Resource allocation method and full duplex communication system
Lai , et al. January 5, 2
U.S. patent number 10,887,929 [Application Number 16/529,809] was granted by the patent office on 2021-01-05 for resource allocation method and full duplex communication system. This patent grant is currently assigned to Realtek Semiconductor Corp.. The grantee listed for this patent is Realtek Semiconductor Corp.. Invention is credited to Ting-Wei Lai, Der-Zheng Liu, Hsuan-Jung Su.






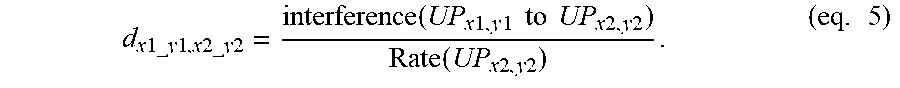
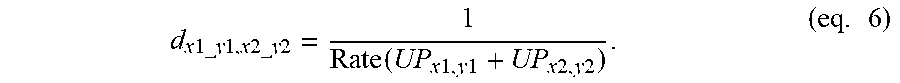
View All Diagrams
| United States Patent | 10,887,929 |
| Lai , et al. | January 5, 2021 |
Resource allocation method and full duplex communication system
Abstract
The present disclosure provides a resource allocation method. The resource allocation method includes the following steps: selecting multiple first selected virtual nodes according to multiple virtual pheromonal trails on multiple virtual edges, in which the first selected virtual nodes forms at least one virtual tour, and the virtual tour includes multiple first virtual edges; updating the virtual pheromonal trails on the virtual edges according to virtual distances corresponding to the first virtual edges of the virtual tour; selecting multiple second selected virtual nodes according to the updated virtual pheromonal trails on the virtual edges, in which the second selected virtual nodes form at least one resulting virtual tour; allocating the resource blocks to selected user pairs according to the resulting virtual tour.
| Inventors: | Lai; Ting-Wei (Taipei, TW), Su; Hsuan-Jung (Taipei, TW), Liu; Der-Zheng (Hsinchu County, TW) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Applicant: |
|
||||||||||
| Assignee: | Realtek Semiconductor Corp.
(HsinChu, TW) |
||||||||||
| Family ID: | 1000005285999 | ||||||||||
| Appl. No.: | 16/529,809 | ||||||||||
| Filed: | August 2, 2019 |
Prior Publication Data
| Document Identifier | Publication Date | |
|---|---|---|
| US 20200119900 A1 | Apr 16, 2020 | |
Related U.S. Patent Documents
| Application Number | Filing Date | Patent Number | Issue Date | ||
|---|---|---|---|---|---|
| 62744664 | Oct 12, 2018 | ||||
| Current U.S. Class: | 1/1 |
| Current CPC Class: | H04L 5/143 (20130101); H04W 76/10 (20180201); H04L 67/38 (20130101); H04L 5/14 (20130101); H04W 72/082 (20130101); H04L 5/1438 (20130101) |
| Current International Class: | H04L 5/14 (20060101); H04W 76/10 (20180101); H04L 29/06 (20060101); H04W 72/08 (20090101) |
References Cited [Referenced By]
U.S. Patent Documents
| 8547884 | October 2013 | Lo |
| 9363066 | June 2016 | Lo |
| 9420606 | August 2016 | Bhushan |
| 9698963 | July 2017 | Luo |
| 9839037 | December 2017 | Lo |
| 10212723 | February 2019 | Jiang |
| 10298297 | May 2019 | Cui |
| 10368357 | July 2019 | Lopez-Perez |
| 10567147 | February 2020 | DiFazio |
| 2018/0213547 | July 2018 | Ju |
| 2019/0123855 | April 2019 | Stirling-Gallacher |
Other References
|
Liu et al. The Sub-channel Allocation Algorithm in Femtocell Networks Based on Ant Colony Optimization; MILCOM 2012--2012 IEEE Military Communications Conference Year: 2012. cited by examiner . Sim et al., Ant Colony Optimization for Routing and Load-Balancing: Survey and New Directions; IEEE Transactions on Systems, Man, and Cybernetics--Part A: Systems and Humans, vol. 33, No. 5, Sep. 2003. cited by examiner. |
Primary Examiner: Harper; Kevin C.
Assistant Examiner: Baron; Henry
Attorney, Agent or Firm: Hsu; Winston
Parent Case Text
CROSS REFERENCE TO RELATED APPLICATIONS
This application claims the benefit of U.S. provisional application No. 62/744,664, filed on Oct. 12, 2018, which is incorporated herein by reference.
Claims
What is claimed is:
1. A resource allocation method, applied in a full duplex communication system comprising a plurality of stations and a plurality of user devices, wherein the full duplex communication system operates on a plurality of resource blocks, and the resource allocation method comprises the following steps: selecting a plurality of first selected virtual nodes according to a plurality of virtual pheromonal trails on a plurality of virtual edges, wherein the plurality of first selected virtual nodes form at least one virtual tour, and the virtual tour comprises a plurality of first virtual edges; updating the plurality of virtual pheromonal trails on the virtual edges according to virtual distances corresponding to the first virtual edges of the virtual tour; selecting a plurality of second selected virtual nodes according to the updated virtual pheromonal trails on the virtual edges, wherein the plurality of second selected virtual nodes forms at least one resulting virtual tour; allocating the plurality of resource blocks to a plurality of selected user pairs according to the resulting virtual tour, wherein the plurality of selected user pairs correspond to the resulting virtual tour; wherein the plurality of user devices and the plurality of stations forms a plurality of user pairs, and each user pair comprises a downlink user device and a uplink user device, among the plurality of user pairs, along with a station among the plurality of stations; wherein the plurality of user pairs represents a plurality of virtual nodes, and the plurality of first selected virtual nodes is among the plurality of virtual nodes; wherein a virtual edge, among the plurality of virtual edges, is formed between two virtual nodes among the plurality of virtual nodes; wherein the virtual distances are related to data rates.
2. The resource allocation method of claim 1, wherein the step of updating the plurality of virtual pheromonal trails on the virtual edges comprises: calculating the virtual distances corresponding to the first virtual edges of the virtual tour; determining incremental virtual pheromones corresponding to the first virtual edges of the virtual tour according to the virtual distances corresponding to the first virtual edges of the virtual tour; and updating the plurality of virtual pheromonal trails on the virtual edges according to the incremental virtual pheromones.
3. The resource allocation method of claim 1, wherein a first virtual distance corresponding to a first virtual edge is inversely proportional to data rates of first virtual nodes between which the first virtual edge is formed.
4. The resource allocation method of claim 1, wherein a first virtual distance corresponding to a first virtual edge is inversely proportional to a data rate of one of first virtual nodes, in which the first virtual edge is formed between the first virtual nodes.
5. The resource allocation method of claim 1, wherein the step of selecting the first selected virtual nodes further comprises: forming a first feasible set comprising all or a part of the plurality of virtual nodes; selecting a third selected virtual node from the first feasible set, wherein the third selected virtual node is within a first cell; forming a second feasible set by removing a plurality of first virtual nodes within the first cell from the first feasible set, wherein the second feasible set comprises a plurality of second virtual nodes; and selecting a fourth selected virtual node from the second feasible set.
6. The resource allocation method of claim 5, wherein the step of selecting the third selected virtual node comprising: selecting the third selected virtual node according to a plurality of initial probabilities corresponding to the plurality of virtual nodes.
7. The resource allocation method of claim 6, wherein distribution of the initial probabilities is uniform distribution.
8. The resource allocation method of claim 5, further comprising: computing a plurality of transition probabilities corresponding to the plurality of second virtual nodes according to the plurality of virtual pheromonal trails on the plurality of virtual edges, wherein each transition probability is corresponding to a transition from the third selected virtual node to a second virtual node of the plurality of second virtual nodes; and selecting the fourth selected virtual node according to the plurality of transition probabilities.
9. A full duplex (FD) communication system comprising: a plurality of stations and a plurality of user devices, wherein the full duplex communication system operates on a plurality of resource blocks; and a computing device comprising a processing unit and a storage unit, wherein the storage unit is configured to store a program code to be executed by the processing unit to perform the following steps: selecting a plurality of first selected virtual nodes according to a plurality of virtual pheromonal trails on a plurality of virtual edges, wherein the plurality of first selected virtual nodes form at least one virtual tour, and the virtual tour comprises a plurality of first virtual edges; updating the plurality of virtual pheromonal trails on the virtual edges according to virtual distances corresponding to the first virtual edges of the virtual tour; selecting a plurality of second selected virtual nodes according to the updated virtual pheromonal trails on the virtual edges, wherein the plurality of second selected virtual nodes form at least one resulting virtual tour allocating the plurality of resource blocks to a plurality of selected user pairs according to the resulting virtual tour, wherein the plurality of selected user pairs correspond to the resulting virtual tour; wherein the plurality of user devices and the plurality of stations forms a plurality of user pairs, and each user pair comprises a downlink user device and a uplink user device, among the plurality of user pairs, along with a station among the plurality of stations; wherein the plurality of user pairs represents a plurality of virtual nodes, and the plurality of first selected virtual nodes is among the plurality of virtual nodes; wherein a virtual edge, among the plurality of virtual edges, is formed between two virtual nodes among the plurality of virtual nodes; wherein the virtual distances are related to data rates.
10. The FD communication system of claim 9, wherein the step of updating the plurality of virtual pheromonal trails on the virtual edges comprises: calculating the virtual distances corresponding to the first virtual edges of the virtual tour; determining incremental virtual pheromones corresponding to the first virtual edges of the virtual tour according to the virtual distances corresponding to the first virtual edges of the virtual tour; and updating the plurality of virtual pheromonal trails on the virtual edges according to the incremental virtual pheromones.
11. The FD communication system of claim 9, wherein a first virtual distance corresponding to a first virtual edge is inversely proportional to data rates of first virtual nodes between which the first virtual edge is formed.
12. The FD communication system of claim 9, wherein a first virtual distance corresponding to a first virtual edge is inversely proportional to a data rate of one of first virtual nodes, in which the first virtual edge is formed between the first virtual nodes.
13. The FD communication system of claim 9, wherein the program code is executed by the processing unit to further perform the following steps: forming a first feasible set comprising all or a part of the plurality of virtual nodes; selecting a third selected virtual node from the first feasible set, wherein the third selected virtual node is within a first cell; forming a second feasible set by removing a plurality of first virtual nodes within the first cell from the first feasible set, wherein the second feasible set comprises a plurality of second virtual nodes; and selecting a fourth selected virtual node from the second feasible set.
14. The FD communication system of claim 13, wherein the step of selecting the third selected virtual node comprising: selecting the third selected virtual node according to a plurality of initial probabilities corresponding to the plurality of virtual nodes.
15. The FD communication system of claim 14, wherein distribution of the initial probabilities is uniform distribution.
16. The FD communication system of claim 13, wherein the program code is executed by the processing unit to further perform the following steps: computing a plurality of transition probabilities corresponding to the plurality of second virtual nodes according to the plurality of virtual pheromonal trails on the plurality of virtual edges, wherein each transition probability is corresponding to a transition from the third selected virtual node to a second virtual node of the plurality of second virtual nodes; and selecting the fourth selected virtual node according to the plurality of transition probabilities.
Description
BACKGROUND OF THE INVENTION
1. Field of the Invention
The present disclosure relates to a resource allocation method and a full duplex communication system, and more particularly, to a resource allocation method and a full duplex communication system capable of allocating wireless resources in a multi-cell scenario.
2. Description of the Prior Art
As the demand of wireless service increases, the utilized frequency spectrum is getting crowded, which might degrade the quality of service (QoS) of wireless systems. Enhancing data rate is always a goal for the next-generation mobile communication. Full-duplex (FD) communications, allowing simultaneous transmission and reception on the same frequency carrier(s), attracts more attentions recently, which is expected to be a promising way to increase spectrum efficiency.
Previously, strong self-interference makes FD communications difficult to be realized. Thanks to the breakthroughs in hardware development, self-interference is able to be reduced by 110 dB, which makes FD communications possible to be realized and being able to upgrade the capacity to a new level. Therefore, resource allocation for the FD system is critical.
SUMMARY OF THE INVENTION
It is therefore a primary objective of the present disclosure to provide a resource allocation method and a full duplex communication system capable of allocating wireless resources in a multi-cell scenario.
The present disclosure provides a resource allocation method applied in a full duplex communication system. The full duplex communication system includes multiple stations and multiple user devices, and the full duplex communication system operates on multiple resource blocks. The resource allocation method includes the following steps: selecting first selected virtual nodes according to virtual pheromonal trails on virtual edges, in which the first selected virtual nodes forms at least one virtual tour, and the virtual tour includes first virtual edges; updating the virtual pheromonal trails on the virtual edges according to virtual distances corresponding to the first virtual edges of the virtual tour; selecting second selected virtual nodes according to the updated virtual pheromonal trails on the virtual edges, in which the second selected virtual nodes form at least one resulting virtual tour; and allocating the resource blocks to selected user pairs according to the resulting virtual tour, in which selected user pairs correspond to the resulting virtual tour. The user devices and stations form user pairs, and each user pair includes a downlink user device and an uplink user device, among the user pairs, along with a station among the stations. The user pairs represent virtual nodes, and the first selected virtual nodes are among the virtual nodes. A virtual edge, among the virtual edges, is formed between two virtual nodes among the virtual nodes. The virtual distances are related to data rates.
The present disclosure further provides a full duplex (FD) communication system. The full duplex communication system includes stations, user devices, and a computing device. The full duplex communication system operates on multiple resource blocks. The computing device includes a processing unit and a storage unit. The storage unit stores a program code to be executed by the processing unit to implement the following steps: selecting first selected virtual nodes according to virtual pheromonal trails on virtual edges, in which the first selected virtual nodes form at least one virtual tour, and the virtual tour includes first virtual edges; updating the virtual pheromonal trails on the virtual edges according to virtual distances corresponding to the first virtual edges of the virtual tour; selecting second selected virtual nodes according to the updated virtual pheromonal trails on the virtual edges, in which the second selected virtual nodes form at least one resulting virtual tour; allocating the resource blocks to selected user pairs according to the resulting virtual tour, in which the selected user pairs correspond to the resulting virtual tour. The user devices and stations form user pairs, and each user pair includes a downlink user device and an uplink user device, among the plurality of user pairs, along with a station among the stations. The user pairs represent virtual nodes, and the first selected virtual nodes are among the virtual nodes. A virtual edge, among the virtual edges, is formed between two virtual nodes among the virtual nodes. The virtual distances are related to data rates.
These and other objectives of the present invention will no doubt become obvious to those of ordinary skill in the art after reading the following detailed description of the preferred embodiment that is illustrated in the various figures and drawings.
BRIEF DESCRIPTION OF THE DRAWINGS
FIG. 1 is a schematic diagram of a full duplex (FD) communication system according to an embodiment of the present disclosure.
FIG. 2 illustrates schematic diagrams of ants finding food from home.
FIG. 3 illustrates a graphic representation of an FD communication system according to an embodiment of the present disclosure.
FIG. 4 illustrates a virtual path corresponding to a resource block according to an embodiment of the present disclosure.
FIG. 5 illustrates a plurality of virtual paths corresponding to a plurality of resource blocks according to an embodiment of the present disclosure.
FIG. 6 is a schematic diagram of a resource allocation method according to an embodiment of the present disclosure.
DETAILED DESCRIPTION
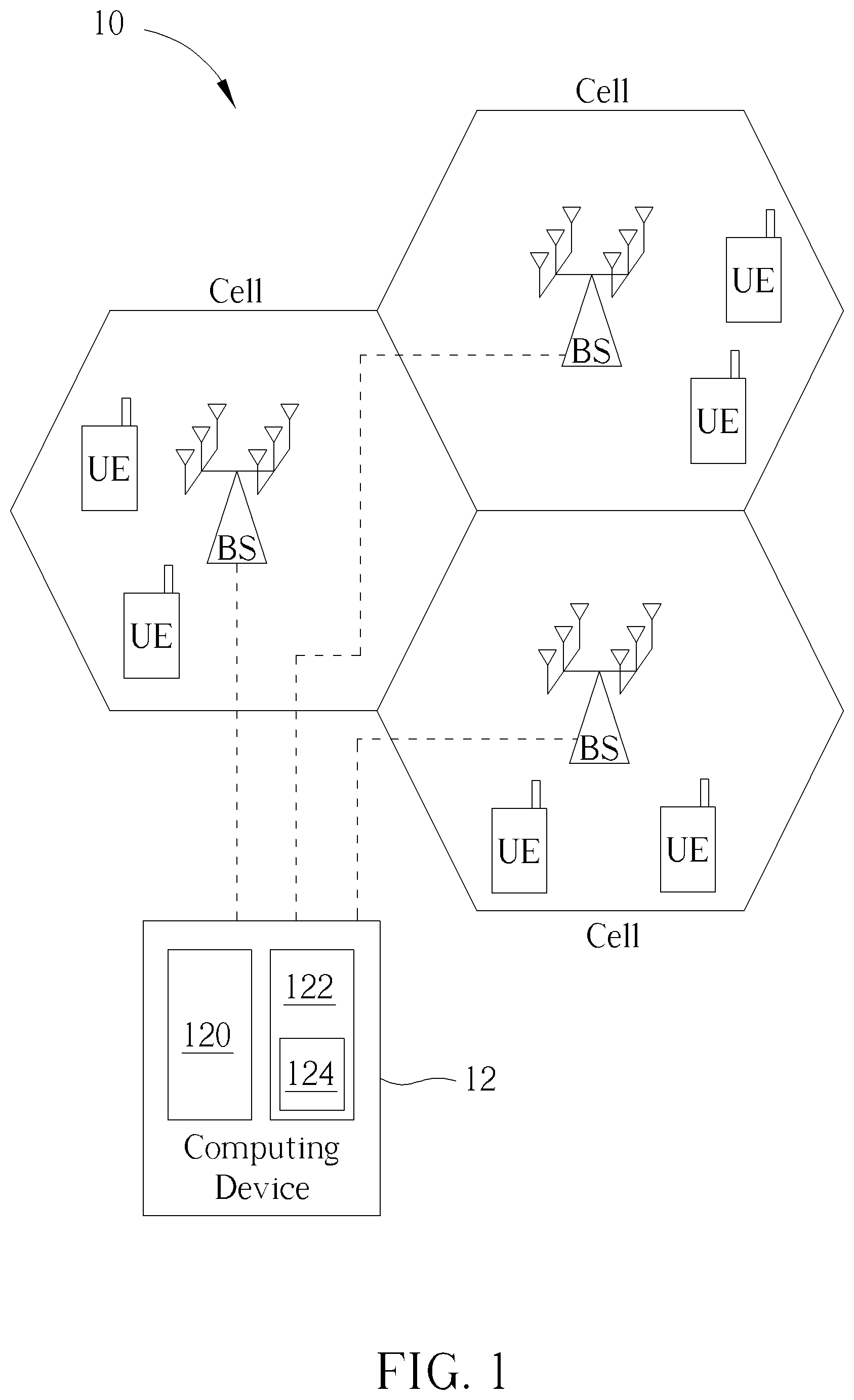
FIG. 1 is a schematic diagram of a full duplex (FD) communication system 10 according to an embodiment of the present disclosure. The FD communication system 10 comprises a plurality of stations BS, a plurality of user devices UE and a computing device 12. The user device UE may be a phone, a tablet computer, a laptop and the like. The station BS may be a macro base station in a cellular network scenario. The station BS may also be a femto base station or an access point (AP) in a WLAN (wireless local area network) scenario. The plurality of stations BS correspond to a plurality of cells respectively. The cell represents a service area covered by the corresponding station BS. The cells in FIG. 1 are illustrated as hexagons for exemplary purpose, but not limited thereto. The computing device 12 may be a computer or a server, comprising a processing unit 120 and a storage unit 122. The processing unit 120 may be one or more processor(s), e.g., CPU (central processing unit). The storage unit 122 may be a non-volatile memory (NVM), e.g., an electrically erasable programmable read only memory (EEPROM) or a flash memory. The computing device 12 is coupled to the plurality of stations BS and configured to execute a resource allocation process to obtain a resource allocation scheme. Based on the resource allocation scheme obtained by the computing device 12, the plurality of stations BS allocates wireless resources to the user devices UE, to enhance an overall data rate. The storage unit 122 is configured to store a program code 124 to be executed such that the processing unit 120 to execute the resource allocation method.
The FD communication system 10 operates on a plurality resource blocks RB (not shown in FIG. 1). The resource block RB represents a certain frequency spectrum within a certain period of time. Practically, in an OFDM (orthogonal frequency division multiplexing) system, the resource block RB may represent couples of frequency subcarriers or one subcarrier.
In the FD communication system 10, a plurality of user pairs UP is formed. For example, a user pair UP.sub.a represents a downlink user device UE.sub.DL,a and a uplink user device UE.sub.UL,a along with a station BS.sub.b within a cell b. When a resource block RB.sub.c is assigned to the user pair UP.sub.a in the cell b, it means that the uplink user device UE.sub.DL,a in the cell b transmits data packets to the station BS.sub.b (via an uplink direction) using the resource block RB.sub.c and the station BS.sub.b transmits data packets to the downlink user device UE.sub.DL,a (via a downlink direction) in the cell b using the resource block RB.sub.c at the same time. In other words, the plurality of user devices UE and the plurality of stations BS form the plurality of user pairs UP, in which the user pairs UP correspond to the stations BS respectively.
The resource allocation problem for the FD communication system basically refers to determination of which resource block being assigned to which user pair, such that an overall capacity can be maximized. In the present disclosure, the terminologies "capacity", "data rate", "transmission rate", "spectrum efficiency", and "throughput" are used interchangeably. In an embodiment, the capacity or the spectrum efficiency may be evaluated in terms of bps/Hz (bits per second per Hz), or bps (bits per second).
In the present disclosure, a concept of an Ant Colony Optimization (ACO) algorithm is adopted to solve the resource allocation problem for the FD communication system. A traditional ACO routing technique models the establishment of routes based on the mechanisms, used by ant colonies, of establishing and maintaining paths to desirable food sources. Ants randomly choose a path to a food source. On the chosen path, the ants deposit a chemical substance called "pheromone", which allows other ants to follow the pheromone scent and hence the chosen path. When more ants traverse a path, the pheromone deposit on that path gets more intense, thereby allowing more ants to become attracted to and use that path to travel to the food source and back. The concentration of the pheromone scent on paths to food sources evaporates after certain amount of time. Thus, longer and less traveled paths lose their pheromone scent faster than shorter and more traveled paths. For this reason, more ants would choose the shorter/shortest paths to food sources.
FIG. 2 illustrates schematic diagrams of ants finding food from home. At the beginning, every ant moves randomly and leaves pheromone on the path through which it passes. Some ants go shorter paths and some go longer, as shown in the subfigure 2a. Next time when the ants leave home, they would sense the pheromone on the path and decide which way to go accordingly, as shown in the subfigure 2b. The higher concentration of pheromone the ants detect, the more probably the ants would follow. On the other hand, the more frequently the path is passed, the more pheromone on that path is retained. Eventually, the ants might find a shortest path, as the subfigure 2c shows.
Specifically, a (, ) graph is used to model the routing of the ants in a conventional ACO algorithm, where represents a set of nodes including N nodes and represents a set of edges including E edges, and the edges are between the nodes. The ACO algorithm operates under three basic assumptions: 1) each ant chooses a node to travel/visit based on a transition probability, which is a function of an edge distance (to the node) and an amount of pheromonal trails left on that edge; 2) each ant would not visit a city twice/again if the tour has not accomplished; 3) the ant lays pheromonal trails on the passed edges after the tour is accomplished. In the present disclosure, the terminologies "pheromonal trail" and "pheromone" are used interchangeably.
Mathematically, during an operation of the conventional ACO algorithm, a transition probability of a k.sup.th ant traveling from an i.sup.th node (or, a node i) to a j.sup.th node (or, a node j) at a time t may be expressed as
.function..tau..function..alpha..function..eta..beta..di-elect cons..times..tau..function..alpha..function..eta..beta..times..times..di-- elect cons..times. ##EQU00001##
In eq. 1, .tau..sub.i,j(t) represents the (virtual) pheromone left on an edge e(i, j) between the node i to the node j at the time t, .eta..sub.i,j=1/d.sub.i,j represents the visibility (preference) of the edge e(i,j), and d.sub.i,j represents the distance of the edge e(i, j). Parameters .alpha. and .beta. are used to reflect the significance of the pheromone and the visibility (preference). The set F.sub.k represents a feasible set including the nodes which are allowed to be visited for the k.sup.th ant, i.e., feasible for the k.sup.th ant, and the feasible set is constrained by the assumption 2 stated above. Once the k.sup.th ant accomplishes its tour, the virtual pheromone .tau..sub.i,j(t) on the edge e(i,j) may be updated as .tau..sub.i,j(t+n)=.rho..tau..sub.i,j(t)+.DELTA..tau..sub.i,j. (eq. 2)
In eq.2, .rho. is an evaporation coefficient, meaning that (1-.rho.) of the pheromone .tau..sub.i,j(t) would be evaporated between the time t and the time (t+n), n is an amount of time which takes the k.sup.th ant to finish a tour. In other words, .rho..tau..sub.i,j(t) is the remaining pheromone on the edge e(i, j) at the time (t+n), and .DELTA..tau..sub.i,j is the newly laid pheromone on the edge e(i, j) between the time t and the time (t+n). The incremental virtual pheromone .DELTA..tau..sub.i,j may be expressed as
.DELTA..times..times..tau..times..DELTA..times..times..tau..times. ##EQU00002##
In eq.3, .DELTA..tau..sub.i,j.sup.k represents the pheromone laid by the k.sup.th ant on the edge e(i, j) between the time t and the time (t+n), K represents a total number of ants. The incremental pheromone .DELTA..tau..sub.i,j.sup.k may be expressed as
.DELTA..times..times..tau..times..times..times..times..times..times..time- s..times..times..times..times..times..times..times..times..times..times..t- imes..times. ##EQU00003##
In eq. 4, Q can be a constant representing a total amount of pheromone which is to be laid by the ant during its tour, and L.sub.k is the tour length of the k.sup.th ant.
The conventional ACO algorithm may be presented as Table I. In Table I, N.sub.itr denotes an iteration index, and step, from 1 to n, denotes a step index, meaning that each ant takes n steps to accomplish one tour, where one tour takes n units of time. From Table I, the tours taken by the K ants might converge to a specific tour, meaning that every ant may eventually select the shortest tour to travel, when the iteration index N.sub.itr is less than a maximum iteration limit N.sub.itr,MAX.
TABLE-US-00001 TABLE I 1 // Initialization 2 Set t = 0 3 Set N.sub.itr = 0 4 Set .tau..sub.i,j(t) = c for all edges and .DELTA..tau..sub.i,j =0 , for all i,j .di-elect cons. , where is the set of nodes 5 while (N.sub.itr< N.sub.itr,MAX) or (L.sub.k1 .noteq. L.sub.k2, .A-inverted. k1, k2.di-elect cons. {1,...,K}) do 6 Uniformly Place K ants on N nodes 7 .DELTA.t = 0 8 for step = 1 to n do 9 .DELTA.t = .DELTA.t +1 10 for k = 1 to K do 11 Move the k.sup.th ant from node i(step,k) to node j(step,k) according to eq. 1 12 Update F.sub.k 13 end 14 end 15 for k = 1 to K do 16 Calculate L.sub.k 17 Update pheromonal trails .tau..sub.i,j(t+n) according to eq.2, eq. 3 and eq. 4 18 Update the shortest tour found 19 end 20 t = t + .DELTA.t 21 N.sub.itr = N.sub.itr + 1 22 Reset .DELTA..tau..sub.i,j =0 for all i,j .di-elect cons. 23 end 24 Print Shortest Tour
By properly defining the graph (, ) the ACO algorithm may be applied to solve the resource allocation problem for the FD communication system. The resource allocation problem for the FD communication system is to assign the plurality of resource blocks RB to the plurality of user pairs UP, such that the overall system data rate can be maximized. In the present disclosure, a virtual node represents a user pair UP within a cell. A virtual edge represents a situation/status that two user pairs UP in two cells are assigned/allocated to the resource blocks RB with the probabilities defined in eq. 1.
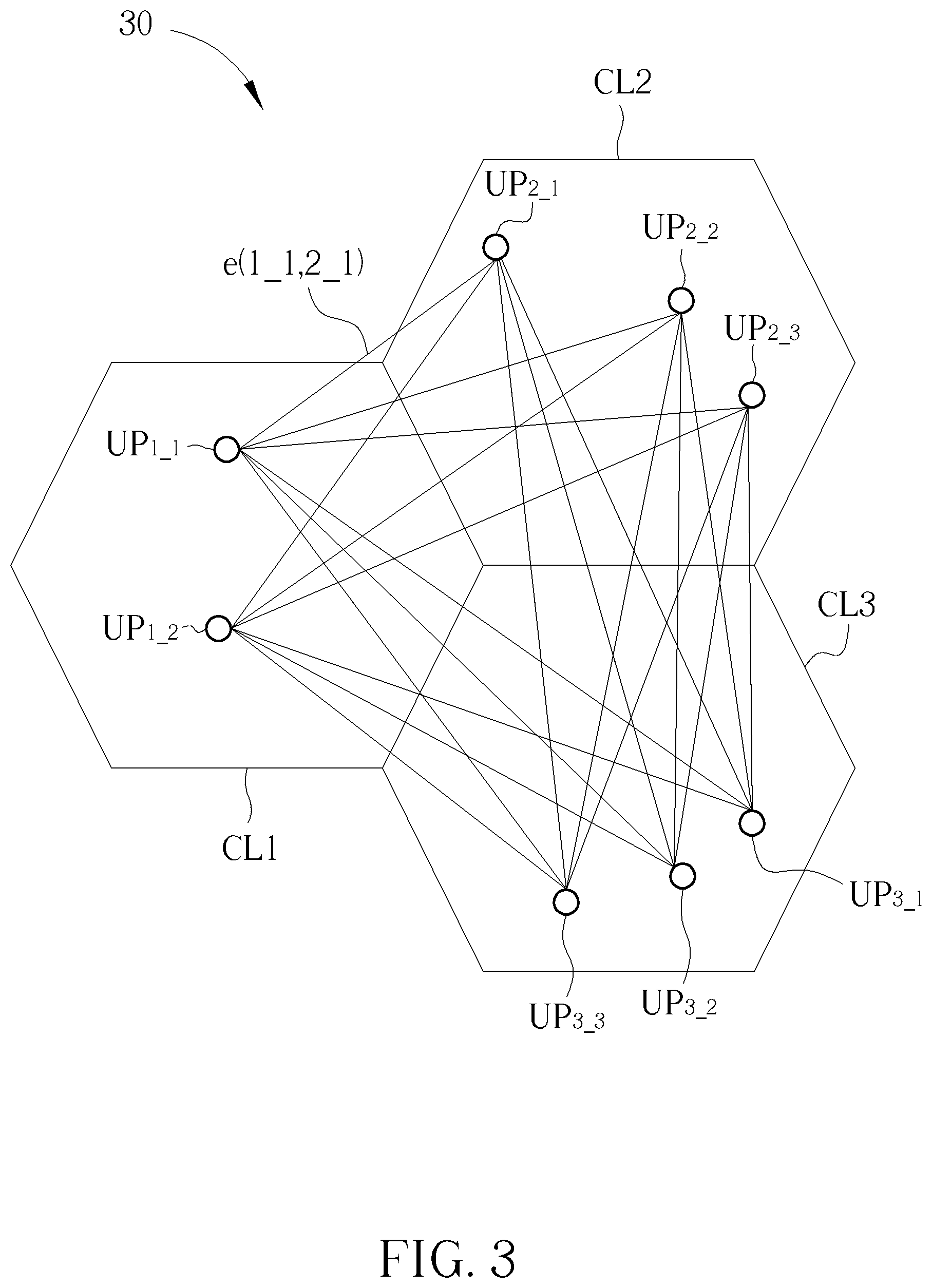
FIG. 3 illustrates a graphic representation of an FD communication system 30 according to an embodiment of the present disclosure. As shown in FIG. 3, the FD communication system 30 comprises cells CL1-CL3 corresponding to the stations BS.sub.1-BS.sub.3 (not shown in FIG. 3) respectively. The computing device of the FD communication system 30 is also not shown. User pairs (or virtual nodes) UP.sub.1_1-UP.sub.1_2, UP.sub.2_1-UP.sub.2_3, and UP.sub.3_1-UP.sub.3_3 are within the cells CL1, CL2, CL3, respectively. The straight lines in FIG. 3 represent edges between the virtual nodes UP.sub.1_1-UP.sub.1_2, UP.sub.2_1-UP.sub.2_3, UP.sub.3_1-UP.sub.3_3. The user pair (or the virtual node) UP.sub.x,y represents a downlink user device UE.sub.DL,y and a uplink user device UE.sub.UL,y, along with the station BS, corresponding to the cell CLx. In an embodiment, FIG. 3 may be interpreted as there are 4, 6, 6 users within the cells CL1, CL2, CL3, respectively, but not limited therein. In another embodiment, FIG. 3 may be interpreted as there are 2, 3, 3 users within the cells CL1, CL2, CL3, respectively. The terminologies "user" and "user device" are used interchangeably in the present disclosure. Note that, the virtual node UP.sub.x_y illustrated in FIG. 3 has nothing to do with practical positions of the downlink user device UE.sub.DL,y and the uplink user device UE.sub.UL,y, in the cell CLx.
A virtual edge e(1_1, 2_1) between the virtual nodes UP.sub.1_1 and UP.sub.2_1 represents that a specific resource block RB is allowed to be allocated to the user pair UP.sub.1_1 in the cell CL1 and the user pair UP.sub.2_1 in the CL2. Since one resource block RB is assigned to only one user pair in one cell, as shown in FIG. 3, there is no edge between virtual nodes within the same cell.
In an embodiment, a virtual edge distance d.sub.x1_y1,x2_y2 of a virtual edge e(x1_y1, x2_y2) between the virtual node UP.sub.x1_y1 in the cell CLx1 and the virtual node UP.sub.x2_y2 in the cell CLx2 may be defined as
.times..times..times..times..times..times..times..times..times..times..fu- nction..times..times..times..times..times..times..times..times..times..tim- es..times..times..function..times..times..times..times..times. ##EQU00004##
In another embodiment, the virtual edge distance d.sub.x1_y1,x2_y2 of the edge between the virtual node UP.sub.x1_y1 and the virtual node UP.sub.x2_y2 may be defined as
.times..times..times..times..times..times..times..times..times..times..fu- nction..times..times..times..times..times..times..times..times..times. ##EQU00005##
In eq. 5, the term "Rate (UP.sub.x2,y2)" may be a summation of transmission rates of downlink and uplink corresponding to user pair UP.sub.x2,y2 and the term "interference(UP.sub.x1,y1 to UP.sub.x2,y2)" may be interference caused by the user pair UP.sub.x1,y1 to UP.sub.x2,y2. In eq. 6, the term "Rate (UP.sub.x1,y1+UP.sub.x2,y2)" may be a summation of transmission rates of downlinks and uplinks corresponding to user pairs UP.sub.x1,y1 and UP.sub.x2,y2, respectively. The transmission rate corresponding to each link may be expressed as
.function..function..times..times..times. ##EQU00006##
In eq.7, the term "interference" represents an undesired signal power received at the user device UE and/or the station BS, and the term "signal power" represents desired signal power received at either the user device UE or the station BS.
FIG. 4 illustrates how the k.sup.th ant travels between the virtual nodes UP.sub.1_1-UP.sub.1_3, UP.sub.2_1-UP.sub.2_3, UP.sub.3_1-UP.sub.3_3, to allocate a resource block RB.sub.1. At the beginning, as shown in the subfigure 4a, the k.sup.th ant has 9 options, which means that the k.sup.th ant is allocated to one of the virtual nodes UP.sub.1_1-UP.sub.1_3, UP.sub.2_1-UP.sub.2_3, UP.sub.3_1-UP.sub.3_3, as a starting point. The feasible set Fk for the k.sup.th ant is Fk={UP.sub.1_1-UP.sub.1_3, UP.sub.2_1-UP.sub.2_3, UP.sub.3_1-UP.sub.3_3}. The decision of the k.sup.th ant choosing the starting point may be based on a plurality of initial probabilities, which will be described later on.
In an embodiment, the k.sup.th ant may be placed at the virtual node UP.sub.1_1, for example, as the starting point (or a first selected virtual node), as shown in the subfigure 4b. It means that the resource block RB.sub.1 may be assigned to the user pair UP.sub.1_1. The feasible set for the k.sup.th ant shrinks as Fk={UP.sub.2_1-UP.sub.2_3, UP.sub.3_1-UP.sub.3_3} by removing UP.sub.1_1-UP.sub.1_3 in the cell CL1, meaning that the k.sup.th ant has 6 options to move on for the next step.
In an embodiment, the k.sup.th ant may choose the virtual node UP.sub.2_2, for example, as the second visited virtual node (or a second selected virtual node), as shown in the subfigure 4c. An edge is formed between the virtual nodes UP.sub.1_1 and UP.sub.2_2, meaning that the resource block RB.sub.1 may have potential to be assigned to the user pairs UP.sub.1_1 and UP.sub.2_2. After the k.sup.th ant chooses the virtual node UP.sub.2_2, the feasible set for the k.sup.th ant shrinks as {UP.sub.3_1-UP.sub.3_3} by removing UP.sub.2_1-UP.sub.2_3 in the cell CL2, meaning that the k.sup.th ant has 3 options to move on for the next step.
In an embodiment, the k.sup.th ant may choose the virtual node UP.sub.3_3, for example, as the third visited virtual node (or a third selected virtual node), as shown in the subfigure 4d. The decision made by the k.sup.th ant to choose the next virtual node to visit may be based on a plurality of transition probabilities, which is similar to eq. 1 and will be detailed later on. After the k.sup.th ant chooses the virtual node UP.sub.3_3, the k.sup.th ant goes back to the starting point UP.sub.1_1, and finishes a first part of its tour, which is corresponding to the resource block RB.sub.1. The virtual path shown in FIG. 4 means that the resource block RB.sub.1 may be assigned to the user pairs UP.sub.1_1 in the cell CL1, UP.sub.2_2 in the cell CL2 and UP.sub.3_3 in the cell CL3.
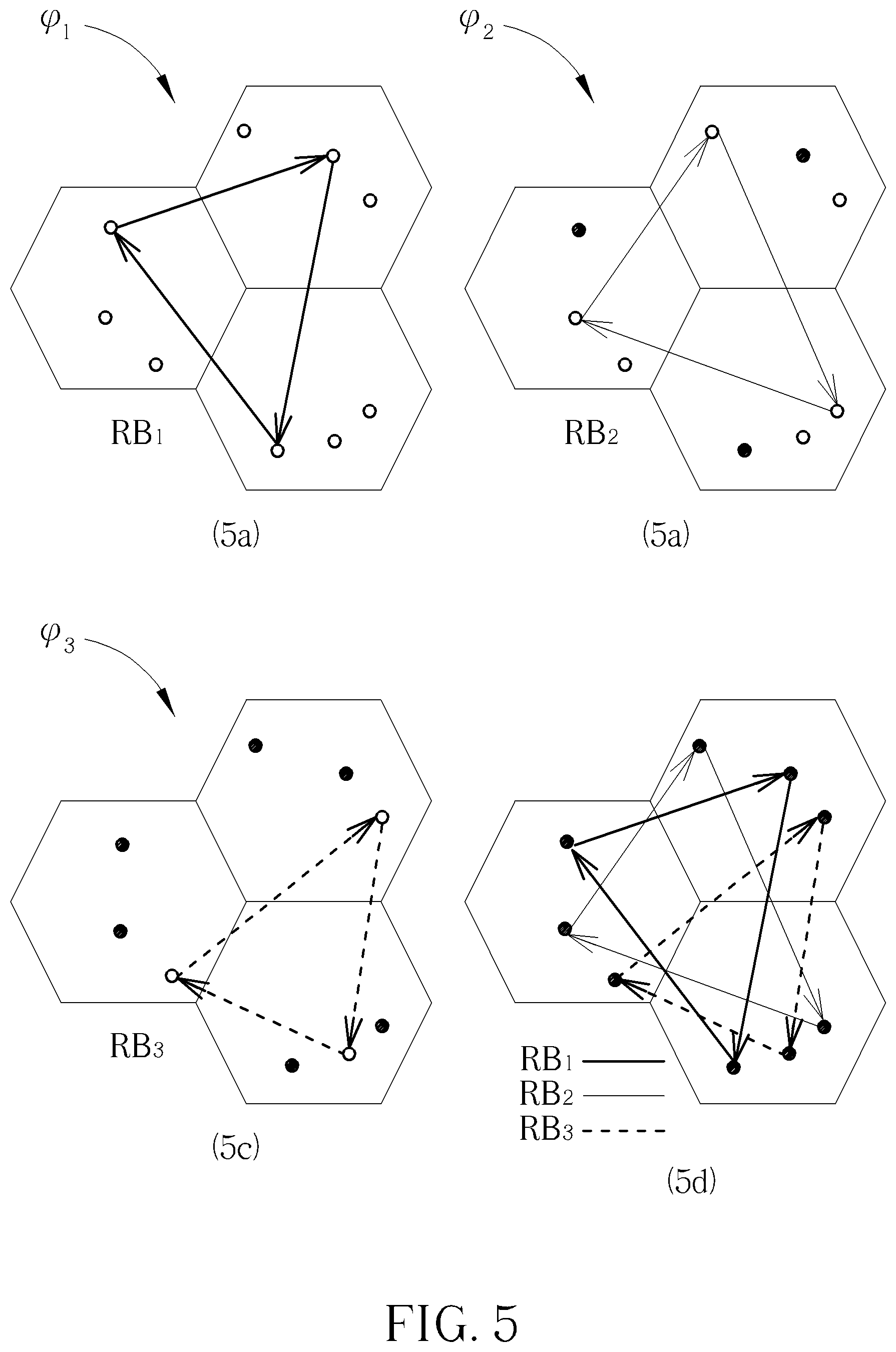
Specifically, FIG. 5 illustrates virtual paths .phi.1-.phi.3 of the k.sup.th ant to allocate resource blocks RB.sub.1-RB.sub.3. The virtual paths .phi.1-.phi.3, corresponding to the resource blocks RB.sub.1-RB.sub.3, are illustrated in the subFIGS. 5a-5c, respectively. The subfigure 5d illustrates a combination of the virtual paths .phi.1-.phi.3. The virtual paths .phi.1, .phi.2 and .phi.3 may be regarded as the first part, the second part and the third part of one tour .lamda..sub.k for of the k.sup.th ant, respectively, and form the tour .lamda..sub.k.
Given the user pairs UP have been analogized as the (virtual) nodes, to apply the ACO algorithm to the resource allocation problem in the FD communication system, it is necessary to provide a proper analogy of the tour length L.sub.k. In general, supposed that there are NRB resource blocks RB.sub.1-RB.sub.NRB to be allocated within the FD communication system, the virtual paths .phi..sub.1-.phi..sub.NRB form the virtual tour .lamda..sub.k of the k.sup.th ant, i.e., .lamda..sub.k=.phi.1+ . . . +.phi..sub.NRB. Or, equivalently, the virtual tour .lamda..sub.k includes the virtual paths .phi..sub.1-.phi..sub.NRB, and each virtual path .phi..sub.m includes a plurality of virtual edges e(x1_y1, x2_y2). Therefore, a virtual tour length .LAMBDA..sub.k corresponding to the virtual tour .lamda..sub.k may be expressed as
.LAMBDA..times..function..lamda..function..phi..function..phi..times..fun- ction..function..times. ##EQU00007##
In eq. 8, Length( ) represents a function outputting a virtual length/distance corresponding to a virtual tour or a virtual path, and d.sub.k(RB.sub.m) represents a virtual distance of the virtual path .phi..sub.m corresponding to the resource block RB.sub.m. In an embodiment, the virtual distance d.sub.k(RB.sub.m) may be expressed as
.function..times..times..times..times..times..times..times..times..times.- .times..times..times..times..times..times..times..times..times..times..tim- es..times..function..A-inverted..times..times..times..times..times..times.- .times..times..times..times..di-elect cons..phi..times. ##EQU00008##
In eq. 9, the virtual edge distance d.sub.x1_y1,x2_y2(RB.sub.m) may be obtained according to eq. 5 or eq. 6, given that the resource block RB.sub.m is assigned to the user pairs UP.sub.x1_y1, UP.sub.x2_y2, and UP.sub.x1_y1, UP.sub.x2_y2.di-elect cons..phi..sub.m represents that the virtual nodes UP.sub.x1_y1, UP.sub.x2_y2 are on the virtual path .phi..sub.m.
Given the virtual tour length .LAMBDA..sub.k has been analogized as the actual tour length L.sub.k, the modified ACO algorithm is presented in Table II, which is applied in the resource allocation problem in the FD communication system of the present disclosure.
TABLE-US-00002 TABLE II 1 // Initialization 2 Set t = 0 3 Set N.sub.itr = 0 4 Set .tau..sub.i,j(t) = c for all edges and .DELTA..tau..sub.i,j = 0 , .A-inverted.i.di-elect cons. , .A-inverted.j.di-elect cons. , .A-inverted.i,j.di-elect cons. i.noteq.j, , where is the set of nodes in cell b.sub.1, is the set of nodes in cell b.sub.2, is the set of BSs 5 while (N.sub.itr< N.sub.itr,MAX) or (L.sub.k1 .noteq. L.sub.k2, .A-inverted. k1, k2.di-elect cons. {1,...,K}) do 6 for r = 1 to NRB do 7 .DELTA.t = 0 8 for step = 1 to NBS do 9 .DELTA.t = .DELTA.t +1 10 for k = 1 to K do 11 Define: UP.sub.i(r,step,k) : a virtual node which the k.sup.th ant stays at "step" of r.sup.th RB 12 if step = 1 and r .noteq. 1 then 13 The k.sup.th ant chooses the virtual node UP.sub.i(r,step,k) as the starting point 14 else if step=1 and r=1 15 Uniformly Place the K ants on the (N.cndot.NBS) node to determine UP.sub.i(1,1,k) 16 else 17 The k.sup.th ant moves to the virtual node UP.sub.j(r,step,k) from virtual node UP.sub.i(r,step,k) where UP.sub.i(r,step+1,k)=UP.sub.j(r,step,k) 18 end 19 Update F.sub.k 20 end 21 end 22 end 23 for k = 1 to K do 24 Calculate .LAMBDA..sub.k according to eq. 8 25 Update pheromonal trails according to eq.2, eq. 3 and eq. 4, where L.sub.k in eq. 4 is replaced with .LAMBDA..sub.k 26 Update the shortest tour found 27 end 28 t = t + .DELTA.t 29 N.sub.itr = N.sub.itr + 1 30 Reset .DELTA..tau..sub.i,j =0, .A-inverted.i.di-elect cons. , .A-inverted.j.di-elect cons. , .A-inverted.i,j.di-elect cons. i.noteq.j, 31 end 32 Print Shortest Tour
In Table II, the virtual node indices x_y have been abbreviated as the indices i or j. N, NBS, NRB represent a number of user pairs within one cell, a number of stations BS and a number of resource blocks RB. The ants presented in Table II are artificial ants, meaning that the processing unit 120 may simulate the behavior of the artificial ants. In some embodiments, N could be different in different cells.
On Line 10 of Table II, the k.sup.th ant chooses to start from the virtual node UP.sub.i(r,step,k) according to a plurality of initial probabilities p.sub.I. In an embodiment, the initial probabilities p.sub.I,i.sup.k, corresponding to the virtual node UP.sub.i for the k.sup.th ant may be expressed as
.function..di-elect cons..times..function..times..times..di-elect cons..times. ##EQU00009##
In an embodiment, the k.sup.th ant may choose a virtual node based on the initial probabilities p.sub.I,i.sup.k.
On line 13, the k.sup.th ant may choose the virtual node UP, based on the initial probabilities p.sub.i,j.sup.k(t). In some embodiments, line 13 can be replaced by line 15 in Table II.
On Line 17 of Table II, the k.sup.th ant chooses to move to the virtual node UP, from virtual node UP.sub.i according to the transition probability p.sub.i,j.sup.k (t) shown in eq. 1. On Line 25 of Table II, the virtual tour length .LAMBDA..sub.k is substituted as the tour length L.sub.k into eq.4, such that the virtual pheromonal trail .tau..sub.i,j(t) is updated according to eq. 2 and eq. 3. In an embodiment, the k.sup.th ant may choose the virtual node UP.sub.j based on the initial probabilities p.sub.i,j.sup.k(t).
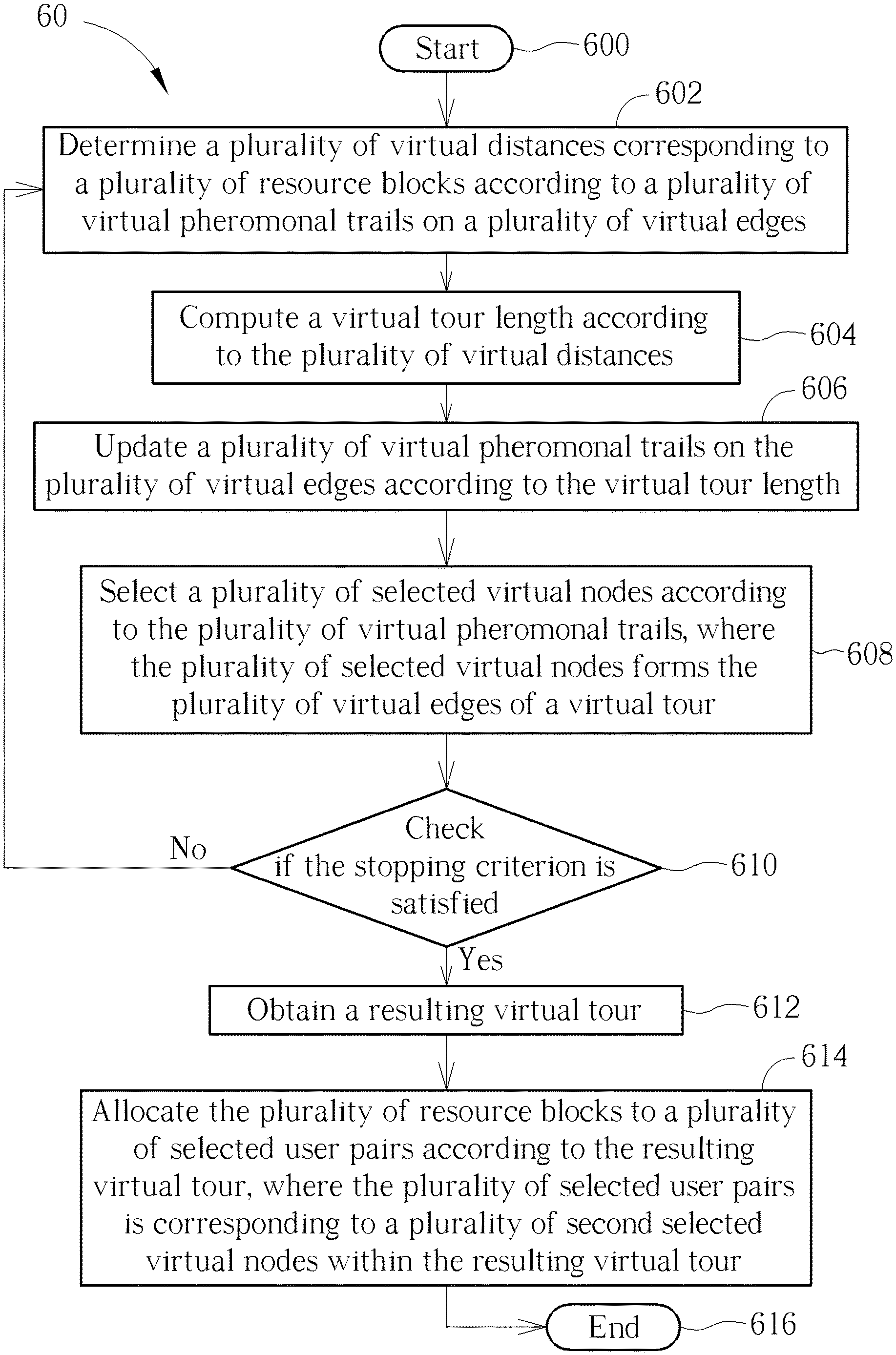
Operations of the ACO algorithm applied in the resource allocation problem in the FD communication system may be summarized as a resource allocation method 60. The resource allocation method 60 may be compiled as the program code 124 to instruct the processing unit 120 to execute the resource allocation method 60.
In the resource allocation method 60, Step 602 may be referred to the computation of the virtual distances d.sub.k(RB.sub.1), . . . , d.sub.k(RB.sub.NRB) in eq. 9, which may be referred back to eq. 5 or eq. 6. Step 604 may be referred to the operation of Line 24 in Table II or the computation of eq. 8. Step 606 may be referred to the operation of Line 25 in Table II or the computation of eq.2, eq. 3 and eq. 4. Step 608 may be referred to the operation of Lines 8-22 in Table II, which has been illustrated in FIG. 4 and FIG. 5. In Step 610, the stopping criterion is presented on Line 5 of Table II. The resulting tour obtained in Step 612 may be referred to the shortest tour in Line 32 of Table II, in which the resulting tour .lamda.* is obtained.
The resulting tour .lamda.* includes virtual paths .phi..sub.1*-.phi..sub.NRB* corresponding to the resource blocks RB.sub.1-RB.sub.NRB respectively. In step 614, according to the resulting tour .lamda.*, the resource block RB.sub.m is allocated to the user pairs corresponding to the virtual nodes on the virtual path .phi..sub.m*.
Note that, since the virtual distance or the virtual tour length is inversely proportional to the data rate, or the virtual distance or the virtual tour length decreases as the data rate increases, the shortest tour would bring the largest data rate.
In summary, the present disclosure utilizes the ACO algorithm to perform multi-cell resource allocation, which maximizes the system data rate for the FD multi-cell communication systems.
Those skilled in the art will readily observe that numerous modifications and alterations of the device and method may be made while retaining the teachings of the invention. Accordingly, the above disclosure should be construed as limited only by the metes and bounds of the appended claims.
* * * * *
D00000

D00001

D00002

D00003

D00004

D00005

D00006

M00001

M00002

M00003

M00004
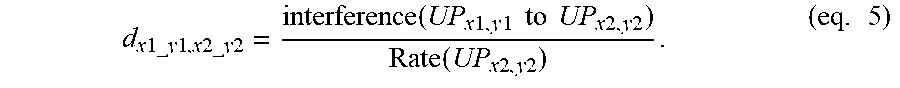
M00005
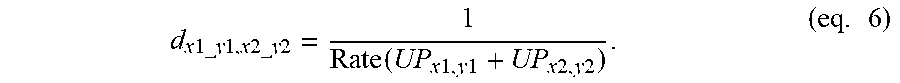
M00006

M00007

M00008

M00009

P00001

P00002

P00003

P00004

P00005

P00006
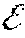
P00007
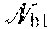
P00008

P00009

P00010

XML
uspto.report is an independent third-party trademark research tool that is not affiliated, endorsed, or sponsored by the United States Patent and Trademark Office (USPTO) or any other governmental organization. The information provided by uspto.report is based on publicly available data at the time of writing and is intended for informational purposes only.
While we strive to provide accurate and up-to-date information, we do not guarantee the accuracy, completeness, reliability, or suitability of the information displayed on this site. The use of this site is at your own risk. Any reliance you place on such information is therefore strictly at your own risk.
All official trademark data, including owner information, should be verified by visiting the official USPTO website at www.uspto.gov. This site is not intended to replace professional legal advice and should not be used as a substitute for consulting with a legal professional who is knowledgeable about trademark law.