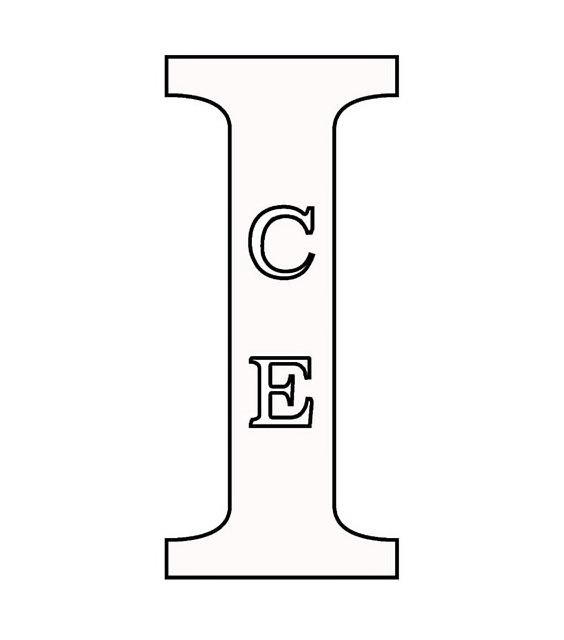
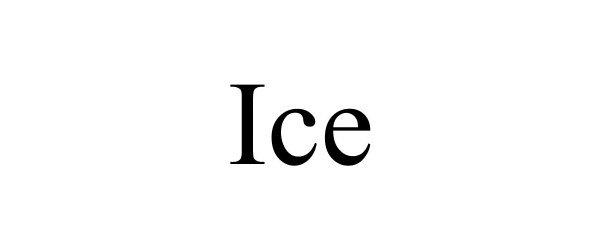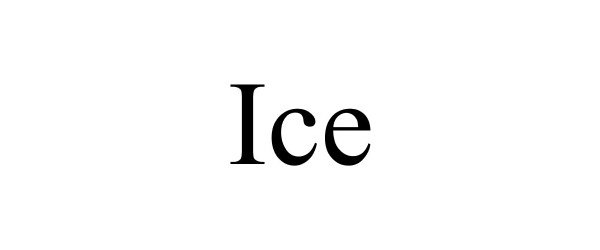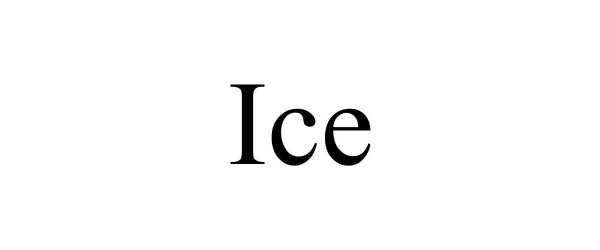IC 009. US 021 023 026 036 038. G & S: Access control and alarm monitoring systems; Biometric identification apparatus; Cards encoded with security features for identification purposes; Security devices, namely, mobile image projection device for displaying retinal images; Software for ensuring the security of electronic mail; Computer programs for the enabling of access or entrance control; Computer software and firmware for authenticating user identification, data encryption; Computer software for encryption; Computer software for authorising access to data bases; Computer software for authorising access to databases; Computer software for use in the encryption and decryption of digital files, including audio, video, text, binary, still images, graphics and multimedia files; Downloadable middleware for authenticating user identification, data encryption; Dynamic random access memory (DRAM); Electronic access control systems for interlocking doors; Electronic coding units; Electronic encryption units; Electronic security and surveillance devices, namely, electronic security tags and labels, acoustic tags, magnetic tags; Electronic readers and controllers for controlling access to a premises; Electronic security token in the nature of a fob-like device used by an authorized user of a computer system to facilitate authentication; Electronic text-messaging device for use in conjunction with personal digital assistants; Entry/exit security portal comprised of an electronic passageway equipped with biometric devices for identification verification and detection of impermissible items being carried through; External computer hard drives featuring software for data encryption; Magnetic coded card readers; Network access server hardware; Network access server operating software; USB computer security key; USB computer access control key; Wireless controllers to remotely monitor and control the function and status of other electrical, electronic, and mechanical devices or systems, namely, secure access entry devices, encrypted devices; Wireless digital electronic apparatus to secure and protect data and images on all forms of wireless equipment including mobile telecommunications equipment using an automatic synchronization process and alarm notification of the loss or theft of the wireless equipment including mobile telecommunications equipment. FIRST USE: 20170214. FIRST USE IN COMMERCE: 20170214
IC 038. US 100 101 104. G & S: Encrypted electronic transmission and delivery of recovered data; Computer transmission of information accessed via a code or a terminal; Electronic transmission of facsimile communications and data featuring encryption and decryption; Information transmission by telematic codes; Providing access to databases; Providing access to telecommunication networks; Providing private and secure real time electronic communication over a computer network; Providing user access to global computer networks; Providing virtual private network (VPN) services, namely, private and secure electronic communications over a private or public computer network; Telecommunication services, namely, providing electronic message alerts via the internet notifying individuals of a changed status or condition of a sensing device in a security system; Transmission, reception and processing of coded and emergency signals. FIRST USE: 20170214. FIRST USE IN COMMERCE: 20170214
IC 042. US 100 101. G & S: Computer security consultancy; Computer security consultancy in the field of scanning and penetration testing of computers and networks to assess information security vulnerability; Computer security consultancy in the field of computer security, data encryption; Computer security services in the nature of administering digital certificates; Computer security services in the nature of administering digital keys; Computer consultation in the field of computer security; Computer consultation in the field of computer security, data encryption; Data security consultancy; Authentication, issuance and validation of digital certificates; Computer code conversion for others; Computer security services in the nature of providing authentication, issuance, validation and revocation of digital certificates; Computer security services, namely, restricting unauthorized access to secured access areas, encrypted data; Computer security services, namely, restricting unauthorized network access by users without credentials; Computer security threat analysis for protecting data; Computer security service, namely, restricting access to and by computer networks to and of undesired web sites, media and individuals and facilities; Computer services, namely, encrypted data recovery services; Data encryption and decoding services; Data encryption services; Data encryption services for providing security and anonymity for electronically transmitted credit card transactions; Design and development of electronic data security systems; Design, development, and implementation of software for authenticating user identification, data encryption; Development of software for secure network operations; Electronic document and e-mail authentication services; Electronic signature verification services using technology to authenticate user identity; Installation and maintenance of data encryption software; Installation of data encryption software; Installation, maintenance and repair of data encryption software; Maintenance of computer software relating to computer security and prevention of computer risks; Maintenance of computer software used for data encryption; Providing a secure, web-based service featuring technology that enables individuals to remotely create and manage their own accounts so that whatever private content they upload now can be encrypted, then delivered to their intended recipients, at the time and in the manner requested; Providing electronic verification of on-line orders of digital content and generating electronic permission codes which then allow users to access said digital content; Updating of computer software relating to computer security and prevention of computer risks. FIRST USE: 20170214. FIRST USE IN COMMERCE: 20170214
IC 045. US 100 101. G & S: Identification verification services, namely, providing authentication of personal identification information; Identification verification services, namely, providing authentication of personal identification information via secure storage and transmitting such information via the Internet; Providing user authentication of electronic funds transfer, credit and debit card and electronic check transactions via a global computer network; Providing user authentication services in e-commerce transactions. FIRST USE: 20170214. FIRST USE IN COMMERCE: 20170214
| International Codes: | 9 |
| U.S. Codes: | 021,023,026,036,038 |
| International Codes: | 38 |
| U.S. Codes: | 100,101,104 |
| International Codes: | 42 |
| U.S. Codes: | 100,101 |
| International Codes: | 45 |
| U.S. Codes: | 100,101 |
| Type Code | Type |
|---|
| CC0000 | The color(s) Blue, white, black, and gray is/are claimed as a feature of the mark. |
| CC0000 | The color(s) Blue, white, black, and gray is/are claimed as a feature of the mark. |