Resource remapping and regrouping in a wireless communication system
Zhang , et al.
U.S. patent number RE47,374 [Application Number 15/040,930] was granted by the patent office on 2019-04-30 for resource remapping and regrouping in a wireless communication system. This patent grant is currently assigned to Samsung Electronics Co., Ltd.. The grantee listed for this patent is Samsung Electronics Co., Ltd. Invention is credited to Joonyoung Cho, Farooq Khan, Juho Lee, Aris Papasakellariou, Zhouyue Pi, Jianzhong Zhang.








| United States Patent | RE47,374 |
| Zhang , et al. | April 30, 2019 |
Resource remapping and regrouping in a wireless communication system
Abstract
Methods and apparatus for remapping and regrouping transmission resources in a wireless communication system. First, a set of new permutation algorithms based on Galois field operation is proposed. Then the proposed algorithms and the known Pruned Bit Reversal Ordering (PBRO) algorithm are applied to several of various resource mapping schemes, including slot or symbol level Orthogonal Cover (OC)/Cyclic Shift (CS) mapping, cell-specific slot-level and symbol-level CS hopping patterns, and subframe and slot level base sequence hopping patterns.
| Inventors: | Zhang; Jianzhong (Plano, TX), Cho; Joonyoung (Suwon-si, KR), Pi; Zhouyue (Allen, TX), Lee; Juho (Suwon-si, KR), Papasakellariou; Aris (Houston, TX), Khan; Farooq (Allen, TX) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Applicant: |
|
||||||||||
| Assignee: | Samsung Electronics Co., Ltd.
(Suwon-si, KR) |
||||||||||
| Family ID: | 40210767 | ||||||||||
| Appl. No.: | 15/040,930 | ||||||||||
| Filed: | February 10, 2016 |
Related U.S. Patent Documents
| Application Number | Filing Date | Patent Number | Issue Date | ||
|---|---|---|---|---|---|
| 14261197 | Apr 24, 2014 | ||||
| 12200462 | Aug 28, 2008 | 8077693 | |||
| 60960497 | Oct 1, 2007 | ||||
| 60960191 | Sep 19, 2007 | ||||
| Reissue of: | 13215963 | Aug 23, 2011 | 8681766 | Mar 25, 2014 | |
| Reissue of: | 13215963 | Aug 23, 2011 | 8681766 | ||
| Current U.S. Class: | 1/1 |
| Current CPC Class: | H04L 5/0055 (20130101); H04L 5/0048 (20130101); H04L 5/0057 (20130101); H04L 5/0057 (20130101); H04L 5/0048 (20130101); H04L 5/0055 (20130101); H04L 5/0007 (20130101); H04L 1/0026 (20130101); H04L 1/0026 (20130101); H04L 1/0071 (20130101); H04L 5/0014 (20130101); H04L 5/0037 (20130101); H04L 1/0071 (20130101); H04L 5/0037 (20130101); H04L 5/0007 (20130101); H04L 5/0014 (20130101); H04L 1/1607 (20130101); H04L 1/1607 (20130101) |
| Current International Class: | H04L 1/00 (20060101); H04L 5/00 (20060101); H04L 1/16 (20060101) |
| Field of Search: | ;455/39,62,73,561,93,103 ;370/203-211,321-324,326,336-337,345-348 |
References Cited [Referenced By]
U.S. Patent Documents
| 5820390 | October 1998 | Takamoto et al. |
| 6031827 | February 2000 | Rikkinen et al. |
| 6912240 | June 2005 | Kumar et al. |
| 6925068 | August 2005 | Stanwood et al. |
| 7075945 | July 2006 | Arsenault et al. |
| 7746916 | June 2010 | Han et al. |
| 7761750 | July 2010 | Eroz et al. |
| 8724444 | May 2014 | Ko et al. |
| 2001/0019576 | September 2001 | Nystrom et al. |
| 2002/0154621 | October 2002 | Laroia et al. |
| 2003/0067943 | April 2003 | Arsenault et al. |
| 2004/0062193 | April 2004 | Ma et al. |
| 2005/0030931 | February 2005 | Sung et al. |
| 2005/0037764 | February 2005 | Trachtman |
| 2005/0157670 | July 2005 | Tang et al. |
| 2006/0020754 | September 2006 | Ji et al. |
| 2006/0209754 | September 2006 | Ji et al. |
| 2007/0171995 | July 2007 | Muharemovic et al. |
| 2007/0183386 | August 2007 | Muharemovic et al. |
| 2008/0051125 | February 2008 | Muharemovic et al. |
| 2008/0107192 | May 2008 | Mukkavilli et al. |
| 2008/0310383 | December 2008 | Kowalski |
| 2008/0311942 | December 2008 | Kim et al. |
| 2013/0286977 | October 2013 | Kwon et al. |
| 1594235 | Nov 2005 | EP | |||
| 9097658 | Apr 1997 | JP | |||
| 2002-523915 | Jul 2002 | JP | |||
| 2002-523970 | Jul 2002 | JP | |||
| 3427056 | Jul 2003 | JP | |||
| 2010-525728 | Jul 2010 | JP | |||
| 2010-536229 | Nov 2010 | JP | |||
| 10-2002-0084517 | Nov 2002 | KR | |||
| 10-2007-0053756 | May 2007 | KR | |||
| 2005118847 | Dec 2006 | RU | |||
| WO 2001-76110 | Oct 2001 | WO | |||
| WO 2006-069826 | Jul 2006 | WO | |||
| WO 2007-024109 | Mar 2007 | WO | |||
| WO 2007-035302 | Mar 2007 | WO | |||
| WO 2008-132073 | Nov 2008 | WO | |||
| WO 2008-0153298 | Dec 2008 | WO | |||
Other References
|
Examination Report dated Aug. 10, 2016 in connection with Indian Application No. 1403/CHENP/2010, 8 pages. cited by applicant . Notification of Reason for Rejection, dated Sep. 18, 2015, in connection with Japanese Patent Application No. 2014-065511, 11 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #47bis, "Uplink control channel multiplexing", R1-070330, Jan. 15-19, 2007, Sorrento, Italy, 4 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #49bis, "Cyclic Shift Hopping of UL ACK Channels", R1-073149, Jun. 25-29, 2007, Orlando, US, 6 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #50, "Symbol based cyclic shift hopping", R1-073643, Aug. 20-24, 2007, Athens, Greece, 6 pages. cited by applicant . Notification of Reason for Rejection, dated Jul. 27, 2015, in connection with Japanese Patent Application No. 2014-110996, 38 pages. cited by applicant . 3GPP TSG RAN WG1 #50, "Joint Coding of CQI and ACK", R1-073260, Aug. 20-24, 2007, Athens, Greece, 7 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #50, "Code Allocation for UL ACK/NACK Channels", R1-073522, Aug. 20-24, 2007, Athens, Greece, 3 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #50bis, "SLot-level UL ACK/NACK Cyclic Shift/Orthogonal Cover Remapping", R1-074092, Oct. 8-12, 2007, Shanghai, China, 6 pages. cited by applicant . Decision of Grant, dated Aug. 7, 2015, in connection with Korean Patent Application No. 10-2014-0040134, 7 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #49bis; "Uplink Data-non-associated Control Signaling in E-UTRA"; R1-073072; Orlando, FL, U.S.; Jun. 25-29, 2007; 5 pages. cited by applicant . Translated Japanese Notification of Rejection of Application in connection with Japanese JP 2014-065511; dated Feb. 23, 2015; 7 pages. cited by applicant . Extended European Search Report dated Jul. 3, 2014 in connection with European Patent Application No. 08016543.4; 10 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #52 "Slot-level UL ACK/NACK Cyclic Shift/Orthogonal Cover Remapping", Sorrento, Italy, Feb. 11-15, 2008, 6 pages. cited by applicant . Extended European Search Report dated Apr. 23, 2014 in connection with European Patent Application No. 14162731.5, 10 pages. cited by applicant . Translated Korean Office Action dated May 16, 2014 in connection with Korean Patent Application No. 10-2008-0092278, 7 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #50; "Randomization of intra-cell interference in PUCCH"; R1-073412; Athens, Greece; Aug. 20-24, 2007; 6 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #50; "Sequence allocation and hopping for uplink ACK/NAK channels"; R1-073413; Athens, Greece; Aug. 20-24, 2007; 6 pages. cited by applicant . 3GPP TSG RAN WG1 Mtg. #50; "Cell Specific Cyclic Shift Hopping vs UE specific Cyclic Shift Hopping for Uplink ACK/NACK Signals"; R1-073619; Athens, Greece; Aug. 20-24, 2007, 4 p. cited by applicant . 3GPP TSG RAN WG1 Meeting #50; "Cyclic shift and orthogonal cover allocations for UL ACK/NACK" R1-074094; Athens, Greece; Aug. 20-24, 2007; 5 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #51; "Slot-level UL ACK/NACK Cyclic/Orthogonal Cover Remapping"; R1-074788; Jeju, Korea; Nov. 5-9, 2007; 6 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #50; "Implicit ACK/NAK Multiplexing in PUCCH CQI Sub-Frame Structure"; R1-073577; Athens, Greece; Aug. 20-24, 2007; 5 pages. cited by applicant . Intl. Search Report of the International Searching Authority dated Mar. 23, 2009 in connection with Intl. Application No. PCT/KR2008/005569, filed Sep. 19, 2008. cited by applicant . Written Opinion of the International Searching Authority dated Mar. 23, 2009 in connection with International Application No. PCT/KR2008/005569, filed Sep. 19, 2008. cited by applicant . European Office Action for European Application No. 08016534.4, dated Jul. 20, 2017. (9 Pages). cited by applicant . European Office Action for European Application No. 14162731.5, dated Jul. 20, 2017. (9 pages). cited by applicant . Extended European Search Report for European Application No. 17165821.4, dated Jul. 21, 2017. (11 pages). cited by applicant . Nokia Siemens Networks, et al, "Signaling of Implicit ACK/NACK resource", 3GPP TSG RAN WG1 Meeting #49bis, R1-073006, Orlando, USA, Jun. 25-29, 2007. (7 pages). cited by applicant . Qualcomm Europe, "PUSCH and PUCCH hopping patters", 3GPP TSG-RAN WG1 #50, R1-073264, Athens, Greece, Aug. 20-24, 2007. (4 pages). cited by applicant . Toshiba, "CAZAC sequence for PUCCH", 3GPP TSGRAN WG1 meeting #50, R1-073316, Athens, Greece, Aug. 20-24, 2007. (3 pages). cited by applicant . Nokia Siemens Networks, et al., "Cyclic Shift Hopping and DM RS Signaling", 3GPP TSG RAN WG1 Meeting #50, R1-073644, Athens, Greece, Aug. 20-24, 2007. (4 pages). cited by applicant . 3GPP TSG RAN WG1 Meeting #50, "CAZAC sequence for PUCCH", Athens, Greece, Aug. 20-24, 2007, 3 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #50, "S-SCH scrambling and mapping methods", Athens, Greece, Oct. 20-24, 2007, 10 pages. cited by applicant . International Search Report of the International Searching Authority issued on Mar. 23, 2009 in connection with International Application No. PCT/KR2008/005569, filed Sep. 19, 2008. cited by applicant . Written Opinion of the International Searching Authority issued on Mar. 23, 2009 in connection with International Application No. PCT/KR2008/005569, filed Sep. 19, 2008. cited by applicant . 3GPP TSG RAN WG1 #50, "Chairman's Notes", Athens, Greece, Aug. 20-24, 2007. cited by applicant . 3GPP TSG RAN WG1 Meeting #50, R1-073541, "UL ACK/NACK Channel Structure", Athens, Greece, Aug. 20-24, 2007. cited by applicant . 3GPP TSG RAN WG1 Meeting #50, R1-073564, "Selection of Orthogonal Cover and Cyclic Shift for High Speed UL ACK Channels", Athens, Greece, Aug. 20-24, 2007. cited by applicant . 3 GPP TSG RAN WG1 #49, R1-072225, "CCE to RE Mapping", Kobe, Japan, May 7-11, 2007. cited by applicant . 3GPP TSG RAN WG1 Meeting #50, R1-073412, "Randomization of Intra-cell Interference in PUCCH", Athens, Greece, Aug. 20-24, 2007. cited by applicant . 3GPP TSG RAN WG1 Meeting #50, R1-073413, "Sequence Allocation and Hopping for Uplink ACK/NAK Channels", Athens, Greece, Aug. 20-24, 2007. cited by applicant . 3GPP TSG RAN WG1 Meeting #50, R1-073661, "Signaling of Implicit ACK/NACK Resources", Athens, Greece, Aug. 20-24, 2007. cited by applicant . 3GPP TSG RAN WG1 Meeting #49bis, "Summary of Reflector Discussions on EUTRA UL RS", Orlando, FL, Jun. 25-29, 2007, 4 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #50, "Pusch and Pucch hopping patterns", Athens, Greece, Aug. 20-24, 2007, 4 pages. cited by applicant . 3GPP TSG RAN WG1 Meeting #50, "Summary of Reflector Discussions on EUTRA DL RS", Athens, Greece, Aug. 20-24, 2007, 3 pages. cited by applicant . 3GPP TSG RAN1#50; "E-UTRA Uplink Reference Signal Planning and Hopping Considerations", Athens, Greece, Aug. 20-24, 2007, 11 pages. cited by applicant . Translated Japanese Examination Report in connection with Japanese JP 2012-256144; dated Nov. 5, 2013; 8 pages. cited by applicant. |
Primary Examiner: Sager; Mark
Parent Case Text
CLAIM OF PRIORITY
This application .Iadd.is a reissue of U.S. Pat. No. 8,681,766 issued Mar. 25, 2014 on U.S. patent application Ser. No. 13/215,963 filed Aug. 23, 2011 and entitled "RESOURCE REMAPPING AND REGROUPING IN A WIRELESS COMMUNICATION SYSTEM," and .Iaddend.is a continuation of .[.U.S. patent application Ser. No. 12/200,462, filed on Aug. 28, 2008, entitled "RESOURCE REMAPPING AND REGROUPING IN A WIRELESS COMMUNICATION SYSTEM," now U.S. Pat. No. 8,077,693, which claims priority to U.S. Provisional Patent Application No. 60/960,191 filed on Sep. 19, 2007, and U.S. Provisional Patent Application No. 60/960,497 filed on Oct. 1, 2007. U.S. patent application Ser. No. 12/200,462 is assigned to the assignee of the present application and.]. .Iadd.U.S. Reissue patent application Ser. No. 14/261,197 filed Apr. 24, 2014, which is also a reissue of U.S. Pat. No. 8,681,766. U.S. patent application Ser. No. 13/215,963 is a continuation of U.S. patent Ser. No. 12/200,462 filed Aug. 28, 2008 and having the same title, now U.S. Pat. No. 8,077,693, and claims priority to U.S. Provisional Patent Application Ser. No. 60/960,191 filed Sep. 19, 2007 and U.S. Provisional Patent Application Ser. No. 60/960,497 filed Oct. 1, 2007. The content of the above-identified patent documents .Iaddend.is incorporated by reference into this disclosure as if fully set forth herein. .[.This disclosure hereby claims priority under 35 U.S.C. .sctn.120 to U.S. patent application Ser. No. 12/200,462. This application makes reference to, incorporates the same herein, and claims all benefits accruing under 35 U.S.C. .sctn. 119 from provisional applications earlier filed in the U.S. Patent & Trademark Office on 19 Sep. 2007 and there duly assigned Ser. No. 60/960,191, and on 1 Oct. 2007 and there duly assigned Ser. No. 60/960,497, respectively..].
Claims
What is claimed is:
.[.1. A method for data transmission in a communication system, the method comprising: modulating data to be transmitted to generate a modulated data; selecting a first resource to be used in a first time based on a function of a first time index; selecting a second resource to be used in a second time based on the first time index and a second time index; mapping the modulated data to the selected first resource and the selected second resource at the first time and the second time, respectively; and transmitting the modulated data at each of the first time and the second time, wherein the first resource and the second resource are at least one of an orthogonal code and a cyclic shift of a base, wherein each of the first time and second time is defined on at least one of a symbol level and a slot level, and wherein a slot consists of at least one symbol..].
.[.2. The method of claim 1, wherein when the modulated data to be transmitted is acknowledgement and negative acknowledgement (ACK/NACK) data, the resource is an orthogonal code and a cyclic shift of a base..].
.[.3. The method of claim 1, wherein when the modulated data to be transmitted is Channel Quality Indicator (CQI) data, the resource is a cyclic shift of a base..].
.[.4. The method of claim 1, wherein the cyclic shift of a base is defined on a per symbol level or a slot level based on a symbol index or a slot index, respectively..].
.[.5. The method of claim 1, wherein the orthogonal code is defined on a per slot level based on a slot index..].
.[.6. The method of claim 1, wherein mapping the modulated data comprises symbol wise spreading the modulated data with the orthogonal code..].
.[.7. The method of claim 1, wherein selecting the first resource to be used in the first time and selecting the second resource to be used in the second time are based upon an amount of a total resource associated with a corresponding time index..].
.[.8. The method of claim 1, wherein when a total resource is shared by CQI transmission and ACK/NACK transmission, the total resource is separated into a portion for CQI transmission and a portion for ACK/NACK transmission..].
.[.9. The method of claim 8, wherein resource for CQI transmission and resource for ACK/NACK transmission are selected among the portion for CQI transmission and the portion for ACK/NACK transmission, respectively, at each corresponding time..].
.[.10. An apparatus in a wireless communication network, the apparatus comprising: a transmitter chain configured to: modulate data to be transmitted to generate a modulated data; select a first resource to be used in a first time based on a function of a first time index; select a second resource to be used in a second time based on the first time index and a second time index; map the modulated data to the selected first resource and the selected second resource at the first time and the second time, respectively; and transmit the modulated data at each of the first time and the second time, wherein the first resource and the second resource are at least one of an orthogonal code and a cyclic shift of a base, wherein each of the first time and second time is defined on at least one of a symbol level and a slot level, and wherein a slot consists of at least one symbol..].
.[.11. The apparatus of claim 10, wherein when the modulated data to be transmitted is acknowledgement and negative acknowledgement (ACK/NACK) data, the resource is an orthogonal code and a cyclic shift of a base..].
.[.12. The apparatus of claim 10, wherein when the modulated data to be transmitted is Channel Quality Indicator (CQI) data, the resource is a cyclic shift of a base..].
.[.13. The apparatus of claim 10, wherein the cyclic shift of a base is defined on a per symbol level or a slot level based on a symbol index or a slot index, respectively..].
.[.14. The apparatus of claim 10, wherein the orthogonal code is defined on a per slot level based on a slot index..].
.[.15. The apparatus of claim 10, wherein the transmitter chain is configured to map the modulated data by symbol wise spreading the modulated data with the orthogonal code..].
.[.16. The apparatus of claim 10, wherein the transmitter chain is configured to select the first resource to be used in the first time and select the second resource to be used in the second time based upon an amount of a total resource associated with a corresponding time index..].
.[.17. The apparatus of claim 10, wherein when a total resource is shared by CQI transmission and ACK/NACK transmission, the total resource is separated into a portion for CQI transmission and a portion for ACK/NACK transmission..].
.[.18. The apparatus of claim 17, wherein resource for CQI transmission and resource for ACK/NACK transmission are selected among the portion for CQI transmission and the portion for ACK/NACK transmission, respectively, at each corresponding time..].
.[.19. An apparatus in a wireless communication network, the apparatus comprising: a receiver chain configured to: receive modulated data mapped to a first resource at a first time, the first time based on a function of a first time index; and receive modulated data mapped to a second resource at a first time, the second time based on the first time index and a second time index, wherein the first resource and the second resource are at least one of an orthogonal code and a cyclic shift of a base, wherein each of the first time and second time is defined on at least one of a symbol level and a slot level, and wherein a slot consists of at least one symbol..].
.[.20. The apparatus of claim 19, wherein when the received data is acknowledgement and negative acknowledgement (ACK/NACK) data, the resource is an orthogonal code and a cyclic shift of a base..].
.[.21. The apparatus of claim 19, wherein when the received data is Channel Quality Indicator (CQI) data, the resource is a cyclic shift of a base..].
.[.22. The apparatus of claim 19, wherein the cyclic shift of a base is defined on a per symbol level or a slot level based on a symbol index or a slot index, respectively..].
.[.23. The apparatus of claim 19, wherein the orthogonal code is defined on a per slot level based on a slot index..].
.[.24. The apparatus of claim 19, wherein the modulated data is mapped using symbol wise spreading with the orthogonal code..].
.[.25. The apparatus of claim 19, wherein the first resource used in the first time and the second resource used in the second time are selected based upon an amount of a total resource associated with a corresponding time index..].
.[.26. The apparatus of claim 19, wherein when a total resource is shared by CQI transmission and ACK/NACK transmission, the total resource is separated into a portion for CQI transmission and a portion for ACK/NACK transmission..].
.[.27. The apparatus of claim 26, wherein resource for CQI transmission and resource for ACK/NACK transmission are selected among the portion for CQI transmission and the portion for ACK/NACK transmission, respectively, at each corresponding time..].
.[.28. A method for data transmission in a communication system, the method comprising: receiving modulated data mapped to a first resource at a first time, the first time based on a function of a first time index; and receiving modulated data mapped to a second resource at a first time, the second time based on the first time index and a second time index, wherein the first resource and the second resource are at least one of an orthogonal code and a cyclic shift of a base, wherein each of the first time and second time is defined on at least one of a symbol level and a slot level, and wherein a slot consists of at least one symbol..].
.[.29. The method of claim 28, wherein when the received data is acknowledgement and negative acknowledgement (ACK/NACK) data, the resource is an orthogonal code and a cyclic shift of a base..].
.[.30. The method of claim 28, wherein when the received data is Channel Quality Indicator (CQI) data, the resource is a cyclic shift of a base..].
.[.31. The method of claim 28, wherein the cyclic shift of a base is defined on a per symbol level or a slot level based on a symbol index or a slot index, respectively..].
.[.32. The method of claim 28, wherein the orthogonal code is defined on a per slot level based on a slot index..].
.[.33. The method of claim 28, wherein the modulated data is mapped using symbol wise spreading with the orthogonal code..].
.[.34. The method of claim 28, wherein the first resource used in the first time and the second resource used in the second time are selected based upon an amount of a total resource associated with a corresponding time index..].
.[.35. The method of claim 28, wherein when a total resource is shared by CQI transmission and ACK/NACK transmission, the total resource is separated into a portion for CQI transmission and a portion for ACK/NACK transmission..].
.[.36. The method of claim 35, wherein resource for CQI transmission and resource for ACK/NACK transmission are selected among the portion for CQI transmission and the portion for ACK/NACK transmission, respectively, at each corresponding time..].
.Iadd.37. A method for transmission of information in a communication system, the method comprising: obtaining an orthogonal sequence allocated for a first slot and a first cyclic shift corresponding to all symbols for the first slot and a cell identifier; obtaining an orthogonal sequence allocated for a second slot and a second cyclic shift corresponding to all symbols for the second slot and the cell identifier; applying the first cyclic shift corresponding to the symbols for the first slot and the orthogonal sequence for the first slot to information for the first slot; applying the second cyclic shift corresponding to the symbols for the second slot and the orthogonal sequence for the second slot to information for the second slot; transmitting, in the first slot, the information to which has been applied the first cyclic shift corresponding to the symbols for the first slot and the orthogonal sequence for the first slot; and transmitting, in the second slot, the information to which has been applied the second cyclic shift corresponding to the symbols for the second slot and the orthogonal sequence for the second slot, wherein a slot comprises multiple symbols..Iaddend.
.Iadd.38. The method of claim 37, wherein the information is an acknowledgement or negative acknowledgement (ACK/NACK)..Iaddend.
.Iadd.39. The method of claim 37, wherein the first cyclic shift corresponding to the symbols for the first slot and the second cyclic shift corresponding to the symbols for the second slot are each defined based on at least one slot index..Iaddend.
.Iadd.40. The method of claim 37, wherein the orthogonal sequence for the first slot and the orthogonal sequence for the second slot are each defined based on at least one slot index..Iaddend.
.Iadd.41. The method of claim 37, wherein the information for the first slot is spread into symbols by applying the orthogonal sequence for the first slot..Iaddend.
.Iadd.42. The method of claim 37, wherein the orthogonal sequence for the second slot is obtained based on a first time index..Iaddend.
.Iadd.43. The method of claim 37, wherein the first cyclic shift corresponding to the symbols for the first slot, the second cyclic shift corresponding to the symbols for the second slot, the orthogonal sequence allocated for the first slot and the orthogonal sequence allocated for the second slot are obtained based on a number of cyclic shifts for an acknowledgement or negative acknowledgement (ACK/NACK) in one resource block..Iaddend.
.Iadd.44. The method of claim 43, wherein each cyclic shift except for a cyclic shift for the ACK/NACK in the one resource block is for channel quality information (CQI)..Iaddend.
.Iadd.45. An apparatus in a communication system, the apparatus comprising: a transmitter chain configured to: obtain an orthogonal sequence for a first slot and a first cyclic shift corresponding to all symbols for the first slot and a cell identifier; obtain an orthogonal sequence for a second slot and a second cyclic shift corresponding to all symbols for the second slot and the cell identifier; apply the first cyclic shift corresponding to the symbols for the first slot and the orthogonal sequence for the first slot to information for the first slot; apply the second cyclic shift corresponding to the symbols for the second slot and the orthogonal sequence for the second slot to information for the second slot; transmit, in the first slot, the information to which has been applied the first cyclic shift corresponding to the symbols for the first slot and the orthogonal sequence for the first slot; and transmit, in the second slot, the information to which has been applied the second cyclic shift corresponding to the symbols for the second slot and the orthogonal sequence for the second slot, wherein a slot comprises a multiple of symbols..Iaddend.
.Iadd.46. The apparatus of claim 45, wherein the information is an acknowledgement and negative acknowledgement (ACK/NACK)..Iaddend.
.Iadd.47. The apparatus of claim 45, wherein the first cyclic shift corresponding to the symbols for the first slot and the second cyclic shift corresponding to the symbols for the second slot are each defined based on at least one slot index..Iaddend.
.Iadd.48. The apparatus of claim 45, wherein the orthogonal sequence for the first slot and the orthogonal sequence for the second slot are each defined based on at least one slot index..Iaddend.
.Iadd.49. The apparatus of claim 45, wherein the information for the first slot is spread into symbols by applying the orthogonal sequence for the first slot..Iaddend.
.Iadd.50. The apparatus of claim 45, wherein the orthogonal sequence for the second slot is obtained based on a first time index..Iaddend.
.Iadd.51. The apparatus of claim 45, wherein the first cyclic shift corresponding to the symbols for the first slot, the second cyclic shift corresponding to the symbols for the second slot, the orthogonal sequence allocated for the first slot and the orthogonal sequence allocated for the second slot are obtained based on a number of cyclic shifts for an acknowledgement or negative acknowledgement (ACK/NACK) in one resource block..Iaddend.
.Iadd.52. The apparatus of claim 51, wherein each cyclic shift except for a cyclic shift for the ACK/NACK in the one resource block is for channel quality information (CQI)..Iaddend.
.Iadd.53. A method for receipt of information in a communication system, the method comprising: obtaining an orthogonal sequence for a first slot and a first cyclic shift corresponding to all symbols for the first slot and a cell identifier; obtaining an orthogonal sequence for a second slot and a second cyclic shift corresponding to all symbols for the second slot and the cell identifier; receiving, at the first slot, information based on the first cyclic shift corresponding to the symbols for the first slot and the orthogonal sequence for the first slot; and receiving, at the second slot, information based on the second cyclic shift corresponding to the symbols for the second slot and the orthogonal sequence for the second slot, wherein a slot comprises multiple symbols..Iaddend.
.Iadd.54. The method of claim 53, wherein the information is an acknowledgement or negative acknowledgement (ACK/NACK)..Iaddend.
.Iadd.55. The method of claim 53, wherein the first cyclic shift corresponding to the symbols for the first slot and the second cyclic shift corresponding to the symbols for the second slot are each defined based on at least one slot index..Iaddend.
.Iadd.56. The method of claim 53, wherein the orthogonal sequence for the first slot and the orthogonal sequence for the second slot are each defined based on at least one slot index..Iaddend.
.Iadd.57. The method of claim 53, wherein the information for the first slot is spread into symbols by applying the orthogonal sequence for the first slot..Iaddend.
.Iadd.58. The method of claim 53, wherein the orthogonal sequence for the second slot is obtained based on a first time index..Iaddend.
.Iadd.59. The method of claim 53, wherein the first cyclic shift corresponding to the symbols for the first slot, the second cyclic shift corresponding to the symbols for the second slot, the orthogonal sequence allocated for the first slot and the orthogonal sequence allocated for the second slot are obtained based on a number of cyclic shifts for an acknowledgement or negative acknowledgement (ACK/NACK) in one resource block..Iaddend.
.Iadd.60. The method of claim 59, wherein each cyclic shift except for the cyclic shift for ACK/NACK in the one resource block is for channel quality information (CQI)..Iaddend.
Description
BACKGROUND OF THE INVENTION
1. Field of the Invention
The present invention relates to methods and apparatus for remapping and regrouping transmission resources in a wireless communication system.
2. Description of the Related Art
The present invention incorporates by reference the following references:
[1] 3GPP RANI #50 Chairman's Notes, August 2007, Athens, Greece
[2] R1-073541, "UL ACK/NACK Structure, Samsung, RAN1#50, August 2007, Athens, Greece
[3] R1-073564, "Selection of Orthogonal Cover and Cyclic Shift for High Speed UL ACK Channels", Samsung, RAN1#50, August 2007, Athens, Greece
[4] R1-072225, "CCE to RE mapping", Samsung, RAN1#49, Kobe, May 2007
[5] R1-073412, "Randomization of intra-cell interference in PUCCH", ETRI, RAN1#50, Athens, August 2007
[6] R1-073413, "Sequence allocation and hopping for uplink ACK/NACK channels", ETRI, RAN1#50, Athens, August 2007
[7] R1-073661, "Signaling of implicit ACK/NACK resources", Nokia Siemens, Nokia, RAN1 #50, Athens, August 2007
Telecommunication enables transmission of data over a distance for the purpose of communication between a transmitter and a receiver. The data is usually carried by radio waves and is transmitted using a limited transmission resource. That is, radio waves are transmitted over a period of time using a limited frequency range.
In Third (3.sup.rd) Generation Partnership Project Long Term Evolution (3GPP LTE) systems, one type of the transmission resource used in the uplink control channel (PUCCH) is known as a Cyclic shift (CS) for each OFDM symbol. For example, the PUCCH occupies twelve subcarriers in one resource block (RB) and therefore twelve CS resources in one RB.
In addition, according to the current working assumption on the transmission block of UL acknowledgement (ACK) channel and reference signal (RS), acknowledgement and negative acknowledgement (ACK/NAK) signals and the uplink (UL) RS for ACK/NACK demodulation are multiplexed on the code channels constructed by both a cyclic shift (CS) of a base sequence and an orthogonal cover (OC). One example of base sequence is Zadoff-Chu sequence.
One important aspect of system design is resource remapping on a symbol, slot or subframe-level. Although some methods have been proposed in the past such as the remapping table based approach disclosed in Reference [5], the remapping table based approach requires the storage of the remapping table and is therefore not desirable. We attempt to find an efficient yet general method for resource remapping in this invention.
SUMMARY OF THE INVENTION
It is therefore an object of the present invention to provide improved methods and apparatus for wireless communication.
It is another object of the present invention to provide improved methods and apparatus for efficiently remapping and regrouping transmission resources in a wireless communication system.
According to one aspect of the present invention, a global resource mapping scheme is established between N resource combinations in a first time slot and N resource combinations in a second time slot in dependence upon a certain parameter n. The mapping scheme is established by: j=g(i,n), where i denotes the index of a resource combination in the first time slot and i=1, 2, . . . , N, j denotes the index of a resource combination in the second time slot and j=1, 2, . . . , N, and g(a,b) is a pseudo-random function.
The pseudo-random function may be a Galois Field based permutation function established by: j=g(i,n)=P.sub.G(i,n,N), where n is selected from a set of integers {1, 2, . . . , N}.
Alternatively, the pseudo-random function may be a Pruned Bit Reversal Ordering (PBRO) function established by: j=g(i,n)=PRBO(mod(i+n-1,N)+1,N).
The parameter n may be the same for all cells in the communication network.
Alternatively, the parameter n may be assigned to each cell in the communication network in dependence upon an identification of the cell.
Each of the resource combinations includes an orthogonal cover selected from a plurality of orthogonal covers and a cyclic shift of a base sequence selected from a plurality of cyclic shifts. A cell-specific symbol level cyclic shift hopping pattern may be established to shift the index of the cyclic shift within at least one resource combination on a modulation symbol in a subframe in a cell by an amount specified by h_sym(c_id,s_id,l_id). The post-shifting index v.sub.i' of the cyclic shift having a pre-shifting index of v.sub.i within an i-th resource combination is established by: v.sub.i'=cyclic_shift(v.sub.i,h_sym(c_id,s_id,l_id),K) where c_id denotes the identification of the cell, s_id denotes the identification of the subframe, l_id denotes the identification of the modulation symbol, K denotes the total number of the plurality of cyclic shifts, and cyclic_shift(a,b,N)=mod(a+b-1,N)+1 when the plurality of cyclic shifts are indexed as 1, 2, . . . , N.
The function h_sym(c_id,s_id,l_id) may be one of a Galois Field based permutation function established by: h_sym(c_id,s_id,l_id)=P.sub.G(x(l_id,K),r(c_id,n,K), and a Pruned Bit Reversal Ordering (PBRO) function established by: h_sym(c_id,s_id,l_id)=PBRO(mod(l_id+c_id+n-1,K)+1,K), where x(l_id,K)=mod(l_id-1,K)+1, and r(c_id,n,K)=mod(c_id+n-1,K)+1.
Alternatively, a cell-specific slot-level cyclic shift hopping pattern may be established to shift the index of the cyclic shift within at least one resource combination in a time slot in a cell by an amount specified by h_slot(c_id,sl_id). The post-shifting index v.sub.i' of the cyclic shift having a pre-shifting index of v.sub.i within an i-th resource combination is established by: v.sub.i'=cyclic_shift(v.sub.i,h_slot(c_id, sl_id),K) where c_id denotes the identification of the cell, sl_id denotes the identification of the time slot, K denotes the total number of the plurality of cyclic shifts, and cyclic_shift(a,b,N)=mod(a+b-1,N)+1 when the plurality of cyclic shifts are indexed as 1, 2, . . . , N. The function h_slot(c_id,sl_id) may be one of a Galois Field based permutation function established by: h_slot(c_id,sl_id)=P.sub.G(sl_id, r(c_id,n,K),K), and a Pruned Bit Reversal Ordering (PBRO) function established by: h_slot(c_id,sl_id)=PBRO(mod(sl_id+c_id+n-1,K)+1,K), where r(c_id,n,K)=mod(c_id+n-1,K)+1.
According to another aspect of the present invention, first, N resource combinations within each of a plurality of time slots are divided into K subsets, with a k-th subset including N.sub.k resource combinations, where k=1, 2, . . . , K. An ultra-subset resource mapping scheme is established between the resource combinations in the subsets in a first time slot and the resource combinations in the subsets in a second time slot in dependent upon a certain parameter vector n=[n.sub.1, n.sub.2, . . . , n.sub.K], where n.sub.k corresponds to a k-th subset. The mapping scheme is established by: i.sub.k,d=g(i,n)=g.sub.k(i.sub.k,c,n.sub.k), for k=1, 2, . . . , K where i=i.sub.k,c, i.sub.k,c denotes the index of a resource combination within the N resource combinations in the first time slot, k denotes the index of the subset where the i.sub.k,c-th resource combination is located, c denotes the index of the i.sub.k-th resource combination within the k-th subset, i.sub.k,d denotes the index of a resource combination within the N resource combinations in the second time slot, k denotes the index of the subset where the i.sub.k,d-th resource combination is located, d denotes the index of the i.sub.k,d-th resource combination within the k-th subset, i.sub.k,c=(k-1).times.N.sub.k+c, i.sub.k,d=(k-1).times.N.sub.k+d, and g(a,b) is a pseudo-random function.
According to yet another aspect of the present invention, first, N resource combinations within each of a plurality of time slots are divided into K subsets, with a k-th subset including N.sub.k resource combinations, where k=1, 2, . . . , K, and N.sub.1=N.sub.2= . . . =N.sub.K. An inter-subset interleaving scheme is established in at least one time slot in accordance with an interleaving parameter PG[s.sub.1, s.sub.2, . . . , s.sub.K]. The inter-subset interleaving scheme is established by: j=w(i,PG[s.sub.1,s.sub.2, . . . , s.sub.K]), for k=1, 2, . . . , K, where w(i,PG[s.sub.1, s.sub.2, . . . , s.sub.K]) denotes the i-th resource combination in the time slot after the interleaving in accordance with the interleaving parameter PG[s.sub.1, s.sub.2, . . . , s.sub.K], and the interleaving parameter PG[s.sub.1, s.sub.2, . . . , s.sub.K] indicates that a subset having a pre-interleaving index of s.sub.k has a post-interleaving index of k, and 1.ltoreq.s.sub.1, . . . , s.sub.K.ltoreq.K.
According to still another aspect of the present invention, a symbol-level cyclic shift mapping scheme is established between M cyclic shifts in a first modulation symbol in a transmission channel and M cyclic shifts in a second modulation symbol in the transmission channel in dependence upon a certain parameter n. The first modulation symbol has an identification number of 1, and the second modulation symbol has an identification number of more than 1. The symbol-level cyclic shift mapping scheme is established by: m'=t(m,l_id, n), for l_id>1, where m denotes the index of a cyclic shift within the first modulation symbol and m=1, 2, . . . , M, m' denotes the index of a cyclic shift within the second modulation symbol and m'=1, 2, . . . , M, l_id denotes the identification number the second modulation symbol, and t(a, b, c) is a pseudo-random function.
According to still yet another aspect of the present invention, a slot-level cyclic shift mapping scheme is established between M cyclic shifts in a first time slot in a transmission channel and M cyclic shifts in a second time slot in the transmission channel in dependence upon a certain parameter n. The slot-level cyclic shift mapping scheme is established by: m'=g(m,n), where m denotes the index of a cyclic shift within the first time slot and m=1, 2, . . . , M, m' denotes the index of a cyclic shift within the second time slot and m'=1, 2, . . . , M, and g(a,b) is a pseudo-random function.
According to a further aspect of the present invention, a subframe-level base sequence mapping scheme is established between Z base sequences in a first subframe in a transmission channel and Z base sequences in a second subframe in the transmission channel in dependence upon a certain parameter n. The first subframe has an identification number of 1, and the second subframe has an identification number of more than 1. The subframe-level base sequence mapping scheme is established by: z'=s(z, s_id, n), for s_id>1, where z denotes the index of a base sequence within the first subframe and z=1, 2, . . . , Z, z' denotes the index of a base sequence within the second subframe and z'=1, 2, . . . , Z, s_id denotes the identification number the second subframe, and s(a, b, c) is a pseudo-random function.
According to a still further aspect of the present invention, a slot-level base sequence mapping scheme is established between Z base sequences in a first time slot and Z base sequences in a second time slot 1 in dependence upon a certain parameter n. The first time slot has an identification number of 1, and the second time slot has an identification number of more than 1. The slot-level base sequence mapping scheme is established by: z'=s(z, sl_id, n), for sl_id>1, where z denotes the index of a base sequence within the first time slot and z=1, 2, . . . , Z, z' denotes the index of a base sequence within the second time slot and z'=1, 2, . . . , Z, sl_id denotes the identification number the second time slot, and s(a,b,c) is a pseudo-random function.
BRIEF DESCRIPTION OF THE DRAWINGS
A more complete appreciation of the invention, and many of the attendant advantages thereof, will be readily apparent as the same becomes better understood by reference to the following detailed description when considered in conjunction with the accompanying drawings in which like reference symbols indicate the same or similar components, wherein:
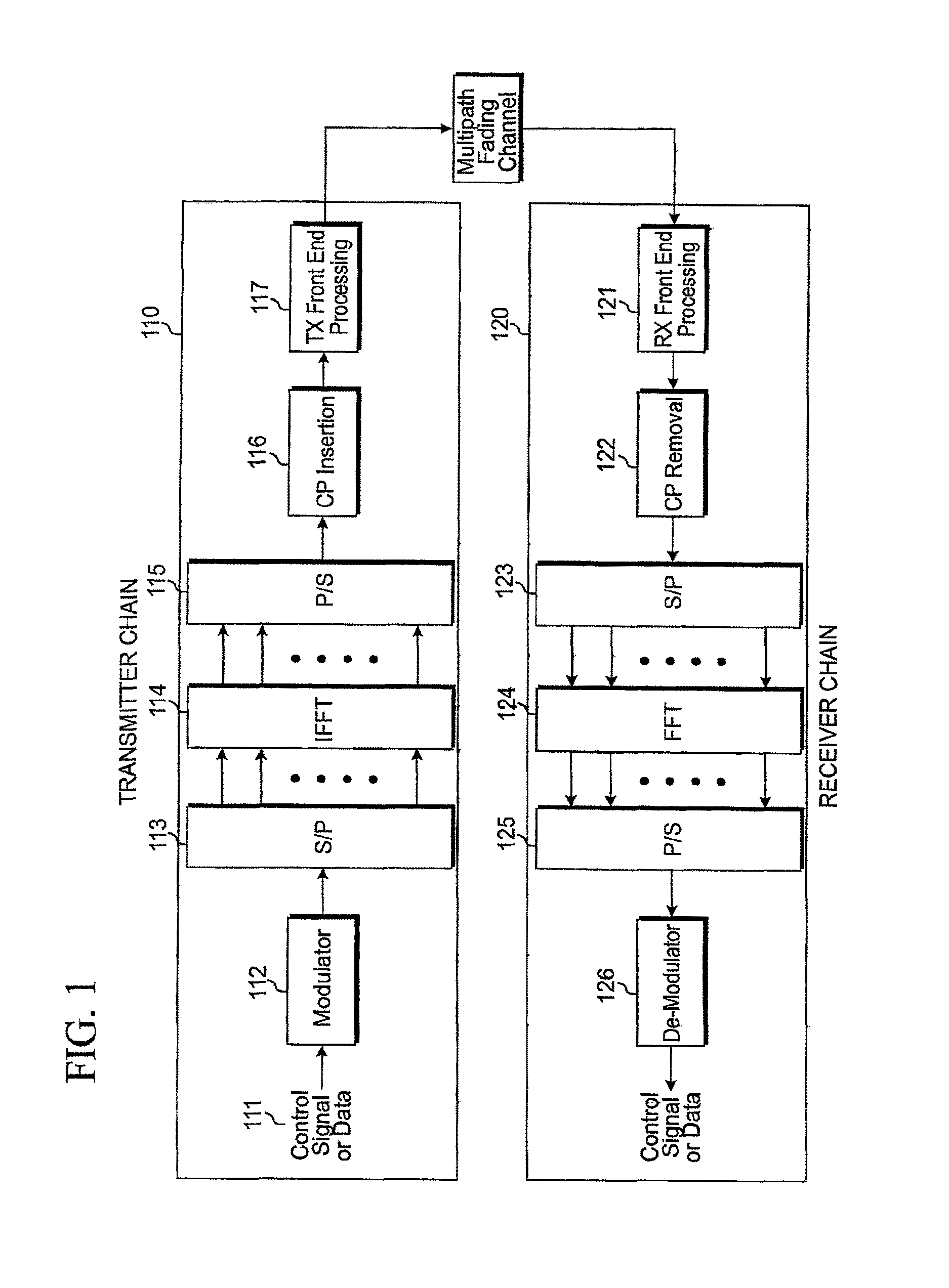
FIG. 1 is an illustration of an Orthogonal Frequency Division Multiplexing (OFDM) transceiver chain suitable for the practice of the principles of the present invention;
FIG. 2 schematically illustrates an example of multiplexing six units of user equipments (UEs) within one resource block (RB); and
FIG. 3 schematically illustrates the current working assumption on the uplink acknowledgement and reference signal channels.
DETAILED DESCRIPTION OF THE INVENTION
FIG. 1 illustrates an Orthogonal Frequency Division Multiplexing (OFDM) transceiver chain. In a communication system using OFDM technology, at transmitter chain 110, control signals or data 111 is modulated by modulator 112 into a series of modulation symbols, that are subsequently serial-to-parallel converted by Serial/Parallel (S/P) converter 113. Inverse Fast Fourier Transform (IFFT) unit 114 is used to transfer the signals from frequency domain to time domain into a plurality of OFDM symbols. Cyclic prefix (CP) or zero prefix (ZP) is added to each OFDM symbol by CP insertion unit 116 to avoid or mitigate the impact due to multipath fading. Consequently, the signal is transmitted by transmitter (Tx) front end processing unit 117, such as an antenna (not shown), or alternatively, by fixed wire or cable. At receiver chain 120, assuming perfect time and frequency synchronization are achieved, the signal received by receiver (Rx) front end processing unit 121 is processed by CP removal unit 122. Fast Fourier Transfinni (FFT) unit 124 transfers the received signal from time domain to frequency domain for further processing.
The total bandwidth in an OFDM system is divided into narrowband frequency units called subcarriers. The number of subcarriers is equal to the FFT/IFFT size N used in the system. In general, the number of subcarriers used for data is less than N because some subcarriers at the edge of the frequency spectrum are reserved as guard subcarriers. In general, no information is transmitted on guard subcarriers.
On the uplink (UL) of the Third Generation Partnership Project (3GPP) long term evolution (LTE) standard, one type of the resource used in the uplink control channel (PUCCH) is known as a Cyclic shift (CS) for each OFDM symbol. For example, the PUCCH occupies twelve subcarriers in one resource block (RB) and therefore we have twelve CS resources in one RB. One example of multiplexing six units of user equipment (UEs) in one RB is shown in FIG. 2. Note that only six out twelve CSs are used in this example.
FIG. 3 illustrates the current working assumption on the transmission block of UL acknowledgement (ACK) channel and reference signal (RS). ACK/NAK signals and the UL RS for ACK/NACK demodulation are multiplexed on the code channels constructed by both a cyclic shift (CS) of a base sequence and an orthogonal cover (OC). One example of base sequence is Zadoff-Chu sequence.
One important aspect of system design is resource remapping on a symbol, slot or subframe-level. Although some methods have been proposed in the past such as the remapping table based approach disclosed in Reference [5], the remapping table based approach requires the storage of the remapping table and is therefore not desirable. We attempt to find an efficient yet general method for resource remapping in this invention.
In this invention, we first propose a set of new permutation algorithms, then propose to apply these algorithms and the known Pruned Bit Reversal Ordering (PBRO) algorithm, to several various resource remapping/regrouping problems, including slot or symbol level Orthogonal Cover (OC)/Cyclic Shift (CS) remapping, generation of cell-specific slot and symbol-level CS hopping patterns, and generation of subframe and slot level base sequence hopping patterns.
In addition, we note that the Pruned Bit Reversal Ordering (PBRO, or some times known as PBRI with "I" stands for interleaving) is a known method and has been used in many applications, for example, CCE to resource element (RE) mapping disclosed in Reference [4]. The PBRO method generates a permutation y=PBRO(i, M) of a sequence of {1, 2, . . . , M} of size M where y is the output value corresponding to the input value i. The PBRO is defined as follows: 1. Let i=i-1 such that i belongs to the sequence {0, 1, . . . , M-1}. Determine the PBRO parameter, n, where n is the smallest integer such that M.ltoreq.2.sup.n. 2. Initialize counters i and j to 0. 3. Define x as the bit-reversed value of j using an n-bit binary representation. For example, if n=4 and j=3, then x=12. 4. If x<M, set PBRO(i,M) to x and increase i by 1. 5. Increment the counter j. 6. If i<M go to step 3. Other wise go to steo 7. 7. Let j=j+1, such that j belong to the set {1, 2, . . . M}.
Aspects, features, and advantages of the invention are readily apparent from the following detailed description, simply by illustrating a number of particular embodiments and implementations, including the best mode contemplated for carrying out the invention. The invention is also capable of other and different embodiments, and its several details can be modified in various obvious respects, all without departing from the spirit and scope of the invention. Accordingly, the drawings and description are to be regarded as illustrative in nature, and not as restrictive. The invention is illustrated by way of example, and not by way of limitation, in the figures of the accompanying drawings.
1. Proposed Permutation Algorithm
In a first embodiment according to the principles of the present invention, we propose a resource permutation function that is based on Galois field operations. Let N be the total number of resources being permuted, the operation of permutation function is given by: j=P.sub.G(i,n,N) (1) where i=1, . . . , N is the index of the input resource index, j=1, . . . , N is the output resource index, and n=1, . . . , N is the permutation sequence index, since a different n provides a different permuted output.
We first consider a case where N is an integer that satisfies N=p.sup.m-1, where p is a prime number and m is a positive integer. In this case, Galois field N+1 exists and we denote it by GF(N+1). In addition, we can find a primitive element of this Galois field and call the primitive element a which satisfies .alpha..sup.N=.alpha..sup.p.sup.n.sub.-1=1, and .alpha. is an integer. In addition, all N non-zero elements in the GF(N+1) can be expressed as an exponent of .alpha., or in another word, the sequence .alpha..sup.0, .alpha..sup.1, . . . , .alpha..sup.N-1 includes all N non-zero elements in GF(N+1). Therefore, any input resource number i can be expressed as a power of the primitive element i=.alpha..sup.k for some integer k such that 0.ltoreq.k.ltoreq.N-1. With this notation, the output of the resource permutation function P.sub.G(i,n,N) is given by: j=P.sub.G,1(i,n,N)=.alpha..sup.mod(k+n=1,N), for i=1, . . . , N, and n=1, . . . , N, (2) where mod(a,b) is the modular operation applied on the two integers a and b. Another similar permutation function can be found as: j=P.sub.G,2(i,n,N)=.alpha..sup.mod(k-(n-1),N), for i=1, . . . , N, and n=1, . . . , N (3) Note that we can resort to finite field calculation to find out the natural number representation of j in the above equation.
On the other hand, we consider the special case where N is an integer that satisfies N=p.sup.1-1, where p is a prime number. In this case, Galois field N+1, i.e., GF(N+1), also exists and is also a ground Galois field. In this, we propose a simpler approach of finding the output permuted resource: j=P.sub.G,3(i,n,N)=mod(i.times.n,N+1), for i=1, . . . , N and n=1, . . . , N. (4)
Furthermore, if N does not satisfy N=p.sup.m-1, for some prime number p and positive integer m, then we propose the following Pruned GF field based approach which we denote by P.sub.G,4a(i,n,N): Step 1: Find the smallest integer M>N such that M satisfies M=p.sup.m-1 where p is a prime number and m is positive. Form Galois field GF(M+1), find the primitive element .alpha. of GF(M+1). Set variables u=1, and v=1. Step 2: Find win such a way: if M=p.sup.m-1 where p is prime and m>1, then w can be generated by either w P.sub.G,1(n,n,M) or w=P.sub.G,2(v,n,M); if M=p-1 where p is prime, then w can generated by one of the three functions above: w=w=P.sub.G,2(v,n,M) and w=P.sub.G,3(v,n,M). Step 3: if w>N, let v=v+1, go to Step 2; else go to Step 4 Step 4: if u=i, go to Step 5; otherwise let u=u+1, v=v+1 and go to Step 2. Step 5: We have obtained the output resource index j=w=P.sub.G,4a(i,n,N).
We also propose a similar method for the case where N does not satisfy N=p-1, for some prime number p, then we propose the following Pruned Ground GF field based approach which we denote by P.sub.G,4b(i,n,N): Step 1: Find the smallest M>N such that M satisfies M=p-1 where p is a prime number. Set variables u=1, and v=1. Step 2: Find w by w=P.sub.G,3(v,n,M). Step 3: if w>N, let v=v+1, go to Step 2; else go to Step 4. Step 4: if u=i, go to Step 5; otherwise let u=u+1, v=v+1 and go to Step 2. Step 5: We have obtained the output resource index=P.sub.G,4b(i,n,N).
Let us now summarize the proposed permutation function. Therefore, for a set of inputs i, n, N, where 1.ltoreq.i.ltoreq.N and 1.ltoreq.n.ltoreq.N, the permutation output is given by the function:
.function..function..times..times..times..times..function..times..times..- times..times..times..times..times..times..function..times..times..function- ..times..times..times..times..function..times..times..times..times..times.- .times..times..times..times..times..times..function..times..times..times..- times.>.times..function..times..times..times..function..times..times..t- imes..times..times..times..times..times..times..times..times..times..times- ..times..times..times..times..times..times..times..times..times.> ##EQU00001##
Noteworthy, in the above methods, we have assumed input and output resources are indexed as i=1, . . . , N, and j=1, . . . , N. If the input index i' and output j' are indexed as i'=0, . . . , N-1 and j'=0, . . . , N-1 instead, then the above equation should be used in the following way: j'=P.sub.G(i'+1, n,N)-1; for i'=0, . . . , N-1, j'=0, . . . , N-1, and n=1, . . . , N. (6)
2. Slot-Level Resource Remapping for Orthogonal Cover/Cyclic Shift Combinations
We first consider the case where there are a total of N resources available in each of the two slots in the uplink control channel, and each resource is defined as a combination of orthogonal cover and cyclic shift (OC/CS combo). An example of the application of this type of resource combo assignment is the uplink ACK/NACK channel. Note that the uplink service grant request channel may reuse the structure of uplink ACK/NACK channel. Another example of application of this type of resource combo assignment is the uplink demodulation reference symbols (RS).
One example of Orthogonal cover is Walsh-Hadmard code.
On the other hand, cyclic shift (CS) is typically applied on a base sequence, examples of base sequences include ZC (Zadoff-Zhu) code and computer generated CAZAC codes. For any base sequence of length N, there are N cyclic shifts, or N CS resources.
Let us start off by denote the OC/CS combo as CB hereafter. The N resource combos are given by: CB.sub.a[i]=OC.sub.a[u.sub.i],CS.sub.a[v.sub.i], for i=1, . . . , N, and a=1, 2, (7) where u.sub.i and v.sub.i indicate the OC and CS indices for the ith resource combo, respectively. In addition, a=1, 2 is the slot index within a subframe for the 3GPP LTE uplink transmission.
2.1 Global Resource Remapping
In a second embodiment according to the principles of the present invention, let there be N OC/CS resource combos in both slots of an uplink subframe. We propose to associate the OC/CS resource combos in such a way that if a UE picks the resource combo CAN in the first slot, then the UE must be assigned CB.sub.2[g(i,n)] in the second slot, where g(i,n) is a pseudo-random resource remapping/permutation function, and n is a parameter.
In a first sub-embodiment of the second embodiment according to the principles of the present invention, the pseudo-random permutation function is established as: g(i,n)=P.sub.G(i,n,N), (8) where n is chosen from the set {1, 2, . . . , N}, or n=1, . . . , N. The function P.sub.G(i,n,N) is defined in the previous section.
In a second sub-embodiment of the second embodiment according to the principles of the present invention, the pseudo-random permutation function uses the PBRO function in such a way: g(i,n)=PBRO(mod(i+n-1,N)+1,N) (9) The function PBRO(a,b) is defined previously, and n is chosen from the set {1, 2, . . . , N}.
In a third sub-embodiment of the second embodiment according to the principles of the present invention, the parameter n in the above two sub-embodiments is the same for all cells. The parameter n can be communicated to the UE by means of higher-layer signaling.
In a fourth sub-embodiment of the second embodiment according to the principles of the present invention, the parameter n is a function of CELL ID (c_id), denoted by n=f(c_id). Therefore, for a different c_id, we will have a different parameter n. One example of such a function is n=mod(c_id-1,N)+1.
Before we show an example for these above embodiments, we provide a table of four OC subsets S.sub.1, S.sub.2, S.sub.3 and S.sub.4 as is disclosed in Reference [3]. The three codes in each subsets are denoted as S.sub.i(A), S.sub.i(B), and S.sub.i(C).
TABLE-US-00001 TABLE 1 Equivalent mapping between all sets of three OCs. Four subsets A B C S.sub.1 c2 c3 c1 S.sub.2 c1 c4 c2 S.sub.3 c4 c1 c3 S.sub.4 c3 c2 c4
where the set of OC codes are given by Walsh codes according to Reference [3]: c1=0.5.times.[1, 1, 1, 1]; c2=0.5.times.[1, -1, 1, -1]; c3=0.5.times.[1, 1, -1, -1]; c4=0.5.times.[1, -1, -1,1]. (10)
We now proceed with one example application of the embodiments. First, the allocation/definition of resource OC/CS combos are given in the Table 2 with N=18, as presented in Reference [3].
TABLE-US-00002 TABLE 2 OC/CS Resource Combinations defined on two slots, N = 18. Cyclic Resource Combos Resource Combos shift in slot #1 - CB1[ ] in Slot #2 - CB2[ ] value OC1[1] OC1[2] OC1[3] OC2[1] OC2[2] OC2[3] 0 CB1[1] [13] CB2[1] [13] 1 [7] [7] 2 [2] [14] [2] [14] 3 [8] [8] 4 [3] [15] [3] [15] 5 [9] [9] 6 [4] [16] [4] [16] 7 [10] [10] 8 [5] [17] [5] [17] 9 [11] [11] 10 [6] [18] [6] [18] 11 [12] [12]
Note here OC.sub.1[1], OC.sub.1[2], OC.sub.1[3] are the three OC codes used in slot 1, and OC.sub.2[1], OC.sub.2[2], OC.sub.2[3] are the three OC codes used in slot 2. In general, the OC codes in each slot can be an arbitrary subset of the four length-4 Walsh codes {c1, c2, c3, c4} defined in Table 1. One example of the OC codes selection is such that the OC codes in the first slot is given by OC.sub.1[1]=S.sub.i(A), OC.sub.1[2]=S.sub.i(C), OC.sub.1[3]=S.sub.i(B), and the OC codes in the second slot is given by OC.sub.2[1]=S.sub.j(A), OC.sub.2[2]=S.sub.i(C), OC.sub.2[3]=S.sub.j(B) for a pair of integers (i, j) (Reference [3]). For example, if i=j=2, then we have OC.sub.1[1]=OC.sub.2[1]=S.sub.2(A)=c1; OC.sub.1[2]=OC.sub.2[2]=S.sub.2(C)=c2; and OC.sub.1[3]=OC.sub.2[3]=S.sub.2(B)=c4.
We now find the association/remapping between the resource combos in slot 1 and slot 2 in this example of 18 OC/CS combos in Table 2. Note the same association/remapping is applicable to any other case where there are N=18 OC/CS combinations, such as the alternative allocation scheme shown in Table 18 in the Annex. Since N=18 and N+1=19 is a prime number and GF(19) is a ground Galois field, we can use g(i,n)=P.sub.G,3(i,n,18)=mod(i.times.n,19) as the permutation function g(i,n) that associates the slot 1 resource CB.sub.1[i] and slot 2 resource CB.sub.2[g(i,n)]. This resource remapping function is shown in Table 3 below. Note that only n=1 to n=4 are shown, other parameter values n=5 to n=18 can also be used in generating the function g(i,n).
TABLE-US-00003 TABLE 3 Resource permutation/remapping function g(i, n) as a function of parameter n. N = 18. i 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 g(i, n), n = 1 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 g(i, n), n = 2 2 4 6 8 10 12 14 16 18 1 3 5 7 9 11 13 15 17 g(i, n), n = 3 3 6 9 12 15 18 2 5 8 11 14 17 1 4 7 10 13 16 g(i, n), n = 4 4 8 12 16 1 5 9 13 17 2 6 10 14 18 3 7 11 15
In another example, we have N=12, or 12 OC/CS resource combos in each slot, as shown in Table 4 below.
TABLE-US-00004 TABLE 4 OC/CS Resource Combinations defined on two slots, presented in Reference [3]. N = 12. Resource Combos Resource Combos Cyclic shift in slot #1 - CB.sub.1[ ] in Slot #2 - CB.sub.2[ ] value OC.sub.1[1] OC.sub.1[2] OC.sub.1[3] OC.sub.2[1] OC.sub.2[2] OC.sub.2- [3] 0 CB.sub.1[1] CB.sub.2[1] 1 [5] [5] 2 [9] [9] 3 [2] [2] 4 [6] [6] 5 [10] [10] 6 [3] [3] 7 [7] [7] 8 [11] [11] 9 [4] [4] 10 [8] [8] 11 [12] [12]
We now find the association between the resource combos in slot 1 and slot 2 in this example of Table 4. Note the same association/remapping is applicable to any other case where there are N=12 OC/CS combinations, Since N=12 and N+1=13 is a prime number and GF(13) is a ground Galois field, we can use g(i,n)=P.sub.G,3(i,n,12)=mod(i.times.n,13) as the permutation function g(i,n) that associates the slot 1 resource CB.sub.1[i] and slot 2 resource CB.sub.2[g(i,n)]. This resource remapping function is shown in Table 5 below. Note that only n=1 to n=3 are shown, other parameter values n=5 to n=12 can also be used in generate the function g(i,n).
TABLE-US-00005 TABLE 5 Resource permutation/remapping function g(i, n) as a function of parameter n. N = 12 i 1 2 3 4 5 6 7 8 9 10 11 12 g(i, n), n = 1 1 2 3 4 5 6 7 8 9 10 11 12 g(i, n), n = 2 2 4 6 8 10 12 1 3 5 7 9 11 g(i, n), n = 3 3 6 9 12 2 5 8 11 1 4 7 10
In a third embodiment according to the principles of the present invention, we propose to assign the subset S.sub.i and S.sub.j to slot 1 and 2 in a subframe, for all UEs within a give cell. In addition, we propose to associate the indices of subsets, i and j, with the CELL ID, denoted by c_id. One example of this association is: i=mod(c_id-1,4)+1, and j=mod(i+n-1,4)+1 (11) where n is a positive integer. Once the indices i and j are available, for this cell whose CELL ID is c_id, we let: OC.sub.1[1]=S.sub.i(A), OC.sub.1[2]=S.sub.i(C), OC.sub.1[3]=S.sub.i(B), (12) for the first slot, and let: OC.sub.2[1]=S.sub.j(A), OC.sub.2[2]=S.sub.j(C), OC.sub.2[3]=S.sub.j(B) (13) for the second slot.
Note that this embodiment applies to, for example, both N=18 and N=12 examples shown in Table 2 and Table 4 above.
2.2 Intra-Subset Resource Remapping
In a fourth embodiment according to the principles of the present invention, we propose to divide the N resources into K subsets, with a k-th subset having N.sub.k elements (k=1, 2, . . . , K), such that
.times. ##EQU00002## Furthermore, the subsets in slot#1 and slot #2 have the same indices. The formation of these subsets is shown in Table 6 below.
TABLE-US-00006 TABLE 6 Dividing the N OC/CS resource combos into subsets. Resources Combos in Slot #1 Resources Combos in Slot #2 Subset 1 {CB.sub.1[i.sub.1,1], . . . , CB.sub.1[i.sub.1,N.sub.1]} {CB.sub.2[i.sub.1,1], . . . , CB.sub.2[i.sub.1,N.sub.1]} Subset 2 {CB.sub.1[i.sub.2,1], . . . , CB.sub.1[i.sub.2,N.sub.2]} {CB.sub.2[i.sub.2,1], . . . , CB.sub.2[i.sub.2,N.sub.2]} . . . . . . . . . subset K {CB.sub.1[i.sub.K,1], . . . , CB.sub.1[i.sub.K,N.sub.K]} {CB.sub.2[i.sub.K,1], . . . , CB.sub.2[i.sub.K,N.sub.K]}
Furthermore, we propose to associate the OC/CS resource combos in such a way that a resource combo in subset #k, slot #1 have to permute to a resource combo in subset #k, slot #2. If a UE picks the resource combo CB.sub.1[i.sub.k,c] in the first slot (1.ltoreq.c.ltoreq.N.sub.k) that belongs to subset #k within slot #1, then the UE must be assigned CB.sub.2[g.sub.k(i.sub.k,c,n.sub.k)] in the second slot, where g.sub.k(i.sub.k,c,n.sub.k) is a pseudo-random resource remapping/permutation function for subset #k, and n.sub.k is a parameter for subset #k. Note that i.sub.k,c=(k-1).times.N.sub.k+c. Furthermore, CB.sub.2[g.sub.k(i.sub.k,c,n.sub.k)] also must be a part of the subset #k within slot #2, such that g.sub.k(i.sub.k,c,n.sub.k)=i.sub.k,d holds for some 1.ltoreq.d.ltoreq.N.sub.k. We proceed to show how to derive output resource index i.sub.k,d for each input index i.sub.k,c (derive variable d from variable c). Note that i.sub.k,d=(k-1).times.N.sub.k+d.
In a first sub-embodiment of the fourth embodiment according to the principles of the present invention, the resource remapping/permutation within each subset uses the Galois Field based permutation function proposed earlier in Section 1. In each subset k, we associate/remap the two resources CA [i.sub.k,c] and CB.sub.2[g.sub.k(i.sub.k,c,n.sub.k)] according to: g.sub.k(i.sub.k,c,n.sub.k)=i.sub.k,d, where d=P.sub.G(c,n.sub.k,N.sub.k) for k=1, . . . , K. (14) Note that here n.sub.k is a parameter for subset k such that 1.ltoreq.n.sub.k.ltoreq.N.sub.k. We can further collect all these parameters into a vector form n=[n.sub.1, . . . , n.sub.K], the total number of possible parameter vectors is the product N.sub.1.times.N.sub.2.times. . . . .times.N.sub.K. Furthermore, summarizing the resource remapping in all subsets, then for each parameter vector n, we have defined the overall remapping function over the whole resource set, which we denote as g(i,n) and provide association/remapping between any resource CB.sub.1[i] in slot #1, and resource CB.sub.2[g(i,n)]. The function g(i,n) is defined by first finding the subset k where i belongs, that is, by finding a subset where there is some c, such that i=i.sub.k,c, furthermore, g(i,n)=g.sub.k(i.sub.k,c,n.sub.k), for the k, c such that i=i.sub.k,c. (15)
In a second sub-embodiment of the fourth embodiment according to the principles of the present invention, the pseudo-random permutation function uses the PBRO function in such a way: g(i.sub.k,c,n.sub.k)=i.sub.k,d, where d=PBRO(mod(c+n.sub.k-1)+1,N.sub.k). (16) The function PBRO(a,b) is defined in the introduction, and n.sub.k is chosen from the set {1, 2, . . . , N}.
In a third sub-embodiment of the fourth embodiment according to the principles of the present invention, the parameter vector n=[n.sub.1, . . . , n.sub.K] used in the above two sub-embodiments is the same for all cells. The parameter vector n=[n.sub.1, . . . , n.sub.K] can be communicated to the UE by means of higher-layer signaling.
In a fourth sub-embodiment of the fourth embodiment according to the principles of the present invention, the parameter vector n=[n.sub.1, . . . , n.sub.K] is a function of CELL ID, denoted by n=f(c_id). Therefore, for a different c_id, we can have a different parameter vector n=[n.sub.1, . . . , n.sub.K]. One example of such a function is: n.sub.k=mod(c_id-1,N.sub.k)+1. (17)
As an example, we apply this set of embodiments is to the 18 resources in Table 2. We first divide them into K=3 groups, with six resources in each group, i.e. N.sub.1=N.sub.2=N.sub.3=6. The division of the resources is shown in Table 7. Note in this example, all OC/CS combos that belong to the same OC code are grouped into a subset, for a given slot.
TABLE-US-00007 TABLE 7 One example of dividing the resources in Table 2 into 3 groups, each with 6 resources. Resources Combos Resources Combos in Slot #1 in Slot #2 Subset 1 {CB.sub.1[1], . . . , CB.sub.1[6]} {CB.sub.2[1], . . . , CB.sub.2[6]} Subset 2 {CB.sub.1[7], . . . , CB.sub.1[12]} {CB.sub.2[7], . . . , CB.sub.2[12]} subset K {CB.sub.1[13], . . . , CB.sub.1[18]} {CB.sub.2[13], . . . , CB.sub.2[18]}
In addition, the slot-level resource remapping can be tabulated in the below. Here we have used the permutation equation d=P.sub.G(c,n.sub.k,N.sub.k) to derive index i.sub.k,d from each input index i.sub.k,c. In particular, we have used the option d=P.sub.G,3(c,n.sub.k,N.sub.k)=mod(c.times.n.sub.k,N.sub.k+1) since N.sub.k+1=7 is a prime number and GF(7) is a ground Galois field.
TABLE-US-00008 TABLE 8(a) Resource re-mapping for subset 1 Resource index in slot #2 Resource index in slot #1 i.sub.1,d = g.sub.1(i.sub.1,c, n.sub.1) i.sub.1,c = 1 i.sub.1,c = 2 i.sub.1,c = 3 i.sub.1,c = 4 i.sub.1,c = 5 i.sub.1,c = 6 n.sub.1 = 1 1 2 3 4 5 6 n.sub.1 = 2 2 4 6 1 3 5 n.sub.1 = 3 3 6 2 5 1 4 n.sub.1 = 4 4 1 5 2 6 3 n.sub.1 = 5 5 3 1 6 4 2 n.sub.1 = 6 6 5 4 3 2 1
TABLE-US-00009 TABLE 8(b) Resource remapping for subset 2. Resource index in slot #2 Resource index in slot #1 i.sub.2,d = g.sub.2(i.sub.2,c, n.sub.2) i.sub.2,c = 7 i.sub.2,c = 8 i.sub.2,c = 9 i.sub.2,c = 10 i.sub.2,c = 11 i.sub.2,c = 12 n.sub.2 = 1 7 8 9 10 11 12 n.sub.2 = 2 8 10 12 7 9 11 n.sub.2 = 3 9 12 8 11 7 10 n.sub.2 = 4 10 7 11 8 12 9 n.sub.2 = 5 11 9 7 12 10 8 n.sub.2 = 6 12 11 10 9 8 7
TABLE-US-00010 TABLE 8(c) Resource remapping for subset 3, Resource index Resource index in slot #1 in slot #2 i.sub.3,c = 13 i.sub.3,c = 14 i.sub.3,c = 15 i.sub.3,c = 16 i.sub.3,c = 17 i.sub.3,c = 18 i.sub.3,d = g(i.sub.3,c), 13 14 15 16 17 18 n.sub.3 = 1 i.sub.3,d = g(i.sub.3,c), 14 16 18 13 15 17 n.sub.3 = 2 i.sub.3,d = g(i.sub.3,c), 15 18 14 17 13 16 n.sub.3 = 3 i.sub.3,d = g(i.sub.3,c), 16 13 17 14 18 15 n.sub.3 = 4 i.sub.3,d = g(i.sub.3,c), 17 15 13 18 16 14 n.sub.3 = 5 i.sub.3,d = g(i.sub.3,c), 18 17 16 15 14 13 n.sub.3 = 6
As we seen in the table above, since N.sub.1=N.sub.2=N.sub.3=6, there are six possible remapping functions within each subset. Therefore, there are a total of 6.sup.3 parameter vectors n, and thus 6.sup.3 possible resource remapping function g(i,n) over the overall set of eighteen OC/CS combos. We will only list in the table below three examples including n=[n.sub.1,n.sub.2,n.sub.3]=[2,2,2], or [1,2,3], or [2,3,4].
TABLE-US-00011 TABLE 9 Overall resource remapping table, where re-mappings take place within each subsets. Resource index in second slot Resource in the first slot, i g(i, n) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 n = [n.sub.1, n.sub.2, n.sub.3] = 1 2 3 4 5 6 8 10 12 7 9 11 15 18 14 17 13 16 [1, 2, 3] n = [n.sub.1, n.sub.2, n.sub.3] = 2 4 6 1 3 5 8 10 12 7 9 11 14 16 18 13 15 17 [2, 2, 2] n = [n.sub.1, n.sub.2, n.sub.3] = 2 4 6 1 3 5 9 12 8 11 7 10 16 13 17 14 18 15 [2, 3, 4]
2.3 Inter-Subset Switching
In a fifth embodiment according to the principles of the present invention, we propose to divide the N resources into K subsets, with each subset having N.sub.1,N.sub.2, . . . , N.sub.K elements and such that
.times. ##EQU00003## Furthermore, the subsets in slot#1 and slot #2 have the same indices. The formation of these subsets are shown in Table 6, similar to the previous embodiment. In addition, in this embodiment, we assume the number of elements within each subset to be the same, i.e., N.sub.1=N.sub.2= . . . =N.sub.K.
We now propose a resource remapping scheme where we perform a subset-wise switching between different subsets. We denote this operation by PG[s.sub.1, s.sub.2, . . . , s.sub.K] where 1.ltoreq.s.sub.1, . . . , s.sub.K.ltoreq.K are indices that indicate the switching pattern in the following way: subset # s.sub.1 in the first slot is remapped to subset #1 in the second slot, #s.sub.2 in the first slot is remapped to subset #2 in the second slot, etc. The intra-subset index of each resource element does not change in this switching operation. If a resource in the first slot is denoted by CB.sub.1[i], then after remapping, the resource is denoted by CB.sub.2[w(i,PG[s.sub.1, s.sub.2, . . . , s.sub.K])] (or concisely, CB.sub.2[w(i,PG[ ])]) in the second slot. In other words, if a UE picks the resource combination CB.sub.1[i] in the first slot, then it must be assigned CB.sub.2[g(w(i,PG[s.sub.1, s.sub.2, . . . , s.sub.K]),n)] i n the second slot.
In a first sub-embodiment of the fifth embodiment according to the principles of the present invention, the inter-subset switching pattern PG[s.sub.1, s.sub.2, . . . , s.sub.K.] is the same for all cells. The parameter PG[s.sub.1, s.sub.2, . . . , s.sub.K.] can be communicated to the UE by means of higher-layer signaling.
In a second sub-embodiment of the fifth embodiment according to the principles of the present invention, the inter-subset switching pattern PG[s.sub.1, s.sub.2, . . . , s.sub.K] is a function of CELL ID, denoted by PG[s.sub.1, s.sub.2, . . . , s.sub.K.]=e(c_id). Therefore, for a different c_id, we can have a different inter-subset switching pattern PG[s.sub.1, s.sub.2, . . . , s.sub.K].
For example, we can divide the eighteen OC/CS resources as shown in Table 2 into three subsets in each slot. In this example, each subset corresponds to all the resource combos on one OC code. The three subsets in slot #1 are given by G1[1]={CB.sub.1[1], . . . , CB.sub.1[6]}, G1 [2]={CB.sub.1[7], . . . , CB.sub.1[12]} and G1[3]={CB.sub.1[13], . . . , CB.sub.1[18]}. The subsets in slot #2 are similarly defined as G2[1], G2[2] and G2[3]. We now denote PG[2,3,1] as a subset-wise resource-mapping that maps the resources in subset G1[2] to subset G2[1], subset G1[3] to G2[2] and subset G1[1] to subset G2[3], etc. Similarly we can define PG[1,3,2], PG[2,1,3], PG[3,1,2], PG[3,2,1]. Several examples of the function g(i, PG[.]) that associates the resource combo CB.sub.1[i] in the first slot and CB.sub.2[w(i,PG[ ])] in the second slot are given in Table 10.
TABLE-US-00012 TABLE 10 Example of subset-wise resource switching Resource index in second slot, w(i, Resource index in the first slot, i PG[.]) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 PG[1, 3, 2] 1 2 3 4 5 6 13 14 15 16 17 18 7 8 9 10 11 12 PG[2, 1, 3] 7 8 9 10 11 12 1 2 3 4 5 6 13 14 15 16 17 18 PG[3, 1, 2] 13 14 15 16 17 18 1 2 3 4 5 6 7 8 9 10 11 12 PG[3, 2, 1] 13 14 15 16 17 18 7 8 9 10 11 12 1 2 3 4 5 6 PG[2, 3, 1] 7 8 9 10 11 12 13 14 15 16 17 18 1 2 3 4 5 6
2.4 Combination of Intra-Subset Remapping and Inter-Subset Switching
In a sixth embodiment according to the principles of the present invention, we propose to combine the intra-subset remapping and inter-subset switching described in previous embodiments. If a resource in the first slot is denoted by CB.sub.1[i], then after remapping, the resource is denoted by CB.sub.2[g(w(i,PG[s.sub.1, s.sub.2, . . . , s.sub.K]),n)] (or concisely, CB.sub.2[g(w(i,PG[ ]),n)]) in the second slot. Note we use the composite function g(w(i, PG[ ]),n) to indicate the combined operation of inter-subset switching and intra-subset permutation. Here PG[s.sub.1, s.sub.2, . . . , s.sub.K] is the inter-subset switching pattern, and n=[n.sub.1, . . . , n.sub.K] is the intra-subset remapping parameter vector. This applies to both cases where the intra-subset permutation g( ,n) function is GF based, or PBRO based, as defined in Section 2.3.
In a first sub-embodiment of the sixth embodiment according to the principles of the present invention, the inter-subset switching pattern PG[s.sub.1, s.sub.2, . . . , s.sub.K] and/or parameter vector n=[n.sub.1, . . . , n.sub.K] are the same for all cells. The parameter PG[s.sub.1, s.sub.2, . . . , s.sub.K] and n=[n.sub.1, . . . , n.sub.K] can be communicated to the UE by means of higher-layer signaling.
In a second sub-embodiment of the sixth embodiment according to the principles of the present invention, the inter-subset switching pattern PG[s.sub.1, s.sub.2, . . . , s.sub.K] and/or parameter vector n=[n.sub.1, . . . , n.sub.K] are functions of CELL ID, denoted by PG[s.sub.1, s.sub.2, . . . , s.sub.K]=e(c_id) and n=f (c_id). Therefore, for a different c_id, we can have a different inter-subset switching pattern PG[s.sub.1, s.sub.2, . . . , s.sub.K] and/or parameter vector n=[n.sub.1, . . . , n.sub.K].
We show in the Table 11 below how the intra-subset permutation can be combined with the inter-subset switching, using the same 18 resource example in Table 2. In this example, we have used GF based intra-subset permutation function g(i,n)=g.sub.k(i.sub.k,c,n.sub.k)=i.sub.k,d for the k,c such that i=i.sub.k,c; and (18) d=P.sub.G,3(c,n.sub.k,N.sub.k)=mod(c.times.n.sub.k,N.sub.k+1). (19) Note N.sub.1=N.sub.2=N.sub.3=6 in this example where 18 resource combos are divided into 3 subsets.
TABLE-US-00013 TABLE 11 Example of resource remapping with both intra-subset permutation and inter-subset switching. Resource index in second slot, Resource index in the first slot, i g(w(i, PG[.]), n) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 PG[1, 3, 2], 1 2 3 4 5 6 15 18 14 17 13 16 8 10 12 7 9 11 n = [1, 2, 3] PG[1, 3, 2], 8 10 12 7 9 11 2 4 6 1 3 5 14 16 18 13 15 17 n = [2, 2, 2]
2.5 Combining the OC/CS Resource Remapping Schemes with Cell-Specific CS Hopping
In a seventh embodiment according to the principles of the present invention, we propose to combine the slot-level OC/CS combo resource-permutation methods described in the above Sections 2.1-2.4 with a cell-specific symbol-level CS resource hopping pattern, denoted by h_sym(c_id,s_id,l_id), where the CELL ID is denoted by c_id, the subframe ID is denoted by s_id, and the OFDM symbol (Long block) ID within a subframe is denoted by l_id. The additional cell-specific hopping step is carried out by cyclically shift the CS resource on a particular OFDM by the amount specified by h_sym(c_id,s_id,l_id).
In an eighth embodiment according to the principles of the present invention, we propose to combine the symbol-level CS resource-permutation methods described in the above embodiments in Sections 2.1-2.4 with a cell-specific slot-level CS resource hopping pattern, denoted by h_slot(c_id,sl_id), where the CELL ID is denoted by c_id, the slot ID is denoted by sl_id. The additional cell-specific hopping step is carried out by cyclically shift the CS resource on a particular OFDM by the amount specified by h_slot(c_id,sl_id).
We further describe in detail how to combine the OC/CS resource combo permutation and cell-specific hopping proposed in the seventh and eighth embodiments. Let the possible values of CS in all OC/CS combos in the discussion be K, and K is also the maximum hop value. Let CB.sub.1[i]=OC.sub.1[u.sub.i], CS.sub.1[v.sub.i] be the resource combo in the first slot, and let CB.sub.1[i]=OC.sub.1[u.sub.i],CS.sub.1[v.sub.i] be associated/remapped with CB.sub.2[j]=OC.sub.2[u.sub.j],CS.sub.2[v.sub.i] in the second slot, according to any of the permutation methods described in Sections 2.1-2.4. Then if symbol-level cell-specific hopping in the seventh embodiment is used, the CS index i in the first slot of a subframe will hop to cyclic_shift(v.sub.i,h_sym(c_id,s_id,l_id),K) for an OFDM symbol having an index of l_id; and the CS index j in the second slot of a subframe will hop to cyclic_shift(v.sub.j,h_sym(c_id,s_id,l_id),K). Similarly, if slot-level cell-specific hopping is used, the CS index i in the first slot of a subframe will hop to cyclic_shift(v.sub.i,h_slot(c_id,sl_id),K) for an OFDM symbol having an index of l_id; and the CS index j in the second slot of the subframe will hop to cyclic_shift(v.sub.j,h_slot(c_id,sl_id),K).
Note that the cyclic shift operation is defined as: cyclic_shift(a,b,N)=mod(a+b-1,N)+1, (20) if the N resources are indexed as 1, 2, . . . , N (this is the case throughout this document). On the other hand, if the N resources are indexed as 0, 1, 2, . . . , N-1, then the cyclic shift operation is defined as: cyclic_shift(a,b,N), mod(a+b,N). (21)
3. Symbol-Level and Slot-Level Resource Remapping for Cyclic Shift Resources
The CS resource assignment/remapping is applicable to the following cases: 1. An uplink control RB that contains only Channel Quality Indicator (CQI) channels; 2. An uplink control RB that contains both CQI and ACK/NACK channels; and 3. An uplink control RB that contains only ACK/NACK channels. Note that uplink service grant request channel may reuse the structure of uplink ACK/NACK channel.
3.1. Symbol-Level CS Remapping
In a ninth embodiment according to the principles of the present invention, we propose to associate the CS resources in such a way that if some channel of a UE (for example, CQI, ACK/NACK) is allocated the CS resource CS.sub.1[m] in the first OFDM symbol (l_id=1), then it must be assigned CS.sub.l.sub._.sub.id[t(m,l_id,n)] in the OFDM symbols where l_id>1, where t(m,l_id,n) is a pseudo-random resource remapping/permutation function that is a function of the input resource index m, the OFDM symbol index l_id, and parameter n that is an integer. Note that m=1, 2, . . . , M and M is the total number of CS resources in each OFDM symbol.
We further note that when applied to UL A/N channel (or serving grant), the symbol-level CS remapping can be combined with slot-level OC-remapping or OC hopping. Slot-level OC remapping is very similar to the slot-level OC/CS combo resource remapping that was discussed throughout the draft, except that the resource being remapping from one slot to the next is only the OC resource, not OC/CS combo resource. OC hopping has the same meaning as OC hopping in this context.
We note that by definition, t(m,l_id,n)=m for l_id=1, for the first OFDM symbol under consideration.
In a first sub-embodiment of the ninth embodiment according to the principles of the present invention, the pseudo-random permutation function is established by: t(m,l_id,n)=P.sub.G(m,r(l_id,n,M),M), for l_id>1 (22) where r(l_id,n,M)=mod(l_id+n-1,M)+1. The Galois field based remapping/permutation function P.sub.G(m,r,M) is defined in the previous section.
In a second sub-embodiment of the ninth embodiment according to the principles of the present invention, the pseudo-random permutation function uses the PBRO function in such a way: t(m,l_id,n)=PBRO(mod(m+l_id+n-1,M)+1,M), for l_id>1 (23) The function PBRO(a,b) is defined in the introduction.
In a third sub-embodiment of the ninth embodiment according to the principles of the present invention, the parameter n in the above two sub-embodiments is the same for all cells. The parameter n can be communicated to the UE by means of higher-layer signaling.
In a fourth sub-embodiment of the ninth embodiment according to the principles of the present invention, the parameter n is a function of CELL ID, denoted by n=f(c_id). Therefore, for a different c_id, we will have a different parameter n. One example of such a function is n=mod(c_id-1,N)+1.
For example, if there are six CS resources in each uplink OFDM symbol, or M=6, and there are L=8 uplink OFDM symbols being considered here. Then one example to let n=0, and let t(m, l_id,n)=P.sub.G,3(m,r(l_id,0,6),6). Note here we are able to use the P.sub.G,3( , , ) function defined earlier, since M+1=7 and GF(7) is a ground Galois field. The resource remapping/association as a function of OFDM symbol index, l_id, is shown in Table 12 below. Here the parameter n is chosen as 0.
TABLE-US-00014 TABLE 12 Example of CS resource remapping as a function of OFDM symbol id. M = 6, L = 8. Remapped CS resource index t(m, l_id, 0) L_id = 1 l_id = 2 l_id = 3 l_id = 4 l_id = 5 l_id = 6 l_id = 7 l_id = 8 M = 1 1 2 3 4 5 6 1 2 2 2 4 6 1 3 5 2 4 3 3 6 2 5 1 4 3 6 4 4 1 5 2 6 3 4 1 5 5 3 1 6 4 2 5 3 6 6 5 4 3 2 1 6 5
3.2 Slot-Level CS Remapping
In a tenth embodiment according to the principles of the present invention, we propose to associate the CS resources in such a way that if some channel of a UE (for example, CQI, ACK/NACK) is allocated the CS resource CS, [m] in the first slot, then the channel must be assigned CS.sub.2[g(m,n)] in the second slot, where g(m,n) is a pseudo-random resource remapping/permutation function that is a function of the input resource index m, and a parameter n that is an integer.
We further note that when applied to UL A/N channel (or serving grant), the slot-level CS remapping can be combined with slot-level OC-remapping or OC hopping.
In a first sub-embodiment of the tenth embodiment according to the principles of the present invention, the pseudo-random permutation function is established by: g(m,n)=P.sub.G(m,n,M), (24) where n is chosen from the set [1, . . . , M], or n=1, . . . , M. The function P.sub.G(m,n,M) is defined in the previous section.
In a second sub-embodiment of the tenth embodiment according to the principles of the present invention, the pseudo-random permutation function uses the PBRO function in such a way: g(m,n)=PBRO(mod(m+n-1,M)+1,M). (25) The function PBRO(a,b) is defined in the introduction.
In a third sub-embodiment of the tenth embodiment according to the principles of the present invention, the parameter n in the above two sub-embodiments is the same for all cells. The parameter n can be communicated to the UE by means of higher-layer signaling.
In a fourth sub-embodiment of the tenth embodiment according to the principles of the present invention, the parameter n is a function of CELL ID, denoted by n=f(c_id). Therefore, for a different c_id, we will have a different parameter n. One example of such a function is n=mod(c_id-1,M)+1.
We consider here below an example of M=6, for n=1, 2, 3, 4.
TABLE-US-00015 TABLE 13 Example of slot-level CS remapping with M = 6. m 1 2 3 4 5 6 G(m, n), n = 1 1 2 3 4 5 6 G(m, n), n = 2 2 4 6 1 3 5 G(m, n), n = 3 3 6 2 5 1 4 G(m, n), n = 4 4 1 5 2 6 3 G(m, n), n = 5 5 3 1 6 4 2 G(m, n), n = 6 6 5 4 3 2 1
The application of the slot-level CS remapping to a dedicated CQI or dedicated A/N uplink RB is straightforward, and therefore we do not provide additional explanation. On the other hand, the application of slot-level CS remapping to a mixed CQI and A/N uplink RB is less obvious, and we provide an example below to show how it works.
Here we show an example of how to apply the slot-level CS remapping in the case of mixed ACK/NACK and CQI channels within one RB (12 subcarriers). Here the total number of CSs used by ACK/NACK and CQI is 8 (M=8), and there are a total of 8 ACK/NACK channels sharing 5 CSs, and three CQI channels sharing 3 CSs. The CS remapping function used in this example is g(m,n) with n=2. Note since M+1=9 and GF(9)=GF(3.sup.2) is a Galois field but not a ground Galois field. The non-zero elements of GF(9) is given in the Table 14 below.
TABLE-US-00016 TABLE 14 Elements of GF(9) exponent format .alpha..sup.0 .alpha..sup.1 .alpha..sup.2 .alpha..sup.3 .alpha..sup- .4 .alpha..sup.5 .alpha..sup.6 .alpha..sup.7 vector format [1, 0] [0, 1] [1, 1] [1, 2] [2, 0] [0, 2] [2, 2] [2, 1] (ternary)[LSB, MSB] natural number 1 3 4 7 2 6 8 5 format
The mapping table of g(m,n) for n=2 is given below for M=8 with GF(9), and g(m,n)=P.sub.G,1(m,n,M)=P.sub.G,1(m,2,8), where P.sub.G,1(m,n,M) is defined in Section 1.
TABLE-US-00017 TABLE 15-a CS remapping with g(m, 2), M = 8. m 1 2 3 4 5 6 7 8 g(m, n), n = 2 3 6 4 7 1 8 2 5
Alternatively, we can use the pruned ground GF field based method g(m,n)=P.sub.G,4b(m,n,M) P.sub.G,4b(m,2,8) to generate the following table.
TABLE-US-00018 TABLE 15-b Slot-level remapping with g(i, n), N = 8, n = 2. M 1 2 3 4 5 6 7 8 g(m, n), n = 2 2 4 6 8 1 3 5 7
We proceed to show how the CS resource re-mapping works in table below. Note that there are M=8 CSs, and remapping only takes place within this set of "used" CSs. We applied the CS remapping rules in Table 15-a above to reach this table below. Notice how a single A/N channel or CQI channel can be remapped to different regions in the OC/CS table.
TABLE-US-00019 TABLE 16 CS remapping in mixed CQI and ACK/NACK channel uplink RB. OC/CS Combos OC/CS Combos in slot #1 - in slot #1 - CB.sub.1[ ](ACK/NCK) CB.sub.2[ ](ACK/NCK) Cyclic shift CS in slot #1 - CS in slot #1 - value - CS.sub.1,CQI[ ] (CQI) CS.sub.2[ ] (CQI) [used CS] OC.sub.1[1] OC.sub.1[2] OC.sub.1[3] OC.sub.2[1] OC.sub.2[2] OC.s- ub.2[3] 0 = [1] A/N #1 A/N #6 A/N#3 A/N #8 1 [2] A/N #4 CQI #2 2 [3] A/N #2 A/N #7 A/N #1 A/N #6 3 [4] A/N #5 A/N #2 A/N #7 4 [5] A/N #3 A/N #8 CQI #3 5- 6 [6] CQI #1 A/N #4 7- 8-[7] CQI #2 A/N #5 9- 10-[8] CQI #3 CQI #1 11-
3.3 Alternative Method for Resource Remapping in the Mixed CQI and ACK/NACK Case
In Table 16, it can be seen that four A/N channels, A/N #1, 2, 6, 7 are assigned to neighboring CSs, after the joint CS remapping on CQI and A/N channels. This may degrade A/N performance. In this subsection, we propose an alternative approach for resource remapping in the mixed CQI and ACK/NACK case.
In an eleventh embodiment according to the principles of the present invention, we propose to divide the total CS resources within one RB into two parts, one part allocated to CQI channel and the other part allocated to the ACK/NACK (or Serving request) channel. The allocation is fixed in two slots of a subframe. In addition, within the part of CSs assigned to the CQI channel, both the symbol-level CS remapping proposed in Section 3.1 and slot-level CS remapping proposed in Section 3.2 can be applied. On the other hand, within the CS resources allocated to the uplink A/N channels (or serving request), we can apply any of the following (a) the joint slot-level joint OC/CS remapping described in Section 2.1-2.4; (b) the symbol-level CS remapping described in Section 3.1; (c) the slot-level CS remapping described in Section 3.2.
We reuse the eight A/N channel and three CQI channel example used in Table 16 to illustrate this alternative approach. Furthermore, in this example, we use the slot-level global OC/CS remapping (Section 2.1) for the A/N part, and use slot-level CS remapping for the CQI part. It is clear from Table 17 that CS resources assigned to the A/N part and the CQI part remain the same in slot #1 and slot #2.
TABLE-US-00020 TABLE 17 Illustration of alternative method of resource remapping in the uplink RB with mixed CQI and ACK/NACK channel. OC/CS Combos OC/CS Combos in slot #1 - in slot #1 - CB.sub.1[ ](ACK/NCK) CB.sub.2[ ](ACK/NCK) Cyclic shift CS in slot #1 - CS in slot #1 - value - CS.sub.1,CQI[ ] (CQI) CS.sub.2[ ] (CQI) [used CS] OC.sub.1[1] OC.sub.1[2] OC.sub.1[3] OC.sub.2[1] OC.sub.2[2] OC.s- ub.2[3] 0 = [1] CB.sub.1[1] CB.sub.1[6] CB.sub.2[1] CB.sub.2[6] 1 [2] CB.sub.1[4] CB.sub.2[4] 2 [3] CB.sub.1[2] CB.sub.1[7] CB.sub.2[2] CB.sub.2[7] 3 [4] CB.sub.1[5] CB.sub.2[5] 4 [5] CB.sub.1[3] CB.sub.1[8] CB.sub.2[3] CB.sub.2[8] 5- 6 [6] CS.sub.1,CQI[1] CS.sub.2,CQI[1] 7- 8-[7] CS.sub.1,CQI[2] CS.sub.2,CQI[2] 9- 10-[8] CS.sub.1,CQI[3] CS.sub.2,CQI[3] 11-
In addition, for the A/N (or serving grant) channels, if an A/N channel is assigned the resource combo CB.sub.1[i] in the first slot, then the A/N channel must be assigned CB.sub.2[g(i,n)] in the second slot. Let n=2. One example of g(i,n) is to let g(i,n)=P.sub.G,1(i,2,8) (note N=8 in this example indicating a total of 8 OC/CS combinations for A/N channel, and GF(9) exists). The mapping table is the same as in Table 15-a or 15-b, if we replace m with i, and M with N.
For the CQI channels, on the other hand, if a CQI channel is assigned the CS resource CS.sub.1[m] in the first slot, then CQI channel must be assigned CS.sub.2[g(m,n)] in the second slot. Similarly, let n=2. One example of g(m,n) is to let g(m,n)=P.sub.G,1(m,2,3) (note M=3 in this example indicating a total of 3 CS resources for A/N channel, and CF(4) exists). The mapping table is omitted here for brevity.
3.4 Combining CS Resource Mapping and Cell-Specific Hopping
In a twelfth embodiment according to the principles of the present invention, we propose to combine the symbol-level CS resource-permutation methods described in the above embodiment with a cell-specific symbol-level CS resource hopping pattern, denoted by h_sym(c_id,s_id,l_id), where the CELL ID denoted by c_id, the subframe ID denoted by s_id, and the OFDM symbol (Long block) ID within a subframe denoted by l_id. The additional cell-specific hopping step is carried out by cyclically shift the CS resource on a particular OFDM by the amount specified by h_sym(c_id,s_id,l_id).
In a thirteenth embodiment according to the principles of the present invention, we propose to combine the symbol-level CS resource-permutation methods described in the above embodiment with a cell-specific slot-level CS resource hopping pattern, denoted by h_slot(c_id,sl_id), where the CELL ID denoted by c_id, the slot ID denoted by sl_id. The additional cell-specific hopping step is carried out by cyclically shifting the CS resource on a particular OFDM by the amount specified by h_slot(c_id,sl_id).
We further describe in detail how to combine symbol-level CS resource permutation and cell-specific hopping proposed in the above two embodiments. Let the number of CS resources in the discussion be K, and K is also the maximum hop value. Let CS.sub.l.sub._.sub.id[t(m,l_id,n)] denote the CS resource for the OFDM symbol l_id, according to the symbol-level remapping algorithms discussed earlier. Then if symbol-level cell-specific hopping is used, the CS index will hop to cyclic_shift(t(m,l_id,n),h_sym(c_id,s_id,l_id),K) for OFDM symbol l_id. Similarly, if slot-level cell-specific hopping is used, the CS index in the first slot will hop to cyclic_shift(t(m,l_id,n),h_slot(c_id,sl_id),K) for OFDM symbol index by l_id, in the slot indexed by sl_id.
The description of combination of slot-level CS resource remapping and slot or symbol-level cell-specific hopping is similar, and is omitted for brevity.
4. Generation of the Slot-Level or Symbol-Level Cell-Specific CS Hopping Pattern
Let the maximum number of the hop value be denoted by K.
In a fourteenth embodiment according to the principles of the present invention, we propose a slot-level base sequence cell-specific pattern with a period of K consecutive slots. We propose a cell-specific slot-level hopping pattern such that: h_slot(c_id,sl_id)=P.sub.G(sl_id,r(c_id,n,K),K), (26) or, h_slot(c_id,sl_id)=PBRO(mod(sl_id+c_id+n-1,K)+1,K), (27) where the function r is defined as r(c_id,n,K)=mod(c_id+n-1,K)+1. Note sl_id=1, . . . , K is the slot index of the slot within the K consecutive slots, n is a parameter that is an integer, and c_id denotes the CELL ID. The Galois field based remapping/permutation function P.sub.G(c_id,r,K) is defined in Section 1. The PBRO function is previously defined.
For example, if there are twelve subcarriers in the LTE uplink control channel PUCCH, and thus the maximum hop K=12. Then one example to let n=0, and let h_slot(c_id,sl_id)=P.sub.G,3(sl_id,r(c_id,0,12),12)=mod(sl_id.times.r(c_i- d,0,12),13). Note here we are able to use the P.sub.G,3( , , ) function defined earlier, since 12+1=13 and GF(13) is a ground Galois field.
We again let the maximum number of the hop value be denoted by K. Furthermore, we let the L be the number of OFDM symbols of interest within a subframe.
In a fifteenth embodiment according to the principles of the present invention, we propose a symbol-level base sequence cell-specific pattern that repeats every subframe, i.e., it is not a function of subframe ID. Denoting, s_id as subframe ID, we propose a cell-specific slot-level hopping pattern such that h_sym(c_id,s_id,l_id)=P.sub.G(x(l_id,K),r(c_id,n,K),K), (28) or h_sym(c_id,s_id,l_id)=PBRO(mod(l_id+c_id+n-1,K)+1,K), (29) where the function x and r is defined as x(l_id,K)=mod(l_id-1,K)+1 and r(c_id,n,K)=mod(c_id+n-1,K)+1. Note l_id=1, . . . , L denotes the OFDM symbol (long block) ID, n is a parameter that is an integer, s_id denotes the subframe ID, and c_id denotes the CELL ID. The Galois field based remapping/permutation function P.sub.G(x,r,K) is defined in Section 1. The PBRO function is defined in the introduction.
For example, if there are 12 subcarriers in the LTE uplink control channel PUCCH, and thus the maximum hop K=12. Then one example to let n=0, and let h_sym(c_id,s_id,l_id)=P.sub.G,3(x(l_id,12),r(c_id,0,12),12)=mod(x(l_id,12- ).times.r(c_id,0,12),13). Note here we are able to use the P.sub.G,3( , , ) function, defined earlier, since 12+1=13 and GF(13) is a ground Galois field.
5. Generation of the Subframe-Level or Slot-Level Base Sequence Hopping Pattern
In a sixteenth embodiment according to the principles of the present invention, let there be a total of Z base sequences for uplink communications. Then we propose a subframe-level base sequence hopping pattern with a period of Z consecutive subframes. In addition, for a given cell, let BS.sub.1[z]=z be the base sequence index in the first subframe within one period of Z consecutive subframes, then the base sequence index used in subsequent subframes in the same cell is denoted by BS.sub.s.sub._.sub.id[s(z,s_id,n)]. Here z=1, . . . , Z, s_id=1, . . . , Z, and n is a parameter that is an integer. Note s_id denotes the subframe ID within a period of Z subframes.
In a sub-embodiment of the sixteenth embodiment according to the principles of the present invention, the pseudo-random permutation function s(z,s_id,n) is given by: s(z,s_id,n)=P.sub.G(z,r(s_id,n,Z),Z) (30) or, s(z,s_id,n)=PBRO(mod(z+s_id+n-1,Z)+1,Z), (31) where the function r is defined as r(s_id,n,Z)=mod(s_id+n-1,Z)+1. The Galois field based remapping/permutation function P.sub.G(z,r,Z) is defined in the previous section. The PBRO(.,.) function is defined in the introduction.
For example, if there are thirty base sequences being used in a cellular system, or Z=30. Then one example to let n=0, and let s (z, s_id,n)=P.sub.G,3(z,r(s_id,0,30),30)=mod(z x s_id,31). Note here we are able to use the P.sub.G function defined earlier, since Z+1=31 and GF(31) is a ground Galois field.
There can be several slots within one subframe in the uplink transmission. For example, in the 3GPP LTE standard, there are 2 slots within each subframe in the uplink.
In a seventeenth embodiment according to the principles of the present invention, let there be a total of Z base sequences for uplink communications. Then we propose a slot-level base sequence hopping pattern with a period of Z consecutive slots. In addition, for a given cell, let BS, [z]=z be the base sequence index in the first slot within one period of Z consecutive slots, then the base sequence index used in subsequent slots in the same cell is denoted by BS.sub.s.sub._.sub.id [s(z, sl_id,n)]. Here z=1, . . . , Z, sl_id=1, . . . , Z, and n is a parameter that is an integer. Note sl_id denotes slot ID within a period of Z slots.
In one sub-embodiment of the seventeenth embodiment according to the principles of the present invention, the pseudo-random permutation function s(z,sl_id,n) is given by s(z,sl_id,n)=P.sub.G(z,r(sl_id,n,Z),Z), (32) or s(z,sl_id,n)=PBRO(mod(z+sl_id+n-1,Z)+1,Z), (33) where the function r is defined as r(sl_id,n,Z)=mod(sl_id+n-1,Z)+1. The Galois field based remapping/permutation function P.sub.G(z,r,Z) is defined in the previous section.
For example, if there are thirty base sequences being used in a cellular system, or Z=30. Then one example to let n=0, and let s(z, sl_id,n)=P.sub.G,3(z,r(sl_id,0,30),30)=mod(z x sl_id,31). Note here we are able to use the P.sub.G,3 function defined earlier, since Z+1=31 and GF(31) is a ground Galois field. The PBRO(.,.) function is defined in the introduction.
Annex: Alternative OC/CS Resource Allocation for N=18 Resources (Excerpt from [6])
TABLE-US-00021 TABLE 18 Alternative OC/CS allocation scheme for N = 18. Cyclic Shift Walsh Sequence Index Index 0 1 2 3 0 0 15 1 16 4 2 8 3 1 12 4 17 5 5 9 6 2 13 7 6 8 10 9 3 14 10 7 11 11
While the forgoing explanation of the principles of the present invention have been shown and described in detail in connection with the preferred embodiments, it will be apparent to those skilled in the art that modifications and variations can be made without departing from the spirit and scope of the invention as defined by the appended claims.
* * * * *
D00000

D00001

D00002

D00003

M00001

M00002

M00003

P00001

P00002

XML
uspto.report is an independent third-party trademark research tool that is not affiliated, endorsed, or sponsored by the United States Patent and Trademark Office (USPTO) or any other governmental organization. The information provided by uspto.report is based on publicly available data at the time of writing and is intended for informational purposes only.
While we strive to provide accurate and up-to-date information, we do not guarantee the accuracy, completeness, reliability, or suitability of the information displayed on this site. The use of this site is at your own risk. Any reliance you place on such information is therefore strictly at your own risk.
All official trademark data, including owner information, should be verified by visiting the official USPTO website at www.uspto.gov. This site is not intended to replace professional legal advice and should not be used as a substitute for consulting with a legal professional who is knowledgeable about trademark law.