Token generating component
Huxham , et al.
U.S. patent number 10,304,047 [Application Number 14/648,510] was granted by the patent office on 2019-05-28 for token generating component. This patent grant is currently assigned to Visa International Service Association. The grantee listed for this patent is Visa International Service Association. Invention is credited to Horatio Nelson Huxham, Tara Anne Moss, Alan Joseph O'Regan, Hough Arie Van Wyk.








| United States Patent | 10,304,047 |
| Huxham , et al. | May 28, 2019 |
| **Please see images for: ( Certificate of Correction ) ** |
Token generating component
Abstract
The invention provides a method and system for providing financial details from a mobile device of a user for use in a transaction. The method is performed on a mobile device of the user and includes the steps of generating, on a token generating component, a session-specific token by applying an algorithm requiring a dynamic key; providing financial details for use in a transaction; incorporating the session-specific token and the financial details into a modified form the financial details; and transferring the modified form of the financial details from the mobile device to initiate the transaction. A corresponding method and system for validating financial details received, at a server of an issuing authority, is also provided.
| Inventors: | Huxham; Horatio Nelson (Cape Town, ZA), O'Regan; Alan Joseph (Cape Town, ZA), Van Wyk; Hough Arie (Cape Town, ZA), Moss; Tara Anne (Cape Town, ZA) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Applicant: |
|
||||||||||
| Assignee: | Visa International Service
Association (San Francisco, CA) |
||||||||||
| Family ID: | 50882882 | ||||||||||
| Appl. No.: | 14/648,510 | ||||||||||
| Filed: | December 6, 2013 | ||||||||||
| PCT Filed: | December 06, 2013 | ||||||||||
| PCT No.: | PCT/IB2013/060696 | ||||||||||
| 371(c)(1),(2),(4) Date: | May 29, 2015 | ||||||||||
| PCT Pub. No.: | WO2014/087381 | ||||||||||
| PCT Pub. Date: | June 12, 2014 |
Prior Publication Data
| Document Identifier | Publication Date | |
|---|---|---|
| US 20150302390 A1 | Oct 22, 2015 | |
Foreign Application Priority Data
| Dec 7, 2012 [ZA] | 2012/09284 | |||
| Current U.S. Class: | 1/1 |
| Current CPC Class: | G06Q 20/327 (20130101); G06Q 20/3229 (20130101); G06Q 20/382 (20130101); H04W 12/004 (20190101); H04L 63/067 (20130101); G06F 21/35 (20130101); H04W 12/0608 (20190101); H04L 63/068 (20130101); G06F 2221/2137 (20130101) |
| Current International Class: | G06Q 20/32 (20120101); G06F 21/35 (20130101); G06Q 20/38 (20120101); H04L 29/06 (20060101); H04W 12/06 (20090101) |
| Field of Search: | ;705/67 |
References Cited [Referenced By]
U.S. Patent Documents
| 4423287 | December 1983 | Zeidler |
| 5412730 | May 1995 | Jones |
| 5613012 | March 1997 | Hoffman |
| 5781438 | July 1998 | Lee |
| 5883810 | March 1999 | Franklin |
| 5953710 | September 1999 | Fleming |
| 5956408 | September 1999 | Arnold |
| 5956699 | September 1999 | Wong |
| 6000832 | December 1999 | Franklin |
| 6014635 | January 2000 | Harris |
| 6044360 | March 2000 | Picciallo |
| 6058193 | May 2000 | Cordery |
| 6112187 | August 2000 | Fukawa |
| 6163771 | December 2000 | Walker |
| 6227447 | May 2001 | Campisano |
| 6236981 | May 2001 | Hill |
| 6267292 | July 2001 | Walker |
| 6327578 | December 2001 | Linehan |
| 6341724 | January 2002 | Campisano |
| 6385596 | May 2002 | Wiser |
| 6422462 | July 2002 | Cohen |
| 6425523 | July 2002 | Shem Ur |
| 6592044 | July 2003 | Wong |
| 6636833 | October 2003 | Flitcroft |
| 6667700 | December 2003 | McCanne |
| 6748367 | June 2004 | Lee |
| 6805287 | October 2004 | Bishop |
| 6879965 | April 2005 | Fung |
| 6891953 | May 2005 | DeMello |
| 6901387 | May 2005 | Wells |
| 6931382 | August 2005 | Laage |
| 6938019 | August 2005 | Uzo |
| 6941285 | September 2005 | Sarcanin |
| 6980670 | December 2005 | Hoffman |
| 6990470 | January 2006 | Hogan |
| 6991157 | January 2006 | Bishop |
| 6996722 | February 2006 | Fairman |
| 7011247 | March 2006 | Drabczuk |
| 7051929 | May 2006 | Li |
| 7069249 | June 2006 | Stolfo |
| 7069439 | June 2006 | Chen |
| 7103576 | September 2006 | Mann, III |
| 7113930 | September 2006 | Eccles |
| 7136835 | November 2006 | Flitcroft |
| 7177835 | February 2007 | Walker |
| 7177848 | February 2007 | Hogan |
| 7194437 | March 2007 | Britto |
| 7209561 | April 2007 | Shankar et al. |
| 7213766 | May 2007 | Ryan |
| 7264154 | September 2007 | Harris |
| 7287692 | October 2007 | Patel |
| 7292999 | November 2007 | Hobson |
| 7350230 | March 2008 | Forrest |
| 7353382 | April 2008 | Labrou |
| 7379919 | May 2008 | Hogan |
| RE40444 | July 2008 | Linehan |
| 7415443 | August 2008 | Hobson |
| 7430668 | September 2008 | Chen |
| 7444676 | October 2008 | Asghari-Kamrani |
| 7469151 | December 2008 | Khan |
| 7548889 | June 2009 | Bhambri |
| 7567934 | July 2009 | Flitcroft |
| 7567936 | July 2009 | Peckover |
| 7571139 | August 2009 | Giordano |
| 7571142 | August 2009 | Flitcroft |
| 7580898 | August 2009 | Brown |
| 7584153 | September 2009 | Brown |
| 7593896 | September 2009 | Flitcroft |
| 7606560 | October 2009 | Labrou |
| 7627531 | December 2009 | Breck |
| 7627895 | December 2009 | Gifford |
| 7650314 | January 2010 | Saunders |
| 7685037 | March 2010 | Reiners |
| 7702578 | April 2010 | Fung |
| 7707120 | April 2010 | Dominguez |
| 7712655 | May 2010 | Wong |
| 7734527 | June 2010 | Uzo |
| 7753265 | July 2010 | Harris |
| 7770789 | August 2010 | Oder, II |
| 7784685 | August 2010 | Hopkins, III |
| 7793851 | September 2010 | Mullen |
| 7801826 | September 2010 | Labrou |
| 7805376 | September 2010 | Smith |
| 7805378 | September 2010 | Berardi |
| 7818264 | October 2010 | Hammad |
| 7828220 | November 2010 | Mullen |
| 7835960 | November 2010 | Breck |
| 7841523 | November 2010 | Oder, II |
| 7841539 | November 2010 | Hewton |
| 7844550 | November 2010 | Walker |
| 7848980 | December 2010 | Carlson |
| 7849020 | December 2010 | Johnson |
| 7853529 | December 2010 | Walker |
| 7853995 | December 2010 | Chow |
| 7865414 | January 2011 | Fung |
| 7873579 | January 2011 | Hobson |
| 7873580 | January 2011 | Hobson |
| 7874010 | January 2011 | Perlman |
| 7890393 | February 2011 | Talbert |
| 7891563 | February 2011 | Oder, II |
| 7896238 | March 2011 | Fein |
| 7908216 | March 2011 | Davis et al. |
| 7922082 | April 2011 | Muscato |
| 7931195 | April 2011 | Mullen |
| 7937324 | May 2011 | Patterson |
| 7938318 | May 2011 | Fein |
| 7954705 | June 2011 | Mullen |
| 7959076 | June 2011 | Hopkins, III |
| 7996288 | August 2011 | Stolfo |
| 8025223 | September 2011 | Saunders |
| 8046256 | October 2011 | Chien et al. |
| 8060448 | November 2011 | Jones |
| 8060449 | November 2011 | Zhu |
| 8074877 | December 2011 | Mullen |
| 8074879 | December 2011 | Harris |
| 8078593 | December 2011 | Ramarao |
| 8082210 | December 2011 | Hansen |
| 8095113 | January 2012 | Kean |
| 8104679 | January 2012 | Brown |
| RE43157 | February 2012 | Bishop |
| 8109436 | February 2012 | Hopkins, III |
| 8121295 | February 2012 | Everson |
| 8121942 | February 2012 | Carlson |
| 8121956 | February 2012 | Carlson |
| 8126449 | February 2012 | Beenau |
| 8151345 | April 2012 | Yeager |
| 8171525 | May 2012 | Pelly |
| 8175973 | May 2012 | Davis et al. |
| 8190523 | May 2012 | Patterson |
| 8196813 | June 2012 | Vadhri |
| 8205791 | June 2012 | Randazza |
| 8219489 | July 2012 | Patterson |
| 8224702 | July 2012 | Mengerink |
| 8225385 | July 2012 | Chow |
| 8229852 | July 2012 | Carlson |
| 8265993 | September 2012 | Chien |
| 8280777 | October 2012 | Mengerink |
| 8281991 | October 2012 | Wentker et al. |
| 8307210 | November 2012 | Duane |
| 8328095 | December 2012 | Oder, II |
| 8336088 | December 2012 | Raj et al. |
| 8346666 | January 2013 | Lindelsee et al. |
| 8376225 | February 2013 | Hopkins, III |
| 8380177 | February 2013 | Laracey |
| 8387873 | March 2013 | Saunders |
| 8401539 | March 2013 | Beenau |
| 8401898 | March 2013 | Chien |
| 8402555 | March 2013 | Grecia |
| 8403211 | March 2013 | Brooks |
| 8412623 | April 2013 | Moon |
| 8412837 | April 2013 | Emigh |
| 8417642 | April 2013 | Oren |
| 8447699 | May 2013 | Batada |
| 8453223 | May 2013 | Svigals |
| 8453925 | June 2013 | Fisher |
| 8458487 | June 2013 | Palgon |
| 8484134 | July 2013 | Hobson |
| 8485437 | July 2013 | Mullen |
| 8494959 | July 2013 | Hathaway |
| 8498908 | July 2013 | Mengerink |
| 8504475 | August 2013 | Brand et al. |
| 8504478 | August 2013 | Saunders |
| 8510816 | August 2013 | Quach |
| 8433116 | September 2013 | Davis et al. |
| 8533860 | September 2013 | Grecia |
| 8538845 | September 2013 | Liberty |
| 8555079 | October 2013 | Shablygin |
| 8566168 | October 2013 | Bierbaum |
| 8567670 | October 2013 | Stanfield |
| 8571939 | October 2013 | Lindsey |
| 8577336 | November 2013 | Mechaley, Jr. |
| 8577803 | November 2013 | Chatterjee |
| 8577813 | November 2013 | Weiss |
| 8578176 | November 2013 | Mattsson |
| 8583494 | November 2013 | Fisher |
| 8584251 | November 2013 | Mcguire |
| 8589237 | November 2013 | Fisher |
| 8589271 | November 2013 | Evans |
| 8589291 | November 2013 | Carlson |
| 8595098 | November 2013 | Starai |
| 8595812 | November 2013 | Bomar |
| 8595850 | November 2013 | Spies |
| 8606638 | December 2013 | Dragt |
| 8606700 | December 2013 | Carlson |
| 8606720 | December 2013 | Baker |
| 8615468 | December 2013 | Varadarajan |
| 8620754 | December 2013 | Fisher |
| 8635157 | January 2014 | Smith |
| 8646059 | February 2014 | Von Behren |
| 8651374 | February 2014 | Brabson |
| 8656180 | February 2014 | Shablygin |
| 8751391 | June 2014 | Freund |
| 8762263 | June 2014 | Gauthier et al. |
| 8793186 | July 2014 | Patterson |
| 8838982 | September 2014 | Carlson et al. |
| 8856539 | October 2014 | Weiss |
| 8887308 | November 2014 | Grecia |
| 9065643 | June 2015 | Hurry et al. |
| 9070129 | June 2015 | Sheets et al. |
| 9100826 | August 2015 | Weiss |
| 9160741 | October 2015 | Wentker et al. |
| 9229964 | January 2016 | Stevelinck |
| 9245267 | January 2016 | Singh |
| 9249241 | February 2016 | Dai et al. |
| 9256871 | February 2016 | Anderson et al. |
| 9271110 | February 2016 | Fultz |
| 9280765 | March 2016 | Hammad |
| 9530137 | December 2016 | Weiss |
| 9860245 | January 2018 | Ronda |
| 9911117 | March 2018 | Everhart |
| 2001/0029485 | October 2001 | Brody |
| 2001/0034720 | October 2001 | Armes |
| 2001/0054003 | December 2001 | Chien |
| 2002/0007320 | January 2002 | Hogan |
| 2002/0016749 | February 2002 | Borecki |
| 2002/0029193 | March 2002 | Ranjan |
| 2002/0035548 | March 2002 | Hogan |
| 2002/0073045 | June 2002 | Rubin |
| 2002/0116341 | August 2002 | Hogan |
| 2002/0133467 | September 2002 | Hobson |
| 2002/0147913 | October 2002 | Lun Yip |
| 2002/0184511 | December 2002 | Kolouch |
| 2003/0028481 | February 2003 | Flitcroft |
| 2003/0084292 | May 2003 | Pierce |
| 2003/0130955 | July 2003 | Hawthorne |
| 2003/0191709 | October 2003 | Elston |
| 2003/0191945 | October 2003 | Keech |
| 2003/0212894 | November 2003 | Buck |
| 2004/0010462 | January 2004 | Moon |
| 2004/0034783 | February 2004 | Fedronic |
| 2004/0050928 | March 2004 | Bishop |
| 2004/0059682 | March 2004 | Hasumi |
| 2004/0093281 | May 2004 | Silverstein |
| 2004/0139008 | July 2004 | Mascavage |
| 2004/0143532 | July 2004 | Lee |
| 2004/0158532 | August 2004 | Breck |
| 2004/0210449 | October 2004 | Breck |
| 2004/0210498 | October 2004 | Freund |
| 2004/0232225 | November 2004 | Bishop |
| 2004/0260646 | December 2004 | Berardi |
| 2005/0037735 | February 2005 | Coutts |
| 2005/0069171 | March 2005 | Rhoads |
| 2005/0080730 | April 2005 | Sorrentino |
| 2005/0108178 | May 2005 | York |
| 2005/0137983 | June 2005 | Bells |
| 2005/0140964 | June 2005 | Eschenauer |
| 2005/0154923 | July 2005 | Lok |
| 2005/0166263 | July 2005 | Nanopoulos |
| 2005/0190914 | September 2005 | Chen |
| 2005/0199709 | September 2005 | Linlor |
| 2005/0246293 | November 2005 | Ong |
| 2005/0269401 | December 2005 | Spitzer |
| 2005/0269402 | December 2005 | Spitzer |
| 2005/0283441 | December 2005 | Ekberg |
| 2006/0075254 | April 2006 | Henniger |
| 2006/0235795 | October 2006 | Johnson |
| 2006/0237528 | October 2006 | Bishop |
| 2006/0255158 | November 2006 | Margalit |
| 2006/0278704 | December 2006 | Saunders |
| 2006/0287965 | December 2006 | Bajan |
| 2006/0288216 | December 2006 | Buhler |
| 2007/0066398 | March 2007 | Rowan |
| 2007/0067833 | March 2007 | Colnot |
| 2007/0107044 | May 2007 | Yuen |
| 2007/0129955 | June 2007 | Dalmia |
| 2007/0136193 | June 2007 | Starr |
| 2007/0136211 | June 2007 | Brown |
| 2007/0143227 | June 2007 | Kranzley |
| 2007/0150942 | June 2007 | Cartmell |
| 2007/0170247 | July 2007 | Friedman |
| 2007/0179885 | August 2007 | Bird |
| 2007/0208671 | September 2007 | Brown |
| 2007/0245414 | October 2007 | Chan |
| 2007/0262138 | November 2007 | Somers |
| 2007/0288377 | December 2007 | Shaked |
| 2007/0291995 | December 2007 | Rivera |
| 2008/0015988 | January 2008 | Brown |
| 2008/0029607 | February 2008 | Mullen |
| 2008/0035738 | February 2008 | Mullen |
| 2008/0052226 | February 2008 | Agarwal |
| 2008/0054068 | March 2008 | Mullen |
| 2008/0054079 | March 2008 | Mullen |
| 2008/0054081 | March 2008 | Mullen |
| 2008/0065554 | March 2008 | Hogan |
| 2008/0065555 | March 2008 | Mullen |
| 2008/0148057 | June 2008 | Hauw |
| 2008/0172738 | July 2008 | Bates |
| 2008/0201264 | August 2008 | Brown |
| 2008/0201265 | August 2008 | Hewton |
| 2008/0228646 | September 2008 | Myers |
| 2008/0243702 | October 2008 | Hart |
| 2008/0245855 | October 2008 | Fein |
| 2008/0245861 | October 2008 | Fein |
| 2008/0283591 | November 2008 | Oder, II |
| 2008/0302869 | December 2008 | Mullen |
| 2008/0302876 | December 2008 | Mullen |
| 2008/0313264 | December 2008 | Pestoni |
| 2009/0006262 | January 2009 | Brown |
| 2009/0010488 | January 2009 | Matsuoka |
| 2009/0037333 | February 2009 | Flitcroft |
| 2009/0037388 | February 2009 | Cooper |
| 2009/0043702 | February 2009 | Bennett |
| 2009/0048971 | February 2009 | Hathaway |
| 2009/0060184 | March 2009 | Alten |
| 2009/0106112 | April 2009 | Dalmia |
| 2009/0106160 | April 2009 | Skowronek |
| 2009/0134217 | May 2009 | Flitcroft |
| 2009/0157555 | June 2009 | Biffle |
| 2009/0159673 | June 2009 | Mullen |
| 2009/0159700 | June 2009 | Mullen |
| 2009/0159707 | June 2009 | Mullen |
| 2009/0173782 | July 2009 | Muscato |
| 2009/0200371 | August 2009 | Kean |
| 2009/0248583 | October 2009 | Chhabra |
| 2009/0276347 | November 2009 | Kargman |
| 2009/0281948 | November 2009 | Carlson |
| 2009/0294527 | December 2009 | Brabson |
| 2009/0307139 | December 2009 | Mardikar |
| 2009/0308921 | December 2009 | Mullen |
| 2009/0313318 | December 2009 | Dye |
| 2009/0327131 | December 2009 | Beenau |
| 2010/0008535 | January 2010 | Abulafia |
| 2010/0017867 | January 2010 | Fascenda |
| 2010/0024024 | January 2010 | Siourthas |
| 2010/0077216 | March 2010 | Kramer |
| 2010/0088237 | April 2010 | Wankmueller |
| 2010/0094755 | April 2010 | Kloster |
| 2010/0106644 | April 2010 | Annan |
| 2010/0120408 | May 2010 | Beenau |
| 2010/0133334 | June 2010 | Vadhri |
| 2010/0138347 | June 2010 | Chen |
| 2010/0145860 | June 2010 | Pelegero |
| 2010/0161433 | June 2010 | White |
| 2010/0185545 | July 2010 | Royyuru |
| 2010/0211505 | August 2010 | Saunders |
| 2010/0223186 | September 2010 | Hogan |
| 2010/0228668 | September 2010 | Hogan |
| 2010/0235284 | September 2010 | Moore |
| 2010/0258620 | October 2010 | Torreyson |
| 2010/0289627 | November 2010 | McAllister |
| 2010/0291904 | November 2010 | Musfeldt |
| 2010/0299267 | November 2010 | Faith et al. |
| 2010/0306076 | December 2010 | Taveau |
| 2010/0325041 | December 2010 | Berardi |
| 2011/0010292 | January 2011 | Giordano |
| 2011/0016047 | January 2011 | Wu |
| 2011/0016320 | January 2011 | Bergsten |
| 2011/0040640 | February 2011 | Erikson |
| 2011/0047076 | February 2011 | Carlson et al. |
| 2011/0083018 | April 2011 | Kesanupalli |
| 2011/0087596 | April 2011 | Dorsey |
| 2011/0093397 | April 2011 | Carlson |
| 2011/0103586 | May 2011 | Nobre |
| 2011/0125597 | May 2011 | Oder, II |
| 2011/0153437 | June 2011 | Archer |
| 2011/0153498 | June 2011 | Makhotin et al. |
| 2011/0154466 | June 2011 | Harper |
| 2011/0154467 | June 2011 | Bomar |
| 2011/0161233 | June 2011 | Tieken |
| 2011/0178926 | July 2011 | Lindelsee et al. |
| 2011/0191244 | August 2011 | Dai |
| 2011/0191592 | August 2011 | Goertzen |
| 2011/0197070 | August 2011 | Mizrah |
| 2011/0237224 | September 2011 | Coppinger |
| 2011/0238511 | September 2011 | Park |
| 2011/0238573 | September 2011 | Varadarajan |
| 2011/0246317 | October 2011 | Coppinger |
| 2011/0251892 | October 2011 | Laracey |
| 2011/0258111 | October 2011 | Raj et al. |
| 2011/0272471 | November 2011 | Mullen |
| 2011/0272478 | November 2011 | Mullen |
| 2011/0276380 | November 2011 | Mullen |
| 2011/0276381 | November 2011 | Mullen |
| 2011/0276424 | November 2011 | Mullen |
| 2011/0276425 | November 2011 | Mullen |
| 2011/0295745 | December 2011 | White |
| 2011/0302081 | December 2011 | Saunders |
| 2011/0307699 | December 2011 | Fielder |
| 2012/0023567 | January 2012 | Hammad |
| 2012/0028609 | February 2012 | Hruska |
| 2012/0030047 | February 2012 | Fuentes et al. |
| 2012/0035998 | February 2012 | Chien |
| 2012/0041881 | February 2012 | Basu |
| 2012/0047237 | February 2012 | Arvidsson |
| 2012/0060025 | March 2012 | Cahill |
| 2012/0066078 | March 2012 | Kingston |
| 2012/0072350 | March 2012 | Goldthwaite |
| 2012/0078735 | March 2012 | Bauer |
| 2012/0078798 | March 2012 | Downing |
| 2012/0078799 | March 2012 | Jackson |
| 2012/0095852 | April 2012 | Bauer |
| 2012/0095865 | April 2012 | Doherty |
| 2012/0110318 | May 2012 | Stone |
| 2012/0116902 | May 2012 | Cardina |
| 2012/0123882 | May 2012 | Carlson |
| 2012/0123940 | May 2012 | Killian |
| 2012/0129514 | May 2012 | Beenau |
| 2012/0143767 | June 2012 | Abadir |
| 2012/0143772 | June 2012 | Abadir |
| 2012/0158580 | June 2012 | Eram |
| 2012/0158593 | June 2012 | Garfinkle |
| 2012/0173431 | July 2012 | Ritchie |
| 2012/0179952 | July 2012 | Tuyls |
| 2012/0185386 | July 2012 | Salama |
| 2012/0197807 | August 2012 | Schlesser |
| 2012/0203664 | August 2012 | Torossian |
| 2012/0203666 | August 2012 | Torossian |
| 2012/0203700 | August 2012 | Ornce |
| 2012/0215688 | August 2012 | Musser |
| 2012/0215696 | August 2012 | Salonen |
| 2012/0221421 | August 2012 | Hammad |
| 2012/0221859 | August 2012 | Marien |
| 2012/0226582 | September 2012 | Hammad |
| 2012/0231844 | September 2012 | Coppinger |
| 2012/0233004 | September 2012 | Bercaw |
| 2012/0246070 | September 2012 | Vadhri |
| 2012/0246071 | September 2012 | Jain |
| 2012/0246079 | September 2012 | Wilson et al. |
| 2012/0265631 | October 2012 | Cronic |
| 2012/0271770 | October 2012 | Harris |
| 2012/0297446 | November 2012 | Webb |
| 2012/0300932 | November 2012 | Cambridge |
| 2012/0303503 | November 2012 | Cambridge |
| 2012/0303961 | November 2012 | Kean |
| 2012/0304273 | November 2012 | Bailey |
| 2012/0310725 | December 2012 | Chien |
| 2012/0310831 | December 2012 | Harris |
| 2012/0316992 | December 2012 | Oborne |
| 2012/0317035 | December 2012 | Royyuru |
| 2012/0317036 | December 2012 | Bower |
| 2013/0017784 | January 2013 | Fisher |
| 2013/0018757 | January 2013 | Anderson et al. |
| 2013/0019098 | January 2013 | Gupta |
| 2013/0031006 | January 2013 | Mccullagh et al. |
| 2013/0047263 | February 2013 | Radhakrishnan |
| 2013/0054337 | February 2013 | Brendell |
| 2013/0054466 | February 2013 | Muscato |
| 2013/0054474 | February 2013 | Yeager |
| 2013/0081122 | March 2013 | Svigals |
| 2013/0085944 | April 2013 | Fielder |
| 2013/0091028 | April 2013 | Oder, II |
| 2013/0110658 | May 2013 | Lyman |
| 2013/0111599 | May 2013 | Gargiulo |
| 2013/0117185 | May 2013 | Collison |
| 2013/0124290 | May 2013 | Fisher |
| 2013/0124291 | May 2013 | Fisher |
| 2013/0124364 | May 2013 | Mittal |
| 2013/0138525 | May 2013 | Bercaw |
| 2013/0144888 | June 2013 | Faith |
| 2013/0145148 | June 2013 | Shablygin |
| 2013/0145172 | June 2013 | Shablygin |
| 2013/0159178 | June 2013 | Colon |
| 2013/0159184 | June 2013 | Thaw |
| 2013/0159195 | June 2013 | Kirillin |
| 2013/0166402 | June 2013 | Parento |
| 2013/0166456 | June 2013 | Zhang |
| 2013/0173736 | July 2013 | Krzeminski |
| 2013/0185202 | July 2013 | Goldthwaite |
| 2013/0191286 | July 2013 | Cronic |
| 2013/0191289 | July 2013 | Cronic |
| 2013/0198071 | August 2013 | Jurss |
| 2013/0198080 | August 2013 | Anderson et al. |
| 2013/0200146 | August 2013 | Moghadam |
| 2013/0204787 | August 2013 | Dubois |
| 2013/0204793 | August 2013 | Kerridge |
| 2013/0212007 | August 2013 | Mattsson |
| 2013/0212017 | August 2013 | Bangia |
| 2013/0212019 | August 2013 | Mattsson |
| 2013/0212024 | August 2013 | Mattsson |
| 2013/0212026 | August 2013 | Powell et al. |
| 2013/0212666 | August 2013 | Mattsson |
| 2013/0218698 | August 2013 | Moon |
| 2013/0218769 | August 2013 | Pourfallah et al. |
| 2013/0226799 | August 2013 | Raj |
| 2013/0226813 | August 2013 | Voltz |
| 2013/0226815 | August 2013 | Ibasco |
| 2013/0246199 | September 2013 | Carlson |
| 2013/0246202 | September 2013 | Tobin |
| 2013/0246203 | September 2013 | Laracey |
| 2013/0246258 | September 2013 | Dessert |
| 2013/0246259 | September 2013 | Dessert |
| 2013/0246261 | September 2013 | Purves et al. |
| 2013/0246267 | September 2013 | Tobin |
| 2013/0254028 | September 2013 | Salci |
| 2013/0254052 | September 2013 | Royyuru |
| 2013/0254102 | September 2013 | Royyuru |
| 2013/0254117 | September 2013 | Von Mueller |
| 2013/0262296 | October 2013 | Thomas |
| 2013/0262302 | October 2013 | Lettow |
| 2013/0262315 | October 2013 | Hruska |
| 2013/0262316 | October 2013 | Hruska |
| 2013/0262317 | October 2013 | Collinge |
| 2013/0275300 | October 2013 | Killian |
| 2013/0275307 | October 2013 | Khan |
| 2013/0275308 | October 2013 | Paraskeva |
| 2013/0282502 | October 2013 | Jooste |
| 2013/0282575 | October 2013 | Mullen |
| 2013/0282588 | October 2013 | Hruska |
| 2013/0290719 | October 2013 | Kaler |
| 2013/0297501 | November 2013 | Monk et al. |
| 2013/0297504 | November 2013 | Nwokolo |
| 2013/0297508 | November 2013 | Belamant |
| 2013/0304649 | November 2013 | Cronic |
| 2013/0308778 | November 2013 | Fosmark |
| 2013/0311382 | November 2013 | Fosmark |
| 2013/0317982 | November 2013 | Mengerink |
| 2013/0326602 | December 2013 | Chen |
| 2013/0332344 | December 2013 | Weber |
| 2013/0339253 | December 2013 | Sincai |
| 2013/0346314 | December 2013 | Mogollon |
| 2014/0004817 | January 2014 | Horton |
| 2014/0007213 | January 2014 | Sanin |
| 2014/0013106 | January 2014 | Redpath |
| 2014/0013114 | January 2014 | Redpath |
| 2014/0013452 | January 2014 | Aissi et al. |
| 2014/0019352 | January 2014 | Shrivastava |
| 2014/0019364 | January 2014 | Hurry |
| 2014/0019752 | January 2014 | Yin |
| 2014/0025581 | January 2014 | Calman |
| 2014/0025585 | January 2014 | Calman |
| 2014/0025958 | January 2014 | Calman |
| 2014/0032417 | January 2014 | Mattsson |
| 2014/0032418 | January 2014 | Weber |
| 2014/0040137 | February 2014 | Carlson |
| 2014/0040139 | February 2014 | Brudnicki |
| 2014/0040144 | February 2014 | Plomske |
| 2014/0040145 | February 2014 | Ozvat |
| 2014/0040148 | February 2014 | Ozvat |
| 2014/0040628 | February 2014 | Fort |
| 2014/0041018 | February 2014 | Bomar |
| 2014/0046853 | February 2014 | Spies |
| 2014/0047551 | February 2014 | Nagasundaram et al. |
| 2014/0052532 | February 2014 | Tsai |
| 2014/0052620 | February 2014 | Rogers |
| 2014/0052637 | February 2014 | Jooste |
| 2014/0068706 | March 2014 | Aissi |
| 2014/0074637 | March 2014 | Hammad |
| 2014/0082366 | March 2014 | Engler |
| 2014/0108172 | April 2014 | Weber et al. |
| 2014/0114857 | April 2014 | Griggs et al. |
| 2014/0136418 | May 2014 | Fielder |
| 2014/0143137 | May 2014 | Carlson |
| 2014/0164243 | June 2014 | Aabye et al. |
| 2014/0188586 | July 2014 | Carpenter et al. |
| 2014/0294701 | October 2014 | Dai et al. |
| 2014/0297534 | October 2014 | Patterson |
| 2014/0310183 | October 2014 | Weber |
| 2014/0330721 | November 2014 | Wang |
| 2014/0330722 | November 2014 | Laxminarayanan et al. |
| 2014/0331265 | November 2014 | Mozell et al. |
| 2014/0337236 | November 2014 | Wong et al. |
| 2014/0344153 | November 2014 | Raj et al. |
| 2014/0372308 | December 2014 | Sheets |
| 2015/0019443 | January 2015 | Sheets et al. |
| 2015/0032625 | January 2015 | Dill |
| 2015/0032626 | January 2015 | Dill |
| 2015/0032627 | January 2015 | Dill |
| 2015/0046338 | February 2015 | Laxminarayanan |
| 2015/0046339 | February 2015 | Wong et al. |
| 2015/0052064 | February 2015 | Karpenko et al. |
| 2015/0088756 | March 2015 | Makhotin et al. |
| 2015/0106239 | April 2015 | Gaddam et al. |
| 2015/0112870 | April 2015 | Nagasundaram et al. |
| 2015/0112871 | April 2015 | Kumnick |
| 2015/0120472 | April 2015 | Aabye et al. |
| 2015/0127529 | May 2015 | Makhotin et al. |
| 2015/0127547 | May 2015 | Powell et al. |
| 2015/0128243 | May 2015 | Roux |
| 2015/0140960 | May 2015 | Powell et al. |
| 2015/0142673 | May 2015 | Nelsen et al. |
| 2015/0161597 | June 2015 | Subramanian et al. |
| 2015/0178724 | June 2015 | Ngo et al. |
| 2015/0180836 | June 2015 | Wong et al. |
| 2015/0186864 | July 2015 | Jones et al. |
| 2015/0193222 | July 2015 | Pirzadeh et al. |
| 2015/0195133 | July 2015 | Sheets et al. |
| 2015/0199679 | July 2015 | Palanisamy et al. |
| 2015/0199689 | July 2015 | Kumnick et al. |
| 2015/0220917 | August 2015 | Aabye et al. |
| 2015/0269566 | September 2015 | Gaddam et al. |
| 2015/0312038 | October 2015 | Palanisamy |
| 2015/0319158 | November 2015 | Kumnick |
| 2015/0332262 | November 2015 | Lingappa |
| 2015/0356560 | December 2015 | Shastry et al. |
| 2016/0028550 | January 2016 | Gaddam et al. |
| 2016/0042263 | February 2016 | Gaddam et al. |
| 2016/0065370 | March 2016 | Le Saint et al. |
| 2016/0092696 | March 2016 | Guglani et al. |
| 2016/0092872 | March 2016 | Prakash et al. |
| 2016/0103675 | April 2016 | Aabye et al. |
| 2016/0119296 | April 2016 | Laxminarayanan et al. |
| 2016/0224976 | August 2016 | Basu |
| 2017/0046696 | February 2017 | Powell et al. |
| 2017/0103387 | April 2017 | Weber |
| 2017/0220818 | August 2017 | Nagasundaram et al. |
| 2017/0228723 | August 2017 | Taylor |
| 2156397 | Feb 2010 | EP | |||
| 2001035304 | May 2001 | WO | |||
| 2001035304 | May 2001 | WO | |||
| 2004042536 | May 2004 | WO | |||
| 2006113834 | Oct 2006 | WO | |||
| 2009032523 | Mar 2009 | WO | |||
| 2010078522 | Jul 2010 | WO | |||
| 2012068078 | May 2012 | WO | |||
| WO2012064280 | May 2012 | WO | |||
| 2012098556 | Jul 2012 | WO | |||
| 2012142370 | Oct 2012 | WO | |||
| 2012167941 | Dec 2012 | WO | |||
| 2013048538 | Apr 2013 | WO | |||
| 2013056104 | Apr 2013 | WO | |||
| 2013119914 | Aug 2013 | WO | |||
| 2013179271 | Dec 2013 | WO | |||
Other References
|
Petition for Inter Partes Review of U.S. Pat. No. 8,533,860 Challenging Claims 1-30 Under 35 U.S.C. .sctn. 312 and 37 C.F.R. .sctn. 42.104, filed Feb. 17, 2016, Before the USPTO Patent Trial and Appeal Board, IPR 2016-00600, 65 pages. cited by applicant . Wang, U.S. Appl. No. 62/000,288 (unpublished), Payment System Canonical Address Format filed May 19, 2014. cited by applicant . Sharma et al., U.S. Appl. No. 62/003,717 (unpublished), Mobile Merchant Application filed May 28, 2014. cited by applicant . Kalgi et al., U.S. Appl. No. 62/024,426, (unpublished) Secure Transactions Using Mobile Devices filed Jul. 14, 2014. cited by applicant . Prakash et al., U.S. Appl. No. 62/037,033 (unpublished), Sharing Payment Token filed Aug. 13, 2014. cited by applicant . Hoverson et al., U.S. Appl. No. 62/038,174 (unpublished), Customized Payment Gateway filed Aug. 15, 2014. cited by applicant . Wang, U.S. Appl. No. 62/042,050 (unpublished), Payment Device Authentication and Authorization System filed Aug. 26, 2014. cited by applicant . Gaddam et al., U.S. Appl. No. 62/053,736 (unpublished), Completing Transactions Without a User Payment Device filed Sep. 22, 2014. cited by applicant . Patterson, U.S. Appl. No. 62/054,346 (unpublished), Mirrored Token Vault filed Sep. 23, 2014. cited by applicant . Dimmick, U.S. Appl. No. 14/952,514 (unpublished), Systems Communications With Non-Sensitive Identifiers filed Nov. 25, 2015. cited by applicant . Dimmick, U.S. Appl. No. 14/952,444 (unpublished), Tokenization Request Via Access Device filed Nov. 25, 2015. cited by applicant . Prakash et al., U.S. Appl. No. 14/955,716 (unpublished), Provisioning Platform for Machine-To-Machine Devices filed Dec. 1, 2015. cited by applicant . Wong et al., U.S. Appl. No. 14/966,948 (unpublished), Automated Access Data Provisioning filed Dec. 11, 2015. cited by applicant . Stubbs et al., U.S. Appl. No. 62/103,522 (unpublished), Methods and Systems for Wallet Provider Provisioning filed Jan. 14, 2015. cited by applicant . McGuire, U.S. Appl. No. 14/600,523 (unpublished), Secure Payment Processing Using Authorization Request filed Jan. 20, 2015. cited by applicant . Flurscheim et al., U.S. Appl. No. 15/004,705 (unpublished), Cloud-Based Transactions With Magnetic Secure Transmission filed Jan. 22, 2016. cited by applicant . Flurscheim et al., U.S. Appl. No. 62/108,403 (unpublished), Wearables With NFC HCE filed Jan. 27, 2015. cited by applicant . Sabba et al., U.S. Appl. No. 15/011,366 (unpublished), Token Check Offline filed Jan. 29, 2016. cited by applicant . Patterson, U.S. Appl. No. 15/019,157 (unpublished), Token Processing Utilizing Multiple Authorizations filed Feb. 9, 2016. cited by applicant . Cash et al., U.S. Appl. No. 15/041,495 (unpublished), Peer Forward Authorization of Digital Requests filed Feb. 11, 2016. cited by applicant . Le Saint et al., , U.S. Appl. No. 15/008,388 (unpublished), Methods for Secure Credential Provisioning filed Jan. 27, 2016. cited by applicant . Kinagi, U.S. Appl. No. 62/117,291 (unpublished), Token and Cryptogram Using Transaction Specific Information filed Feb. 17, 2015. cited by applicant . Galland et al. U.S. Appl. No. 62/128,709 (unpublished), Tokenizing Transaction Amounts filed Mar. 5, 2015. cited by applicant . Rangarajan et al., U.S. Appl. No. 61/751,763 (unpublished), Payments Bridge filed Jan. 11, 2013. cited by applicant . Li, U.S. Appl. No. 61/894,749 (unpublished), Methods and Systems for Authentication and Issuance of Tokens in a Secure Environment filed Oct. 23, 2013. cited by applicant . Aissi et al., U.S. Appl. No. 61/738,832 (unpublished), Management of Sensitive Data filed Dec. 18, 2012. cited by applicant . Wong et al., U.S. Appl. No. 61/879,362 (unpublished), Systems and Methods for Managing Mobile Cardholder Verification Methods filed Sep. 18, 2013. cited by applicant . Powell, U.S. Appl. No. 61/892,407 (unpublished), Issuer Over-The-Air Update Method and System filed Oct. 17, 2013. cited by applicant . Powell, U.S. Appl. No. 61/926,236 (unpublished), Methods and Systems for Provisioning Mobile Devices With Payment Credentials and Payment Token Identifiers filed Jan. 10, 2014. cited by applicant . International Search Report dated Apr. 1, 2014 in PCT/IB2013/060696, 3 pages. cited by applicant . Chipman, et al., U.S. Appl. No. 15/265,282 (Unpublished), Self-Cleaning Token Vault, filed Sep. 14, 2016. cited by applicant . Lopez, et al., U.S. Appl. No. 15/462,658 (Unpublished), Replacing Token on a Multi-Token User Device, filed Mar. 17, 2017. cited by applicant. |
Primary Examiner: Chang; Edward
Assistant Examiner: Smith; Slade E
Attorney, Agent or Firm: Kilpatrick Townsend & Stockton LLP
Claims
What is claimed is:
1. A method for providing financial details from a mobile device of a user for use in a transaction, the method being performed on the mobile device of the user and including the steps of: generating, on a token generating component associated with the mobile device, a session-specific token by applying an algorithm stored on the token generating component with a dynamic key, the session-specific token generated by encrypting a customer identification number using the dynamic key and a seed value unique to the user; retrieving, by the mobile device, financial details in a pre-determined format conforming to Track 2 data format for use in a transaction; incorporating the session-specific token and the financial details into a modified form of the financial details including encrypting a portion of characters of the financial details using the session-specific token by incorporating a first portion of the session-specific token before a check digit of the financial details, incorporating a second portion of the session-specific token before a CVV field of the financial details, and replacing data in an account number field with the customer identification number; and transferring the modified form of the financial details in the predetermined format from the mobile device to an issuing authority to initiate the transaction, the issuing authority validating the session-specific token within the modified form of the financial details before authorizing the transaction.
2. The method as claimed in claim 1, wherein incorporating the session-specific token and the financial details into a modified form of the financial details includes: inserting the session-specific token into redundant characters in the pre-determined format.
3. The method as claimed in claim 1, wherein the seed value unique to the user is provided by the issuing authority to the mobile device.
4. The method as claimed in claim 1, wherein the seed value unique to the user is used by the issuing authority to generate an expected session-specific token, the expected session-specific token being compared to the session-specific token when validating the session-specific token.
5. The method as claimed in claim 1, wherein the session-specific token offline from an is generated while not in communication with the issuing authority and the dynamic key is coordinated between the mobile device and the issuing authority.
6. The method as claimed in claim 5, wherein the dynamic key and one of a customer identifier or an initialization vector for a customer is used by an issuing authority to generate an expected-session-specific token to be compared to the session-specific token to authenticate the user.
7. The method as claimed in claim 1, wherein the financial details include static customer account details or one-time generated customer account details.
8. The method as claimed in claim 1, wherein the dynamic key is randomly selected from a pre-calculated set of keys; and a key serial number related to the dynamic key is transferred along with the modified form of the financial details, wherein the key serial number is able to be used to determine the dynamic key that was used.
9. The method as claimed in claim 1, wherein the dynamic key is a counter value which increments or changes every time the algorithm is applied.
10. The method as claimed in claim 1, wherein the dynamic key is based on a time signal derived by the mobile device, the time signal indicating a time at which the generation of the session-specific token is carried out.
11. The method as claimed in claim 1, wherein the token generating component is a cryptographic expansion device that can be attached to a communication component of the mobile device; and the cryptographic expansion device is configured to be used with the mobile device without requiring any changes to the internal software or hardware of the mobile device and without requiring any modification to the communication protocols used by the mobile device.
12. The method as claimed in claim 1, wherein the token generating component is a hardware security module which uses hardware to generate the session-specific token.
13. The method as claimed in claim 1, wherein validating the session-specific token by the issuing authority comprises: identifying, by the issuing authority, the seed value unique to the user based on the customer identification number; determining a lifetime of the session-specific token; generating a plurality of expected session-specific tokens based on the lifetime of the session-specific token; and comparing the session-specific token to each of the expected session-specific tokens of the plurality of expected session-specific tokens, the session-specific token being validated upon determining that the session-specific token matches one expected session-specific token of the plurality of expected session-specific tokens.
14. The method as claimed in claim 13, wherein the lifetime of the session-specific token is ten minutes and the plurality of expected session-specific tokens comprises ten expected session-specific tokens, wherein each of the plurality of expected session-specific tokens is generated to correspond to a one-minute interval of the lifetime.
15. The method as claimed in claim 1, wherein the session-specific token comprises six digits, the first portion of the session-specific token comprises a first three digits of the session-specific token, and the second portion of the session-specific token comprises a last three digits of the session-specific token.
16. A system for providing financial details from a mobile device of a user for use in a transaction, the system being provided on the mobile device of the user and including: a token generating component associated with the mobile device for generating a session-specific token by applying an algorithm stored on the token generating component with a dynamic key, the session-specific token generated by encrypting a customer identification number using the dynamic key and a seed value unique to the user; a financial details component for providing financial details in a pre-determined format conforming to Track 2 data format for use in a transaction; a format modifying component for incorporating the session-specific token and the financial details into a modified form of the financial details including encrypting a portion of characters of the financial details with the session-specific token by incorporating a first portion of the session-specific token before a check digit of the financial details, incorporating a second portion of the session-specific token before a CVV field of the financial details, and replacing data in an account number field with the customer identification number; and a communication component for transferring the modified form of the financial details in the pre-determined format from the mobile device to an issuing authority to initiate the transaction, the issuing authority being caused to validate the session-specific token within the modified form of the financial details before authorizing the transaction.
17. The system as claimed in claim 16, wherein the token generating component is a cryptographic expansion device that can be attached to a communication component of the mobile device; and the cryptographic expansion device is configured to be used with the mobile device without requiring any changes to the internal software or hardware of the mobile device and without requiring any modification to the communication protocols used by the mobile device.
18. The system as claimed in claim 17, wherein the cryptographic expansion device is a cryptographic label that includes a hardware security module (HSM) disposed therein including a secure processing unit and a public processing unit.
19. The system as claimed in claim 16, wherein the token generating component is a hardware security module which uses hardware to generate the session-specific token.
20. A computer program product for providing financial details from a mobile device of a user for use in a transaction, the computer program product comprising a computer-readable medium having stored computer-readable program code for performing the steps of: generating, on a token generating component associated with the mobile device, a session-specific token by applying an algorithm stored on the token generating component with a dynamic key, the session-specific token generated by encrypting a customer identification number using the dynamic key and a seed value unique to the user; providing financial details in a pre-determined format conforming to Track 2 data format for use in a transaction; incorporating the session-specific token and the financial details into a modified form of the financial details including encrypting a portion of characters of the financial details with the session-specific token by incorporating a first portion of the session-specific token before a check digit of the financial details, incorporating a second portion of the session-specific token before a CVV field of the financial details, and replacing data in an account number field with the customer identification number; and transferring the modified form of the financial details in the predetermined format from the mobile device to an issuing authority to initiate the transaction, the issuing authority validating the session-specific token within the modified form of the financial details before authorizing the transaction.
Description
CROSS-REFERENCES TO RELATED APPLICATIONS
This application is a National Stage of International Application No. PCT/IB2013/060696, International Filing Date Dec. 6, 2013, and which claims the benefit of South African Patent Application No. 2012/09284, filed Dec. 7, 2012, the disclosures of both applications being incorporated herein by reference.
BACKGROUND
This invention relates to a device, system and method for generating tokens for security purposes.
Many applications utilize token generation to enhance security through the provision of session specific tokens. Token generators often require a user to carry hardware with them, such as key fobs, cards, or USB devices, which are required for the generation of the session specific token. Carrying such devices may be inconvenient to a user.
The abovementioned hardware-type token generators often use time-based encryption, wherein the current time upon generation of a session-specific token is used as an input value to the algorithm used. The use of a time as an input value is an example of dynamic key use, where a continuously changing (dynamic) key is used as an input value to the algorithm used for determining the session specific token. A dynamic key ensures that the algorithm will provide a different result each time that the result of the algorithm is determined. If the same input value is used more than once in a token generating device which utilizes a single algorithm, the same result will be obtained. By including a dynamic input value, a different result should be obtained after each calculation.
A major problem which is often encountered with hardware-type token generators which use time as an input value is that the clock which provides the time to the hardware has to be synchronized with the clock of a service provider who has to check the validity of a generated token. Should the clocks not be synchronized, a validly generated token may not be recognized as valid when it is checked by a service provider with a clock that is out-of-sync to the clock of the hardware.
Mobile banking involves the use of a mobile device to pay for goods or services at a point-of-sale (POS) of a merchant, or even remotely. Mobile payments, in turn, refer to payment services performed with the use of a mobile device. Examples of mobile payments include situations in which details of a person's financial transaction card, such as a debit or credit card, is stored on the person's mobile device, typically in the format of Track 1 or Track 2 card data. Track 1 and Track 2 are standardized formats in which properties of a financial transaction card are stored on the cards themselves.
The mobile device transfers the details of a person's financial transaction card to a POS terminal of a merchant where a user wishes to transact, for example by means of near-field communications technology. The POS terminal, in turn, transmits the details to an issuing authority that is to approve or deny payment from an account of the user held by the issuing authority. Security concerns do however still exist with regards to mobile payments, for example regarding the possibility of the interception of the details during its transfer, or the access protection offered by the mobile device with regards to the payments cards stored thereon.
BRIEF SUMMARY
In accordance with an embodiment of the invention there is provided a method for providing financial details from a mobile device of a user for use in a transaction, the method being performed on a mobile device of the user and including the steps of:
generating, on a token generating component associated with the mobile device, a session-specific token by applying an algorithm stored on the token generating component with a dynamic key;
providing financial details in a pre-determined format for use in a transaction;
incorporating the session-specific token and the financial details into a modified form of the financial details; and
transferring the modified form of the financial details in the pre-determined format from the mobile device to initiate the transaction.
Further features of the invention provide for the step of incorporating the session-specific token and the financial details into a modified form of the financial details to include inserting the session-specific token into redundant characters in the pre-determined format; and to include encrypting a portion of the characters of the financial details with the session-specific token.
Still further features of the invention provide for the algorithm stored on the token generating component to include an individual seed value for a customer; and for the modified form of the financial details to include a readable customer identifier.
Yet further features of the invention provide for the algorithm stored on the token generating component to include a seed value for an issuing authority; and for the modified form of the financial details to include a readable issuing authority identifier and an initiation vector.
In one embodiment of the invention, the dynamic key acts as the seed value. In a further embodiment, the user has a unique seed value, and the issuing authority has a database storing details relating to customer's respective unique seed values.
Further features of the invention provide for the step of generating, on a token generating component associated with the mobile device, a session-specific token by applying an algorithm stored on the token generating component with a dynamic key, generates the session-specific token offline from an issuing authority and the dynamic key is coordinated between the mobile device and the issuing authority.
A still further feature of the invention provides for the session-specific token to be generated without a communication channel to a issuing authority that is to verify the validity of the token, the issuing authority able to determine the session-specific token used, and its validity.
A yet further feature of the invention provides for the dynamic key and one of a customer identifier or an initialization vector for a customer to enable the session-specific token to be reversed by an issuing authority to authenticate a customer.
A further feature of the invention provides for the financial details to include static customer account details or one-time generated customer account details.
Still further features of the invention provide for the dynamic key to be randomly selected from a pre-calculated set of keys; and for a key serial number related to the dynamic key to be transferred along with the modified form of the financial details, wherein the key serial number is able to determine the dynamic key that was used.
Yet further features of the invention provide for the dynamic key to be a counter value which increments or changes every time the algorithm is applied; or to be a based on a time signal derived by the mobile device and at which the generation of the session-specific token is carried out.
Still further features of the invention provide for the session-specific token to be inserted in redundant characters in the pre-determined format; for the format to be compatible with a POS terminal; for the format to be the Track 1 or Track 2 data format of a financial transaction card; and for the session-specific token to be inserted at least partially in any one or more of a field normally reserved for an expiration date, a card security code, a service code, discretionary data, or a name. In one embodiment of the invention, the token is inserted into the card security code only, and the card security code can be described as a dynamic card security code.
In one embodiment of the invention, the financial details are transferred to a point-of-sale (POS) terminal of a merchant, from where it is further transferred to the issuing authority.
Further features of the invention provide for the token generating component to be a cryptographic expansion device that can be attached to a communication component of the mobile device; and for the cryptographic expansion device to be configured to be used with the mobile device without requiring any changes to the internal software or hardware of the mobile device and without requiring any modification to the communication protocols used by the mobile device.
The invention further extends to the cryptographic expansion device being a cryptographic label that includes a hardware security module (HSM) disposed therein including a secure processing unit and a public processing unit.
In one embodiment of the invention, the cryptographic label also includes a first set of electrical contacts disposed on the top side of the cryptographic label for interfacing to a mobile device, and a second set of electrical contacts disposed on the bottom side of the cryptographic label for interfacing to a communication component. A coupling element may also be provided to attach the cryptographic label to the communication component. In an exemplary embodiment, the mobile device can be a mobile phone, the communication component can be a subscriber identity module (SIM) card, and the coupling element used for attaching the cryptographic label to the communication component can be an adhesive material disposed on the cryptographic label.
The invention extends to a method for determining the validity of financial details, the method being performed at a server and including the steps of:
receiving a pre-determined format of financial details for a transaction;
extracting a session-specific token from the pre-determined format;
generating, on a token generating component associated with the server, at least one expected session-specific token by applying an algorithm with a dynamic key;
comparing the at least one expected session-specific token and the extracted session-specific token; and
in response to the extracted session-specific token matching at least one expected session-specific token, approving the received financial details for use; or,
in response to the extracted session-specific token matching none of the at least one expected session-specific tokens, rejecting the financial details for use.
A further feature of the invention provides for the step of extracting the session-specific token from the pre-determined format to include extracting the session-specific token from redundant characters in the pre-determined format.
Still further features of the invention provide for the algorithm stored on the token generating component to include an individual seed value for a customer; and for the received pre-determined format of financial details to include a readable customer identifier.
Yet further features of the invention provide for the algorithm stored on the token generating component to include a seed value for an issuing authority; and for the received pre-determined format of financial details to include a readable issuing authority identifier and an initialization vector.
Further features of the invention provide for the financial details to include static customer account details or one-time generated customer account details. In one embodiment, the pre-determined format may be a Track 1 or Track 2 data format of a financial transaction card.
Still further features of the invention provides for the financial details to include a serial number related to the dynamic key, the serial number providing an indication of the dynamic key used; the server having a database associated therewith which stores a list of keys and related serial numbers.
Yet further features of the invention provides for the server to be a server of an issuing authority at which a user has an account; and for financial details to be received from the mobile device of a user or a POS terminal of a merchant.
Further features of the invention provide for an expected session-specific token to be any token which may have been validly generated within a pre-determined amount of time; or to be any token which may have been validly generated a pre-determined amount of times since a previous transaction approval message has been transmitted.
A still further feature of the invention provides for the method to include the step of transmitting a transaction approval or a transaction rejection message to an electronic device of either the user or the merchant in response to the approval or rejection of the financial details for use.
The invention extends to a system for providing financial details from a mobile device of a user for use in a transaction, the system being provided on a mobile device of the user and including:
a token generating component associated with the mobile device for generating a session-specific token by applying an algorithm stored on the token generating component with a dynamic key;
a financial details component for providing financial details in a pre-determined format for use in a transaction
a format modifying component for incorporating the session-specific token and the financial details into a modified form of the financial details; and
a communication component for transferring the modified form of the financial details in the pre-determined format from the mobile device to initiate the transaction.
Further features of the invention provide for the format modifying component to incorporate the session-specific token and the financial details into a modified form of the financial details by inserting the session-specific token into redundant characters in the pre-determined format; or by encrypting a portion of the characters of the financial details with the session-specific token.
In one embodiment of the invention, the algorithm stored on the token generating component may include an individual seed value for a customer; and wherein the modified form of the financial details may include a readable customer identifier. In another embodiment, the algorithm stored on the token generating component may include a seed value for an issuing authority; and wherein the modified form of the financial details may include a readable issuing authority identifier and an initialization vector.
In one embodiment of the invention, the modified form of the financial details is transferred to a point-of-sale (POS) terminal of a merchant, from where it is further transferred to the issuing authority.
The invention extends to a mobile device having a hardware security module having a memory component for storing at least an algorithm, a seed value and a pre-determined format; and the token generating component applying the algorithm with input values including at least the seed value and a dynamic key.
Further features of the invention provide for the token generating component to be a cryptographic expansion device that can be attached to a communication component of the mobile device; and for the cryptographic expansion device to be configured to be used with the mobile device without requiring any changes to the internal software or hardware of the mobile device and without requiring any modification to the communication protocols used by the mobile device.
A still further feature of the invention provide for the cryptographic expansion device to be a cryptographic label that includes a hardware security module (HSM) disposed therein including a secure processing unit and a public processing unit.
In one embodiment of the invention, the cryptographic label also includes a first set of electrical contacts disposed on the top side of the cryptographic label for interfacing to a mobile device, and a second set of electrical contacts disposed on the bottom side of the cryptographic label for interfacing to a communication component. A coupling element may also be provided to attach the cryptographic label to the communication component. In an exemplary embodiment, the mobile device can be a mobile phone, the communication component can be a subscriber identity module (SIM) card, and the coupling element used for attaching the cryptographic label to the communication component can be an adhesive material disposed on the cryptographic label.
The invention extends to a system for determining the validity of financial details, the system being provided at a server and including:
a receiving component for receiving a pre-determined format of financial details for a transaction;
an extracting component for extracting a session-specific token from the pre-determined format;
a token generating component associated with the server for generating at least one expected session-specific token by applying an algorithm with a dynamic key;
a comparing component for comparing the at least one expected session-specific token and the extracted session-specific token; and
in response to the extracted session-specific token matching at least one expected session-specific token, approving the received financial details for use; or,
in response to the extracted session-specific token matching none of the at least one expected session-specific tokens, rejecting the financial details for use.
Further features of the invention provides for the server to be a server of an issuing authority at which a user has an account; and for financial details to be received from a POS terminal of a merchant.
A yet further feature of the invention provides for the system to include a transmission component for transmitting a transaction approval or a transaction rejection message to an electronic device of either the user or the merchant in response to the approval or rejection of the financial details for use.
The invention extends to a computer program product for providing financial details from a mobile device of a user for use in a transaction, the computer program product comprising a computer-readable medium having stored computer-readable program code for performing the steps of:
generating, on a token generating component associated with the mobile device, a session-specific token by applying an algorithm stored on the token generating component with a dynamic key;
providing financial details in a pre-determined format for use in a transaction;
incorporating the session-specific token and the financial details into a modified form of the financial details; and
transferring the modified form of the financial details in the pre-determined format from the mobile device to initiate the transaction.
The invention further extends to a computer program product for determining the validity of financial details, the computer program product comprising a computer-readable medium having stored computer-readable program code for performing the steps of:
receiving a pre-determined format of financial details for a transaction;
extracting a session-specific token from the pre-determined format;
generating, on a token generating component associated with the server, at least one expected session-specific token by applying an algorithm with a dynamic key;
comparing the at least one expected session-specific token and the extracted session-specific token; and
in response to the extracted session-specific token matching at least one expected session-specific token, approving the received financial details for use; or,
in response to the extracted session-specific token matching none of the at least one expected session-specific tokens, rejecting the financial details for use.
BRIEF DESCRIPTION OF THE DRAWINGS
FIG. 1 is a system for providing financial details from a mobile device in accordance with an embodiment of the present invention;
FIG. 2 is an embodiment of a mobile device of the system of FIG. 1 in accordance with the present invention;
FIG. 3 a flow diagram of an embodiment of a method of operation of the system of FIG. 1;
FIG. 4 is an example of a financial detail structure used in the method of FIG. 3;
FIG. 5 is a flow diagram of an embodiment of a method performed on the mobile device of FIG. 2 in accordance with the present invention;
FIG. 6 is an embodiment of a server of the system of FIG. 1 in accordance with the present invention;
FIG. 7 is a flow diagram of an embodiment of a method in accordance with the present invention performed on the server of FIG. 6;
FIG. 8 is an embodiment of a system for providing financial details from a mobile device in accordance with a further embodiment of the invention;
FIG. 9 is a flow diagram of an embodiment of a method in accordance with the present invention performed at the server of the system of FIG. 8;
FIG. 10 is a second example of a financial detail structure used in a method of operation of the mobile device of FIG. 2;
FIG. 11 is a flow diagram of an embodiment of a method in accordance with the present invention performed on the mobile device of FIG. 2 and using the financial detail structure of FIG. 10;
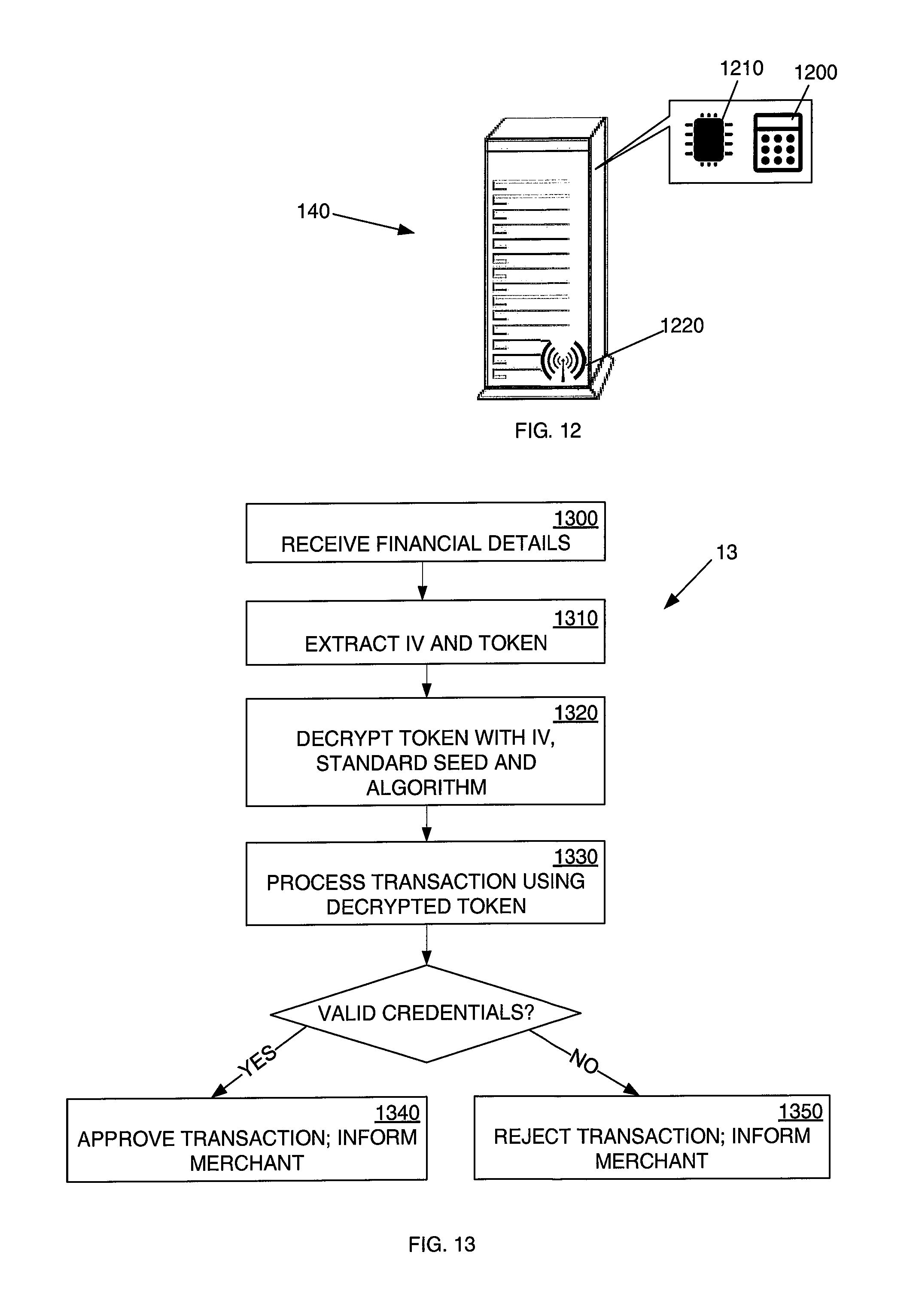
FIG. 12 is an embodiment of a server of the system of FIG. 1 in accordance with the present invention;
FIG. 13 is a flow diagram of an embodiment of a method in accordance with the present invention performed at the server of FIG. 12;
FIG. 14 is an embodiment of a computing device in accordance with the present invention; and
FIG. 15 is an embodiment of a block diagram of a communication device in accordance with the present invention.
DETAILED DESCRIPTION
FIG. 1 shows a system (1) for providing financial details from a mobile device. The system includes a mobile device (100) of a user (110), a point of sale terminal (120) of a merchant, and an issuing authority (130) at which the user (110) has an account. The issuing authority has associated therewith a server (140) and a database (150). In the present embodiment, the mobile device (100) is a smartphone, however the mobile device (100) may alternatively be a feature phone.
The mobile device (100) of FIG. 1 is shown in more detail in FIG. 2. The mobile device includes an encryption component, in the present embodiment a hardware security module (HSM) (200). The HSM includes a token generating component (210), a financial details component, in the present embodiment a non-volatile memory module (220), and a format modifying component, in the present embodiment a processor (230). The mobile device also has a communication component (240) by means of which it can receive and send data.
In at least one embodiment of the invention, the mobile device differs from devices that may solely use software to encrypt communications between an electronic device and a target device or system. An electronic device that solely uses software to encrypt communications may comply with only a security level 1 of the Federal Information Processing Standard 140-2 (FIPS 140-2), which provides only a minimum level of security to protect sensitive information. In contrast, the HSM within an electronic device or controller according to some embodiments of the invention is compliant with at least a security level 2 of the FIPS 140-2 standard. More preferably, the HSM within the electronic device or controller in embodiments of the invention is compliant with security level 3 or level 4 of FIPS 140-2.
The HSM in embodiments of the invention uses hardware to encrypt data instead of solely performing the encryption in software. The HSM provides enhanced protection over software encryption technologies. For example, the HSM provides secure key management to generate cryptographic keys, sets the capabilities and security limits of keys, implements key backup and recovery, prepares keys for storage and performs key revocation and destruction. In some embodiments, the HSM is implemented as a dual processor device that includes a secure processor with storage and a public processor with storage. The HSM may also include a physical or logical separation between interfaces that are used to communicate critical security parameters and other interfaces that are used to communicate other data. The HSM can also provide a tamper-proof mechanism that provides a high risk of destroying the HSM and the cryptographic keys stored therein, if any attempt is made to remove or externally access the HSM.
FIG. 3 shows a flow diagram of an example operation of the system of FIG. 1. When a user (110) wishes to transact with a merchant, the user indicates on an input component of the mobile device (100), typically a keyboard, that he or she wishes to generate financial details required to complete the transaction in a first step (301). The financial details are generated on the mobile device (100) of the user (110) in a next step (302), and are transmitted to the POS terminal (120) in a further step (303). From the POS terminal (120), the details are transmitted to the issuing authority (130) at which the user has an account in a next step (304). At the issuing authority (130), the validity of the financial details is verified in a next step (305). Finally, the merchant is informed of the result of the verification of the details in a final step (306).
The financial details are presented in a format compliant with POS devices. In the present embodiment of the invention, that format is Track 2 financial transaction card format. By using a data format that a point of sale device is used to handling, the least number of modifications need to be made to currently in-use POS terminals and transmission protocols to allow them to facilitate the operation of the invention.
Track 2 financial transaction card data include a number of digits in a pre-determined format. An example of data included in Track 2 data is shown in FIG. 4. The data includes a personal account number (PAN) field (400), which is made up of a bank identification number (BIN) field (401) of 6 characters and an account number field (402) of the user, of 10 characters. A BIN is an identifier of an institution who issued the financial data, such as an issuing authority, or of an issuing authority at which a user has an account. The account number includes a check digit (403) of a single character. Also included in the Track 2 data is an expiry date field (404) of 4 characters and a card verification value (CVV) field (405) of 3 characters. It should be noted that FIG. 4 only shows an extract of the data fields in Track 2 data, and that the actual format includes various other fields, such as field separators, and initialization fields, a termination field, as well as other data fields.
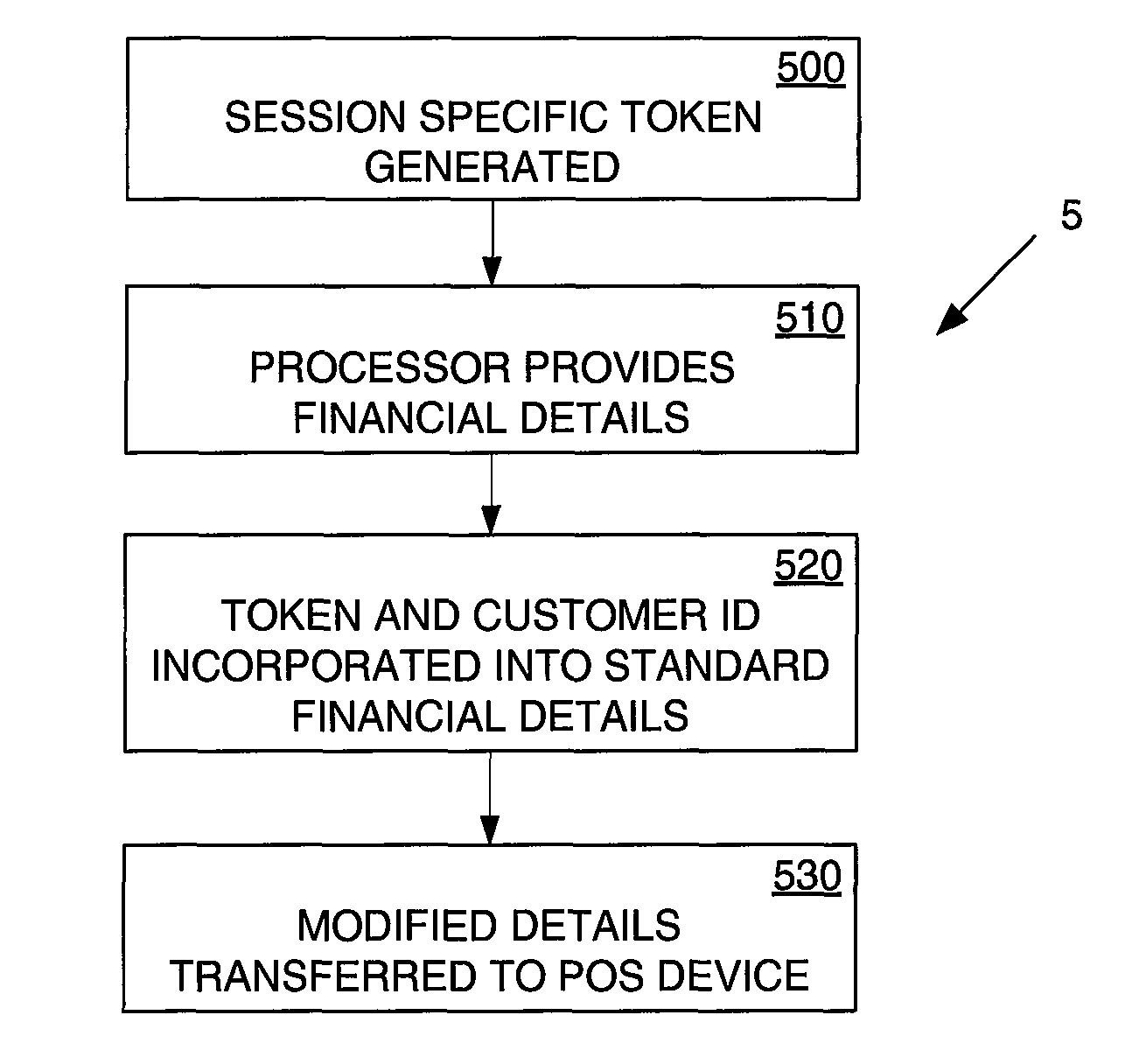
A method performed on the mobile device for providing financial details is illustrated in the flow diagram (5) shown in FIG. 5. The method is performed on a mobile device as illustrated in FIG. 2 and the reference numerals for the components of FIG. 2 are used.
In a first step (500), a session specific token is generated on the token generating component (210) of the mobile device. It is envisaged that the mobile device will only generate a session-specific token upon a request from the user to do so.
To generate the token, the token generating device uses an algorithm which is stored on the token generating component (210) in the HSM (200). The algorithm requires a seed value as input, the seed being unique to the user (110). The seed value is stored in the memory module (220). The algorithm further requires a dynamic key as an input value. In the present embodiment, the dynamic key used is a counter value which is also stored on the memory module. After each determination of a session-specific token using the algorithm and dynamic key, the counter is increased. The initial counter value and the seed value of a user are known by the issuing authority (130).
In a next step (510), the processor (230) provides financial details relating to a payment card of the user, in the present embodiment payment card details in the form of Track 2 data may be stored in the memory module (210).
In a next step (520), the session specific token is incorporated into data fields of the Track 2 data which is available for a part of the account number and the CVV and, optionally, the expiry date. In the present embodiment, these fields are not essential for the transfer of payment credentials, and may be considered redundant. In the present embodiment, three characters of the session-specific token are incorporated in a last part (407), before the check digit (403), of the account number field (402), and three characters are incorporated in the CVV field (405).
A first part (406) of the account number field (402) is used to transmit the customer ID number, which is stored in and retrieved from the memory module (220). In combination, the last part (407) of the account number field and the CVV field (405) provide space for a 6-digit token to be inserted. The result of the incorporated of the session-specific token and the customer ID number into the Track 2 data is a modified form of the financial details.
In a final step (530), the modified form of the financial details is transferred to a POS terminal that is still in a format compatible with the POS terminal. In effect, certain numeric characters in the Track 2 data have been altered.
The point of sale device transmits the modified form of the financial details received to the issuing authority (130) in a similar manner as is currently known for transactions involving a physical payment card. The modified form of the financial details is sent along with details of the transaction, including, for example, the price payable and a merchant identifier, as is common practice in payment systems using POS terminals. The BIN number (401) indicates to the POS terminal to which issuing authority the details are to be sent.
An embodiment of the server (140) of FIG. 1 is shown in more detail in FIG. 6. The server (140) includes a token generating component (610), an extraction component, and a comparison component. In the present embodiment, the extraction component and the comparison component are provided by a processor (620). The server also has a communication component (630) by means of which data can be sent and received. The communications component functions as both a receiving component and a transmission component, for receiving and transmitting data.
A flow diagram (7) illustrating the method followed by the server (140) of a issuing authority in determining the validity of received financial details in accordance with an embodiment of the invention is illustrated in FIG. 7. In a first step (700), the issuing authority receives financial details in an expected format. In the present embodiment, the expected format is a modified form of the Track 2 data as described above.
Since a customer ID number is contained in the first part (407) of the account number field (402) in an unaltered form, the server can extract the customer ID number directly from the details received in a next step (710). Since the fields in which a session-specific token should be included are also known to the issuing authority, a token is also extracted by the server in this step (710) from the last part (406) of the account number field (402) and the CVV field (405).
The database (150) has stored thereon a list containing the details of user accounts, including the customer ID number of each user account and the counter value and seed value associated with each user account. The counter value and seed are retrieved by the server in a next step (720), by looking up the key and seed associated with the customer ID number extracted from the financial details received in the previous step (710).
In a next step (730), the server applies an algorithm related to the algorithm that is stored on the memory module (220) of the HSM (200) on the user's mobile device (100), using the seed value and counter value retrieved from the database (150), to obtain an expected session-specific token. The server utilizes its token-generating component (710) for calculating expected session-specific tokens.
The server then compares the expected session-specific token to the received token in a next step (740). If the tokens match, the transaction is approved, and an approval message is transmitted to the merchant in a final step (750) via the communication component (730). If the tokens do not match, the transaction is rejected, and a rejection or failure message is transmitted to the merchant in a final step (760) via the communication component (730). If the transaction is approved, the server is expected to deal with the transfer of money in a standard manner. After a successful comparison, the counter value stored in the database relating to the user account concerned is increased in the same manner as it would have occurred on the user's mobile device when then session-specific key was originally generated. The approval or rejection message may also be sent to the user's mobile device.
It is envisaged that the seed value may constitute the dynamic key itself. In such a situation, only the dynamic key will be used as input value for generating a session-specific token, and the server will only need to look up the dynamic key to generate the same token instead of looking up the dynamic key and the seed value.
It should be noted that in the embodiment described above, the session-specific token is generated without a direct communication channel to the issuing authority. Therefore, the token generation can be considered as offline token generation, wherein the validity of the token can be assessed by the issuing authority at a later stage.
In another embodiment of the invention, both the HSM and the database have a set of pre-calculated keys which can be used to generate a session-specific token. In such an embodiment, a section of the Track 2 data field can be used to indicate which of these keys have been used by the token generating component to generate the specific token, in effect by using a key serial number. For example, if there are ten different tokens, a single digit, with numerals 0 to 9, can be used to indicate which of the keys have been used in the encryption process. It should be noted that this digit must not be encrypted in the modified form of the financial details if it is transmitted as part of the modified form of the payment credentials. The server can then look up the key used in the database, using the serial number of the key received. Alternatively, the key used can be based on a counter value, and the token generating component will use the different keys in a standard format or according to another algorithm, both being determinable by the issuing authority's token generating component by looking the values up in its associated database. A key that changes in this manner can also be described as a dynamic key.
In the embodiment described above, tokens will need to be validated by an issuing authority in the order in which they are generated by the token generating component on the mobile device. If a generated token does not reach the issuing authority, the counter on the mobile device and the counter in the database will be out of sync, and a token generated at the server will not be the same as a token received from the POS terminal. It is envisaged that in at least some embodiments, the server will test the validity by applying a counter increased by, for example, three times' use. In such an embodiment, the server will compensate for a delay in tokens received. The server may be configured to inform the user if the counter values at the mobile device and server are suspected to be out of sync in this manner.
Also in the embodiment described above, the session-specific token has been included in redundant characters of the Track 2 data; however, it is also envisaged that some of the characters may be encrypted, either by means of a one-way hash function, an RSA token, or indeed any cryptographic function that renders a different result upon every operation performed with differing input values. A person skilled in the art would appreciate that there are indeed a large variety of cryptographic functions that can perform such a function.
It is further envisaged that the expiry date field (404) may be used as another field in which characters of the session-specific key may be stored. However, it should be noted that a POS terminal may automatically reject financial details if the details are in an invalid format, or in a format that will constitute a date that has passed, or a date that is too far in the future. Typically, any date more than 4 years in the future will be rejected. Similarly, any month field that is not from 01 to 12 will be invalid, and any day field that is not from 1 to 31 will be invalid. Some POS devices may also reject a day field if the relevant month does not have that many days, for example the second month, February, or 02, cannot have 30 days. Including the expiry date field as a field in which characters of a session-specific token may be stored will increase the possible length of the token, although the specific characters that may be used or which may be used together are limited. Any system which makes use of the expiry date field should be configured to only include acceptable characters in this field.
FIG. 8 shows an embodiment of a system (8) in which the dynamic key is time-based, instead of based on counter value as described above. This may be referred to as "time-based encryption". The system includes a mobile device (800) of a user (810), a point of sale terminal (820) of a merchant, and an issuing authority (830). The financial system has associated therewith a server (840) and a database (850). In the present embodiment, as in the embodiment described with reference to FIG. 1, the mobile device is a smartphone. The mobile device (800) is in communication with a mobile base station which has a clock (870). The database (850) also has a clock (880) which is synchronized with the clock (870) of the base station.
Modern smartphones, and indeed the mobile device (800) of the present embodiment, are able to retrieve the current time from a clock at a mobile base station. Accordingly, upon the device being requested to generate a session-specific token, the mobile device (800) obtains the time from the clock (870) of the base station (860). At least a part of this time is used as a dynamic key for an input value in the algorithm, negating the need for a counter value as dynamic key. In the present embodiment, the hours and minutes of the current time is used as an input value. The session-specific token obtained from application of the algorithm is then handled in exactly the same way as described above, in that the token replaces some of the characters in financial details in a standard format that is stored on the HSM, and the modified financial detail is transferred to a POS terminal. Similarly, a customer ID number is included in the modified format as well. The modified financial details format is identical to the format described with reference to FIG. 4. The POS terminal transfers the modified financial details to the issuing authority as described above.
A method of determining the validity of the credentials received by the server (940) in accordance with the present embodiment of a time-based dynamic key is illustrated by the flow diagram (9) shown in FIG. 9. In a first step (900), the issuing authority receives financial details in an expected format. In the present embodiment, the expected format is a modified form of the Track 2 data as described above. The inclusion of the BIN in the modified form of the Track 2 data in an unaltered, standard format allowed the POS terminal (820) to transmit the data to an appropriate issuing authority (830).
Since a customer ID number is contained in the first part (407) of the account number field (402) in an unaltered form, the server can extract the customer ID number directly from the details received in a next step (910). Since the fields in which a session-specific token should be included are also known to the issuing authority, a token is also extracted by the server in this step (910) from the last part (406) of the account number field (402) and the CVV field (405).
The database (750) has stored thereon a list containing the details of user accounts held at the issuing authority, including the customer ID number of each user account and the counter value associated with each user account. The seed value is retrieved by the server in a next step (920), by looking up the seed associated with the customer ID number extracted from the financial details received in the previous step (900).
In a next step (930), the server applies an algorithm related to the algorithm that is stored on the memory module (220) of the HSM (200) on the user's mobile device (100), using the seed value retrieved. The server has a token-generating component associated therewith which is similar to the token-generating component (210) of the HSM (200) for calculating expected session-specific tokens. The server also uses the time of its clock (780), which is synchronized with the clock (770) of the mobile base station (760), as input value, in order to obtain an expected session-specific token. As with the generation of the original session-specific token, the hours and minutes of the current time is used. In the present embodiment, the lifetime of a session-specific key is ten minutes, and the server also generates expected tokens for the previous ten minutes. As only the current hour and minutes are used as input values, and not the seconds, ten expected tokens need to be determined for a session-specific token lifetime of ten minutes.
The server then compares the ten expected session-specific tokens to the received token in a next step (940). If the received token matches any of the expected tokens, the transaction is approved, and an approval message is transmitted to the merchant in a final step (950). If none of the expected tokens match the received token, the transaction is rejected, and a rejection or failure message is transmitted to the merchant in a final step (960). If the transaction is approved, the server is expected to deal with the transfer of money in a standard manner. It should be noted that since there is no counter value present, no alterations need to be made to the database after successful completion of a transaction.
Although it has only be described that the hour and minutes are used as input values for the time-based encryption described above, other elements of time may also be used. For example, the day, month or year of the current time may all be used, or even the seconds, milliseconds, or the like, as input values. It should be noted that the inclusion of these elements may increase the amount of expected session-specific tokens to which a received token need to be compared, depending on the lifetime of a session-specific token. For example, a session-specific token which is valid for 2 minutes and which uses seconds of time as input value to the algorithm, as there are 120 seconds in two minutes.
In FIG. 10, the example of data forming part of Track 2 data as shown in FIG. 4 is repeated. The data includes a personal account number (PAN) field (1000), which is made up of a bank identification number (BIN) field (1010) of 6 characters and an account number field (1020) of the user, of 10 characters. The account number includes a check digit (1030) of a single character. Also included in the Track 2 data is an expiry date field (1040) of 4 characters and a card verification value (CVV) field (1050) of 3 characters. It should be noted that FIG. 10 only shows an extract of the data fields in Track 2 data, and that the actual format includes various other fields, such as field separators, initialization fields, a termination field, as well as other data fields. In the present embodiment, all HSM modules issued by a specific issuing authority have the same algorithm stored thereon. This data is, however, modified differently to the data that was described with reference to FIG. 4. A flow diagram illustrating an alternative method performed on the mobile device of FIG. 2 is shown in FIG. 11. The mobile device forms part of the same system (1) that was described above with reference to FIG. 1.
In a first step (1100), the processor (230) provides financial details relating to a payment card of the user, in the present embodiment again payment card details in the form of Track 2 data may be stored in the memory module (220) of the HSM (200).
In a next step, the token generating component (1110) generates a session-specific token of up to 9 characters long, using an encryption algorithm to encrypt a customer identification number with input values including a seed value and a dynamic key. The algorithm also uses an initialization vector (IV) as input value. In the present embodiment, the IV may be a random one-time CVV value, which is determined by the token generating component (210) prior to generating the session-specific token. The algorithm and seed value is stored on the memory module (220), and are linked to the specific issuing authority which is to approve or reject the transaction. The customer identification number may also be stored on the memory module (220).
In the present embodiment of the invention, every user which has a financial account at a specific issuing authority and who makes use of the system and method of the invention is in possession of the same key and a corresponding decryption algorithm.
The up to 9 characters of the session-specific token is inserted into the account number field (1020) not including the check digit (1030) field, and the random CVV value, which is also the IV, is inserted into the CVV field (1050) in a next step (1120), to arrive at a modified form of the financial details. In a final step (1130), the modified financial details are transmitted to the POS device (120).
The point of sale device transmits the modified form of the financial details received to the issuing authority (130) in a similar manner as is currently known for transactions involving a physical payment card. The modified form of the financial details is sent along with details of the transaction, including the price payable and a merchant identifier, as is currently known. The BIN number indicates to the POS terminal to which issuing authority the details are to be sent.
A further embodiment of the server (140) of FIG. 1 is shown in more detail in FIG. 12. The server includes an extraction component, a comparing component, and a token decryption component (1200). In the present embodiment, the extraction component and the comparing component are provided by a processor (1210). The server also has a communication component (1220) by means of which data can be sent and received. The communications component functions as both a receiving component and a transmission component, for receiving or transmitting data.
A flow diagram (13) illustrating the method followed by the server (140) of an issuing authority in determining the validity of received financial details in accordance with the present embodiment of the invention is illustrated in FIG. 13. In a first step (1300), the issuing authority receives financial details in an expected format via the communication component (1220). In the present embodiment, the expected format is a modified form of the Track 2 data as described above.
Since every modified form of financial details received by an issuing authority is expected to have been encrypted with the same algorithm and seed value, a related same decryption algorithm and seed value can be used by the server to decrypt any received modified financial details.
In a next step (1310), the server extracts the IV from the CVV field and the token from the account number field with the processor (1210). In combination with the standard seed and algorithm, the IV is used to decrypt the token in the account number field, using the decryption component (1200) to extract the customer identification number in a next step (1320).
The transaction is then processed in the normal manner in a next step (1330), using the result of the decryption algorithm. If the credentials obtained using the decryption algorithm is valid, the transaction is approved, and an approval message is transmitted to the relevant merchant in a final step (1340), using the communication component (1220). If the credentials are not valid, the transaction is rejected, and a rejection or denial message is transmitted to the merchant in a final step (1350) using the communication component (1220).
It is envisaged that different algorithms may be stored on a memory module of the HSM, with each algorithm being coupled to a specific issuing authority. By selecting a specific set of financial details to use in a transaction, the HSM will use the appropriate set of details in order to produce a session-specific token with an algorithm that the specific issuing authority can decrypt or interpret.
It should also be noted that the providing of the financial details by the mobile device may be facilitated by a computer program product, such as an application or a program, operating on the mobile device. The computer program product will typically need to be stored in a computer-readable medium in the form of a computer-readable program code, and will be configured to enable the performance of the method on the mobile device as described earlier with reference to FIG. 5 and FIG. 11. Similarly, the determining of the validity of financial details on the server may be facilitated by a computer program product, such as an application or a program, operating on the server. The computer program product will typically need to be stored in a computer-readable medium in the form of a computer-readable program code, and will be configured to enable the performance of the method on the server as described earlier with reference to FIG. 6 and FIG. 12.
In at least one embodiment of the invention, the financial details are not stored on a memory element (220) of the mobile device, and are rather obtained from the issuing authority. These financial details may be one-time use financial details, often referred to as one-time personal account numbers. These one-time use financial details may then be encrypted or modified as explained above. In such an instance, the server may be configured to remember which user has requested the one-time use financial details, and check when receiving financial details that the user from which the details appear to originate has in actual fact request credentials. This may provide additional security to a user wishing to use the systems and methods described.
FIG. 14 illustrates an example of a computing device (1400) in which various aspects of the disclosure may be implemented. The computing device (1400) may be suitable for storing and executing computer program code. The various participants and elements in the previously described system diagrams may use any suitable number of subsystems or components of the computing device (1400) to facilitate the functions described herein.
The computing device (1400) may include subsystems or components interconnected via a communication infrastructure (1405) (for example, a communications bus, a cross-over bar device, or a network). The computing device (1400) may include at least one central processor (1410) and at least one memory component in the form of computer-readable media.
The memory components may include system memory (1415), which may include read only memory (ROM) and random access memory (RAM). A basic input/output system (BIOS) may be stored in ROM. System software may be stored in the system memory (1415) including operating system software.
The memory components may also include secondary memory (1420). The secondary memory (1420) may include a fixed disk (1421), such as a hard disk drive, and, optionally, one or more removable-storage interfaces (1422) for removable-storage components (1423).
The removable-storage interfaces (1422) may be in the form of removable-storage drives (for example, magnetic tape drives, optical disk drives, floppy disk drives, etc.) for corresponding removable storage-components (for example, a magnetic tape, an optical disk, a floppy disk, etc.), which may be written to and read by the removable-storage drive.
The removable-storage interfaces (1422) may also be in the form of ports or sockets for interfacing with other forms of removable-storage components (1423) such as a flash memory drive, external hard drive, or removable memory chip, etc.
The computing device (1400) may include an external communications interface (1430) for operation of the computing device (1400) in a networked environment enabling transfer of data between multiple computing devices (1400). Data transferred via the external communications interface (1430) may be in the form of signals, which may be electronic, electromagnetic, optical, radio, or other types of signal.
The external communications interface (1430) may enable communication of data between the computing device (1400) and other computing devices including servers and external storage facilities. Web services may be accessible by the computing device (1400) via the communications interface (1430).
The external communications interface (1430) may also enable other forms of communication to and from the computing device (1400) including, voice communication, near field communication, Bluetooth, etc.
The computer-readable media in the form of the various memory components may provide storage of computer-executable instructions, data structures, program modules, and other data. A computer program product may be provided by a computer-readable medium having stored computer-readable program code executable by the central processor (1410).
A computer program product may be provided by a non-transient computer-readable medium, or may be provided via a signal or other transient means via the communications interface (1430).
Interconnection via the communication infrastructure (1405) allows a central processor (1410) to communicate with each subsystem or component and to control the execution of instructions from the memory components, as well as the exchange of information between subsystems or components.
Peripherals (such as printers, scanners, cameras, or the like) and input/output (I/O) devices (such as a mouse, touchpad, keyboard, microphone, joystick, or the like) may couple to the computing device (1400) either directly or via an I/O controller (1435). These components may be connected to the computing device (1400) by any number of means known in the art, such as a serial port.
One or more monitors (1445) may be coupled via a display or video adapter (1440) to the computing device (1400).
FIG. 15 shows a block diagram of a communication device (1500) that may be used in embodiments of the disclosure. The communication device (1500) may be a cell phone, a feature phone, a smart phone, a satellite phone, or a computing device having a phone capability.
The communication device (1500) may include a processor (1505) (e.g., a microprocessor) for processing the functions of the communication device (1500) and a display (1520) to allow a user to see the phone numbers and other information and messages. The communication device (1500) may further include an input element (1525) to allow a user to input information into the device (e.g., input buttons, touch screen, etc.), a speaker (1530) to allow the user to hear voice communication, music, etc., and a microphone (1535) to allow the user to transmit his or her voice through the communication device (1500).
The processor (1510) of the communication device (1500) may connect to a memory (1515). The memory (1515) may be in the form of a computer-readable medium that stores data and, optionally, computer-executable instructions.
The communication device (1500) may also include a communication element (1540) for connection to communication channels (e.g., a cellular telephone network, data transmission network, Wi-Fi network, satellite-phone network, Internet network, Satellite Internet Network, etc.). The communication element (1540) may include an associated wireless transfer element, such as an antenna.
The communication element (1540) may include a subscriber identity module (SIM) in the form of an integrated circuit that stores an international mobile subscriber identity and the related key used to identify and authenticate a subscriber using the communication device (1500). One or more subscriber identity modules may be removable from the communication device (1500) or embedded in the communication device (1500).
The communication device (1500) may further include a contactless element (1550), which is typically implemented in the form of a semiconductor chip (or other data storage element) with an associated wireless transfer element, such as an antenna. The contactless element (1550) may be associated with (e.g., embedded within) the communication device (1500) and data or control instructions transmitted via a cellular network may be applied to the contactless element (1550) by means of a contactless element interface (not shown). The contactless element interface may function to permit the exchange of data and/or control instructions between mobile device circuitry (and hence the cellular network) and the contactless element (1550).
The contactless element (1550) may be capable of transferring and receiving data using a near field communications (NFC) capability (or near field communications medium) typically in accordance with a standardized protocol or data transfer mechanism (e.g., ISO 14443/NFC). Near field communications capability is a short-range communications capability, such as radio-frequency identification (RFID), Bluetooth, infra-red, or other data transfer capability that can be used to exchange data between the communication device (1500) and an interrogation device. Thus, the communication device (1500) may be capable of communicating and transferring data and/or control instructions via both a cellular network and near field communications capability.
The data stored in the memory (1515) may include: operation data relating to the operation of the communication device (1500), personal data (e.g., name, date of birth, identification number, etc.), financial data (e.g., bank account information, a bank identification number (BIN), credit or debit card number information, account balance information, expiration date, loyalty provider account numbers, etc.), transit information (e.g., as in a subway or train pass), access information (e.g., as in access badges), etc. A user may transmit this data from the communication device (1500) to selected receivers.
The communication device (1500) may be, amongst other things, a notification device that can receive alert messages and access reports, a portable merchant device that can be used to transmit control data identifying a discount to be applied, as well as a portable consumer device that can be used to make payments.
The foregoing description of the embodiments of the invention has been presented for the purpose of illustration; it is not intended to be exhaustive or to limit the invention to the precise forms disclosed. Persons skilled in the relevant art can appreciate that many modifications and variations are possible in light of the above disclosure.
Some portions of this description describe the embodiments of the invention in terms of algorithms and symbolic representations of operations on information. These algorithmic descriptions and representations are commonly used by those skilled in the data processing arts to convey the substance of their work effectively to others skilled in the art. These operations, while described functionally, computationally, or logically, are understood to be implemented by computer programs or equivalent electrical circuits, microcode, or the like. The described operations may be embodied in software, firmware, hardware, or any combinations thereof.
The software components or functions described in this application may be implemented as software code to be executed by one or more processors using any suitable computer language such as, for example, Java, C++, or Perl using, for example, conventional or object-oriented techniques. The software code may be stored as a series of instructions, or commands on a non-transitory computer-readable medium, such as a random access memory (RAM), a read-only memory (ROM), a magnetic medium such as a hard-drive or a floppy disk, or an optical medium such as a CD-ROM. Any such computer-readable medium may also reside on or within a single computational apparatus, and may be present on or within different computational apparatuses within a system or network.
Any of the steps, operations, or processes described herein may be performed or implemented with one or more hardware or software modules, alone or in combination with other devices. In one embodiment, a software module is implemented with a computer program product comprising a non-transient computer-readable medium containing computer program code, which can be executed by a computer processor for performing any or all of the steps, operations, or processes described.
Finally, the language used in the specification has been principally selected for readability and instructional purposes, and it may not have been selected to delineate or circumscribe the inventive subject matter. It is therefore intended that the scope of the invention be limited not by this detailed description, but rather by any claims that issue on an application based hereon. Accordingly, the disclosure of the embodiments of the invention is intended to be illustrative, but not limiting, of the scope of the invention, which is set forth in the following claims.
* * * * *
D00000

D00001

D00002

D00003

D00004

D00005

D00006

D00007

D00008

D00009

D00010

XML
uspto.report is an independent third-party trademark research tool that is not affiliated, endorsed, or sponsored by the United States Patent and Trademark Office (USPTO) or any other governmental organization. The information provided by uspto.report is based on publicly available data at the time of writing and is intended for informational purposes only.
While we strive to provide accurate and up-to-date information, we do not guarantee the accuracy, completeness, reliability, or suitability of the information displayed on this site. The use of this site is at your own risk. Any reliance you place on such information is therefore strictly at your own risk.
All official trademark data, including owner information, should be verified by visiting the official USPTO website at www.uspto.gov. This site is not intended to replace professional legal advice and should not be used as a substitute for consulting with a legal professional who is knowledgeable about trademark law.