customizing, configuring, deploying, installing, maintaining, analyzing, integrating, repairing, and managing of cyber-security systems for others; technical support services in the nature of detecting and diagnosing computer hardware and software security problems and vulnerabilities, updating and maintenance of computer software relating to computer security and to prevention and mitigation of computer risks; cloud computing services featuring software and databases for use in computer security and prevention and mitigation of computer risks; computer security consultancy in the field of malware, intrusion and penetration testing and diagnosis of computers and networks to assess information technology security and vulnerability; application service provider (asp) featuring software for use for detection, blocking, and facilitating removal and remediation of viruses, worms, trojans, adware, spyware, rootkits, backdoors, zero-day attacks, data exfiltration, phishing, bots, time bombs, cyber-attacks, malicious attacks, advanced persistent threats and other malware in computers, computer systems, networks, hardware, software applications, digital devices, and mobile digital devices; application service provider (asp) featuring software that provides secure virtual computer systems and virtual computing environments; providing temporary use of non-downloadable, artificial-intelligence based network security software that detects and prioritizes mal-intent and behavioral threats from internal and external sources and performs autonomous incident triage; providing temporary use of non-downloadable computer software for use in protecting and managing enterprise security; providing temporary use of non-downloadable computer software for digital security; providing temporary use of non-downloadable computer software and non-downloadable software platform, all for monitoring enterprise networks and computer systems to protect against malicious attacks; providing temporary use of non-downloadable computer software for monitoring data and communications for security purposes; providing temporary use of non-downloadable computer software for protecting private information on enterprise networks; providing temporary use of non-downloadable computer software for implementing computer, software and network security measures; providing temporary use of non-downloadable computer software for monitoring and detecting security breaches; providing temporary use of non-downloadable computer software that provides intrusion alert, threat protection and other security functions; providing temporary use of non-downloadable anti-malware software applications; providing temporary use of non-downloadable computer software for providing network, Internet, and computer security; providing temporary use of non-downloadable computer software for scanning, detecting, remediating and removing viruses, worms, trojans, adware, spyware, rootkits, backdoors, zero-day attacks, data exfiltration, phishing, bots, time bombs, cyber-attacks, malicious attacks, advanced persistent threats and other malware; providing temporary use of non-downloadable Internet security software, including namely, computer software for use in the monitoring and control of computer and online activity; providing temporary use of non-downloadable computer software for identifying and preventing malicious attacks on, and unauthorized activities and intrusions in computers, computer systems, networks, hardware, software applications, digital devices, and mobile devices; providing temporary use of non-downloadable computer software for providing secure networks; providing temporary use of non-downloadable computer software for security analytics; providing temporary use of non-downloadable computer software for network traffic analysis; providing temporary use of non-downloadable computer software for network detection and response; providing temporary use of non-downloadable computer software for threat investigations and incident response; providing temporary use of non-downloadable computer software for threat hunting. FIRST USE: 20170500. FIRST USE IN COMMERCE: 20170500
| International Codes: | 37 |
| U.S. Codes: | 100,103,106 |
| International Codes: | 42 |
| U.S. Codes: | 100,101 |
| Type Code | Type |
|---|
| GS0421 | Information technology troubleshooting, namely, investigation, research and diagnosis of computer system and computer network threats; Computer consultation in the field of computer security to detect and assess information security vulnerability; computer services, namely, on-line scanning, detecting, quarantining and eliminating of viruses, worms, trojans, adware, spyware, rootkits, backdoors, zero-day attacks, data exfiltration, phishing, bots, time bombs, cyber-attacks, malicious attacks, advanced persistent threats, malware and unauthorized data and programs on computers, computer systems, networks, hardware, software applications, digital devices, and mobile devices; computer security services for protecting and managing enterprise networks; computer security services, namely, restricting and detecting unauthorized access to enterprise computer networks; technical support and consulting services related to security and vulnerability of, and cyber-attacks and threats against computers, computer systems, networks, hardware, software applications, digital devices, digital data, and mobile devices; technical and consulting services related to designing, developing, customizing, configuring, deploying, installing, maintaining, analyzing, integrating, repairing, and managing of cyber-security systems for others; technical support services in the nature of detecting and diagnosing computer hardware and software security problems and vulnerabilities, updating and maintenance of computer software relating to computer security and to prevention and mitigation of computer risks; cloud computing services featuring software and databases for use in computer security and prevention and mitigation of computer risks; computer security consultancy in the field of malware, intrusion and penetration testing and diagnosis of computers and networks to assess information technology security and vulnerability; application service provider (asp) featuring software for use for detection, blocking, and facilitating removal and remediation of viruses, worms, trojans, adware, spyware, rootkits, backdoors, zero-day attacks, data exfiltration, phishing, bots, time bombs, cyber-attacks, malicious attacks, advanced persistent threats and other malware in computers, computer systems, networks, hardware, software applications, digital devices, and mobile digital devices; application service provider (asp) featuring software that provides secure virtual computer systems and virtual computing environments |
| GS0371 | technical support and consulting services related to customizing, installing, maintaining and repairing cyber-security computer hardware systems for others |