Packet Sending Method and Device
Kind Code
U.S. patent application number 16/857825 was filed with the patent office on 2020-08-06 for packet sending method and device. The applicant listed for this patent is Huawei Technologies Co., Ltd.. Invention is credited to Xia Chen, Yongkang Zhang.
| Application Number | 20200252366 16/857825 |
| Document ID | 20200252366 / US20200252366 |
| Family ID | 1000004823961 |
| Filed Date | 2020-08-06 |
| Patent Application | download [pdf] |

| United States Patent Application | 20200252366 |
| Kind Code | A1 |
| Zhang; Yongkang ; et al. | August 6, 2020 |
Packet Sending Method and Device
Abstract
This application provides a packet sending method, applied to an anycast service-based network. The method includes: obtaining, by a client device, an IP anycast address of the anycast server cluster and an IP unicast address of the target server; generating, by the client device, an IP detection packet, where the IP detection packet is used to detect whether the target server is reachable based on the IP anycast address, and the IP detection packet includes the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address; and sending, by the client device, the IP detection packet to the target server. This helps accurately detect IP anycast address reachability of a designate anycast server.
| Inventors: | Zhang; Yongkang; (Nanjing, CN) ; Chen; Xia; (Beijing, CN) | ||||||||||
| Applicant: |
|
||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Family ID: | 1000004823961 | ||||||||||
| Appl. No.: | 16/857825 | ||||||||||
| Filed: | April 24, 2020 |
Related U.S. Patent Documents
| Application Number | Filing Date | Patent Number | ||
|---|---|---|---|---|
| PCT/CN2018/099413 | Aug 8, 2018 | |||
| 16857825 | ||||
| Current U.S. Class: | 1/1 |
| Current CPC Class: | H04L 61/2046 20130101; H04L 67/42 20130101; H04L 49/3009 20130101 |
| International Class: | H04L 29/12 20060101 H04L029/12; H04L 12/935 20060101 H04L012/935 |
Foreign Application Data
| Date | Code | Application Number |
|---|---|---|
| Oct 27, 2017 | CN | 201711025021.9 |
Claims
1. A packet sending method, applied to an anycast service-based network, wherein the network comprises a client device and an anycast server cluster, the anycast server cluster comprises at least two servers, the at least two servers have a same IP anycast address, and the method comprises: obtaining, by the client device, the IP anycast address and an IP unicast address of a target server in the at least two servers; generating, by the client device, an IP detection packet, wherein the IP detection packet is used to detect whether the target server is reachable based on the IP anycast address, and the IP detection packet comprises the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address; and sending, by the client device, the IP detection packet to the target server.
2. The method according to claim 1, wherein the obtaining, by the client device, the IP anycast address and an IP unicast address of a target server comprises: obtaining, by the client device, the IP anycast address and the IP unicast address of the target server by using a user-configured command line; or receiving, by the client device, a message sent by a control management device, and obtaining the IP anycast address and the IP unicast address of the target server from the message.
3. The method according to claim 1, wherein that the IP detection packet comprises the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address comprises: a destination IP address field in the IP detection packet carries the IP unicast address of the target server, a segment list field in an IP segment routing header SRH in the IP detection packet carries the IP anycast address, a value of a segment left SegLeft field in the IP SRH is 1, and the value of the SegLeft field instructs the target server to replace the IP unicast address of the target server with the IP anycast address.
4. The method according to claim 1, wherein the method further comprises: obtaining, by the client device, an IP unicast address of at least one designate middle node on a forwarding path from the client device to the target server; and correspondingly, obtaining, by the client device, the IP unicast address of the at least one designate middle node by using a user-configured command line; or receiving, by the client device, a message sent by the control management device, and obtaining the IP unicast address of the at least one designate middle node from the message.
5. The method according to claim 4, wherein that the IP detection packet comprises the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address comprises: a destination IP address field in the IP detection packet carries an IP unicast address of a first designate middle node, and the first designate middle node is a first designate middle node on the forwarding path from the client device to the target server; and a segment list field in an IP segment routing header SRH in the IP detection packet carries the IP anycast address, the IP unicast address of the target server, and the IP unicast address of the at least one designate middle node, a value of a segment left SegLeft field in the IP SRH is 1 plus a quantity of designate middle nodes, and when the value of the SegLeft field is 1, the value of the SegLeft field instructs the target server to replace the IP unicast address of the target server with the IP anycast address.
6. The method according to claim 1, wherein the method further comprises: when receiving, within a predetermined time interval, a response packet sent by the target server, determining, by the client device, that the target server is reachable based on the IP anycast address; or when receiving, within the predetermined time interval, no response packet sent by the target server, determining, by the client device, that the target server is unreachable based on the IP anycast address, wherein the response packet is a response packet to the IP detection packet.
7. A client device, applied to an anycast service-based network, wherein the network comprises the client device and an anycast server cluster, the anycast server cluster comprises at least two servers, the at least two servers have a same IP anycast address, and the client device comprises: a transceiver; a processor; a memory storing computer executable instructions; the processor being execute the executable instructions to: obtain the IP anycast address of the anycast server cluster and an IP unicast address of a target server in the at least two servers; generate an IP detection packet, wherein the IP detection packet is used to detect whether the target server is reachable based on the IP anycast address, and the IP detection packet comprises the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address; and send, via the transceiver, the IP detection packet to the target server.
8. The client device according to claim 7, wherein the processor being execute the executable instructions to: obtain the IP anycast address and the IP unicast address of the target server by using a user-configured command line; or the transceiver receives a message sent by a control management device, and the processor being execute the executable instructions to obtain the IP anycast address and the IP unicast address of the target server from the message.
9. The client device according to claim 7, wherein a destination IP address field in the IP detection packet carries the IP unicast address of the target server, a segment list field in an IP segment routing header SRH in the IP detection packet carries the IP anycast address, a value of a segment left SegLeft field in the IP SRH is 1, and the value of the SegLeft field instructs the target server to replace the IP unicast address of the target server with the IP anycast address.
10. The client device according to claim 7, wherein the processor further being execute the executable instructions to obtain an IP unicast address of at least one designate middle node on a forwarding path from the client device to the target server, wherein the IP unicast address of at least one designate middle node is obtained by using a user-configured command line or by receiving a message sent by the control management device.
11. The client device according to claim 10, wherein a destination IP address field in the IP detection packet carries an IP unicast address of a first designate middle node, and the first designate middle node is a first designate middle node on the forwarding path from the client device to the target server; and a segment list field in an IP segment routing header SRH in the IP detection packet carries the IP anycast address, the IP unicast address of the target server, and the IP unicast address of the at least one designate middle node, a value of a segment left SegLeft field in the IP SRH is 1 plus a quantity of designate middle nodes, and when the value of the SegLeft field is 1, the value of the SegLeft field instructs the target server to replace the IP unicast address of the target server with the IP anycast address.
12. The client device according to claim 7, wherein the processor further being execute the executable instructions to: determine that the target server is reachable based on the IP anycast address when the transceiver receives, within a predetermined time interval, a response packet sent by the target server; or determine that the target server is unreachable based on the IP anycast address when the transceiver receives, within the predetermined time interval, no response packet sent by the target server.
Description
CROSS-REFERENCE TO RELATED APPLICATIONS
[0001] This application is a continuation of International Application No. PCT/CN2018/099413, filed on Aug. 8, 2018, which claims priority to Chinese Patent Application No. 201711025021.9, filed on Oct. 27, 2017. The disclosures of the aforementioned applications are hereby incorporated by reference in their entireties.
TECHNICAL FIELD
[0002] The present invention relates to the field of communications technologies, and specifically, to a packet sending method and a client device.
BACKGROUND
[0003] Internet Protocol (IP) anycast is a network addressing and routing method, in which a data packet from a transmit end (or a client) device is routed to any one of several destination nodes (or servers) based on a policy of shortest path, lowest cost, healthiest, least congestion routing, or some other distance measurement policies. The IP anycast is an operation of providing a same designate service address at a plurality of discrete and autonomous locations. The service address may be an IPv6 address (in this case, the IP anycast is referred to as IPv6 anycast), or may be an IPv4 address (in this case, the IP anycast is referred to as IPv4 anycast). The IP anycast is generally used to provide high reliability and load balancing, and is widely deployed in existing networks. For example, in a Domain Name System (DNS) root server, and network scenarios such as a Protocol Independent Multicast (PIM) network scenario, a Multicast Source Discovery Protocol (MSDP) network scenario, and a 6 to 4 network scenario that supports transition from an Internet Protocol version 6 (IPv6) to an Internet Protocol version 4 (IPv4), an IP anycast address is used.
[0004] However, an IP anycast address identifies a server group rather than a server. In other words, a cluster of servers share an IP anycast address. Therefore, in an existing IP ping/tracert detection method in which the IP anycast address is used as a destination address, IP anycast address reachability of a designate anycast server in the server cluster cannot be accurately detected.
SUMMARY
[0005] Embodiments of the present invention provide a packet sending method and a client device, to help resolve a problem that IP anycast address reachability of a designate anycast server cannot be accurately detected in an anycast service-based network.
[0006] To resolve the foregoing problem, a first aspect of the embodiments of the present invention provides a packet sending method, applied to an anycast service-based network. The network includes a client device and an anycast server cluster, the anycast server cluster includes at least two servers, the at least two servers have a same IP anycast address, and the method includes: obtaining, by the client device, the IP anycast address of the anycast server cluster and an IP unicast address of a target server; generating, by the client device, an IP detection packet, where the IP detection packet is used to detect whether the target server is reachable based on the IP anycast address, and the IP detection packet includes the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address; and sending, by the client device, the IP detection packet to the target server.
[0007] The IP detection packet carries the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address. This helps accurately detect IP anycast address reachability of a designate anycast server.
[0008] In a possible design, the obtaining, by the client device, the IP anycast address of the anycast server cluster and an IP unicast address of the target server includes: obtaining, by the client device, the IP anycast address and the IP unicast address of the target server by using a user-configured command line; or receiving, by the client device, a message sent by a control management device, and obtaining the IP anycast address and the IP unicast address of the target server from the message.
[0009] A to-be-detected server in the anycast server cluster may be flexibly designated as required by configuring a command line or receiving a configuration parameter sent by the control management device.
[0010] In a possible design, that the IP detection packet includes the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address includes: a destination IP address field in the IP detection packet carries the IP unicast address of the target server, a segment list field in an IP segment routing header SRH in the IP detection packet carries the IP anycast address, a value of a segment left SegLeft field in the IP SRH is 1, and the value of the SegLeft field instructs the target server to replace the IP unicast address of the target server with the IP anycast address.
[0011] The IP detection packet carries the SRH to carry the IP anycast address, and the value 1 of SegLeft is used to instruct the target server to replace the IP unicast address of the target server with the IP anycast address, so that the IP detection packet can be sent to the IP anycast address of a server in the anycast server cluster simply and accurately.
[0012] In a possible design, the method further includes: obtaining, by the client device, an IP unicast address of at least one designate middle node on a forwarding path from the client device to the target server; and correspondingly, obtaining, by the client device, the IP unicast address of the at least one designate middle node by using a user-configured command line; or receiving, by the client device, a message sent by the control management device, and obtaining the IP unicast address of the at least one designate middle node from the message.
[0013] A middle node that needs to be included on a to-be-detected path is designated by configuring a command line or receiving a configuration parameter sent by the control management device, so that the middle node that needs to be included on the to-be-detected path and a to-be-detected server in the anycast server cluster may be flexibly designated as required.
[0014] In a possible design, that the IP detection packet includes the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address includes: a destination IP address field in the IP detection packet carries an IP unicast address of a first designate middle node, and the first designate middle node is a first designate middle node on the forwarding path from the client device to the target server; and a segment list field in an IP segment routing header SRH in the IP detection packet carries the IP anycast address, the IP unicast address of the target server, and the IP unicast address of the at least one designate middle node, a value of a segment left SegLeft field in the IP SRH is 1 plus a quantity of designate middle nodes, and when the value of the SegLeft field is 1, the value of the SegLeft field instructs the target server to replace the IP unicast address of the target server with the IP anycast address.
[0015] The IP detection packet carries the SRH to carry the IP anycast address, the IP unicast address of the designate middle node, and the IP unicast address of the target server, and the value 1 of SegLeft is used to instruct the target server to replace the IP unicast address of the target server with the IP anycast address, so that the IP detection packet can be sent to the IP anycast address of a server in the anycast server cluster simply and accurately by using the designate middle node.
[0016] In a possible design, when receiving, within a predetermined time interval, a response packet sent by the target server, the client device determines that the target server is reachable based on the IP anycast address; when receiving, within the predetermined time interval, no response packet sent by the target server, the client device determines that the target server is unreachable based on the IP anycast address.
[0017] Whether the target server is reachable based on the IP anycast address (for example, whether a fault occurs) can be accurately determined based on whether the response packet to IP detection can be received within the predetermined time interval.
[0018] According to a second aspect, the present invention provides a client device. The client device is configured to perform the method in any one of the first aspect or the possible implementations of the first aspect. Specifically, the client device includes a module configured to perform the method in any one of the first aspect or the possible implementations of the first aspect.
[0019] According to a third aspect, the present invention provides a client device. The client device includes a processor, a transceiver, a random access memory, a read-only memory, and a bus. The processor is separately coupled to the transmitter, the random access memory, and the read-only memory by using the bus. When the client device needs to be run, a bootloader in a basic input/output system or an embedded system that is built into the read-only memory is used to lead a system to start, and lead the client device to enter a normal running state. After the client device enters the normal running state, an application program and an operating system are run in the random access memory, to enable the processor to perform the method in any one of the first aspect or the possible implementations of the first aspect.
[0020] According to a fourth aspect, a client device is provided. The client device includes a central processing unit, a forwarding entry storage, a physical interface network card, and a network forwarding processor. The client device is configured to perform the method in any possible implementation of the first aspect. Specifically, the client device includes a module configured to perform the method in any one of the first aspect or the possible implementations of the first aspect.
[0021] According to a fifth aspect, the present invention provides a computer readable medium, including an instruction. When the instruction is run on a computer, the computer is enabled to perform the method in any one of the first aspect or the possible implementations of the first aspect.
BRIEF DESCRIPTION OF DRAWINGS
[0022] To describe technical solutions in embodiments of this application or in the prior art more clearly, the following briefly describes the accompanying drawings required for describing the embodiments or the prior art. Apparently, the accompanying drawings in the following description show merely some embodiments recorded in this application, and a person of ordinary skill in the art may still derive other drawings from these accompanying drawings.
[0023] FIG. 1a is a schematic diagram of an application scenario of packet sending according to an embodiment of the present invention;
[0024] FIG. 1b is a schematic structural diagram of an SRH packet header according to an embodiment of the present invention;
[0025] FIG. 1c-1 and FIG. 1c-2 are a schematic flowchart of SRH forwarding according to an embodiment of the present invention;
[0026] FIG. 2 is a schematic flowchart of a packet sending method according to an embodiment of the present invention;
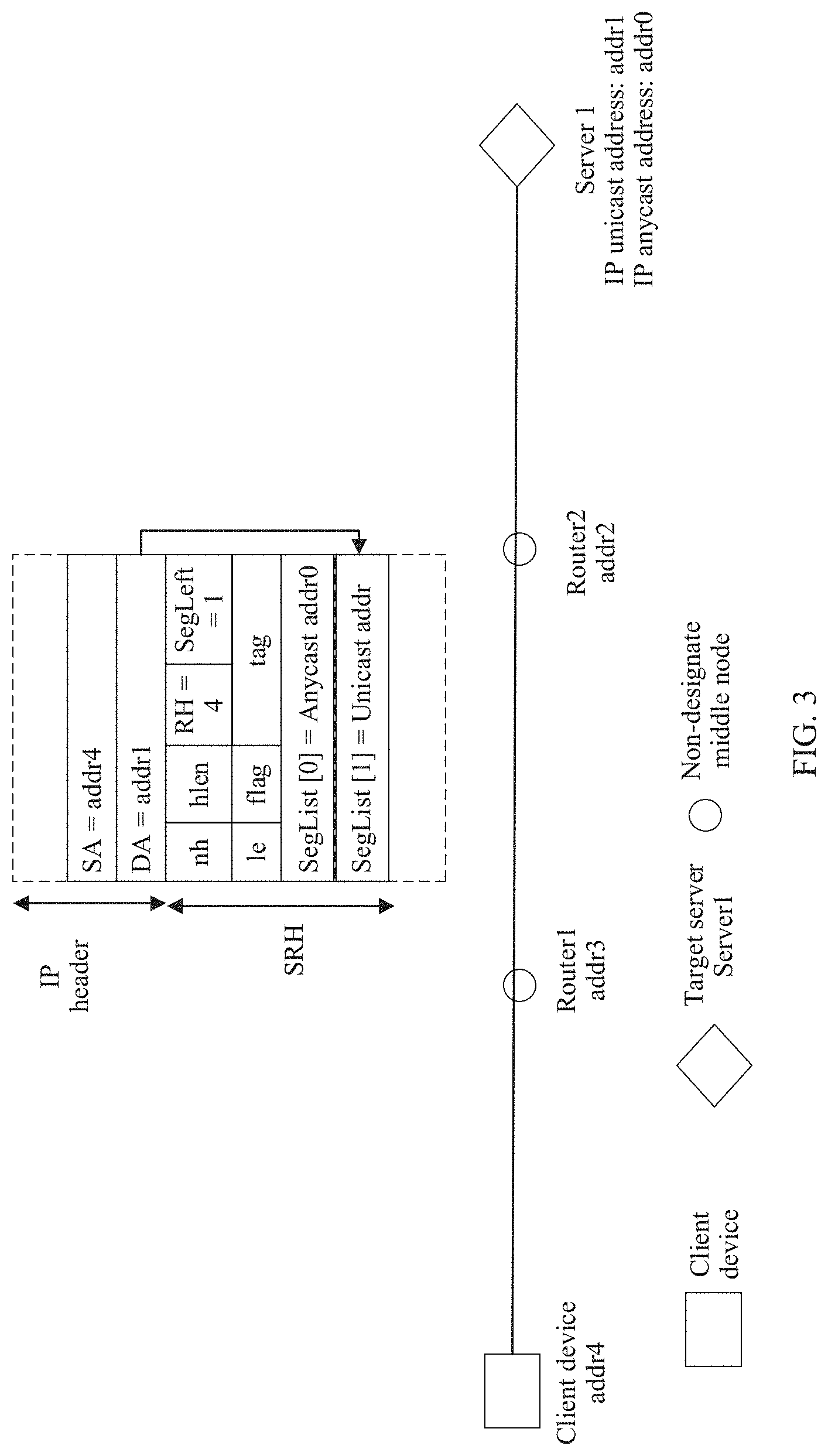
[0027] FIG. 3 is a schematic flowchart of forwarding without a designate middle node according to an embodiment of the present invention;
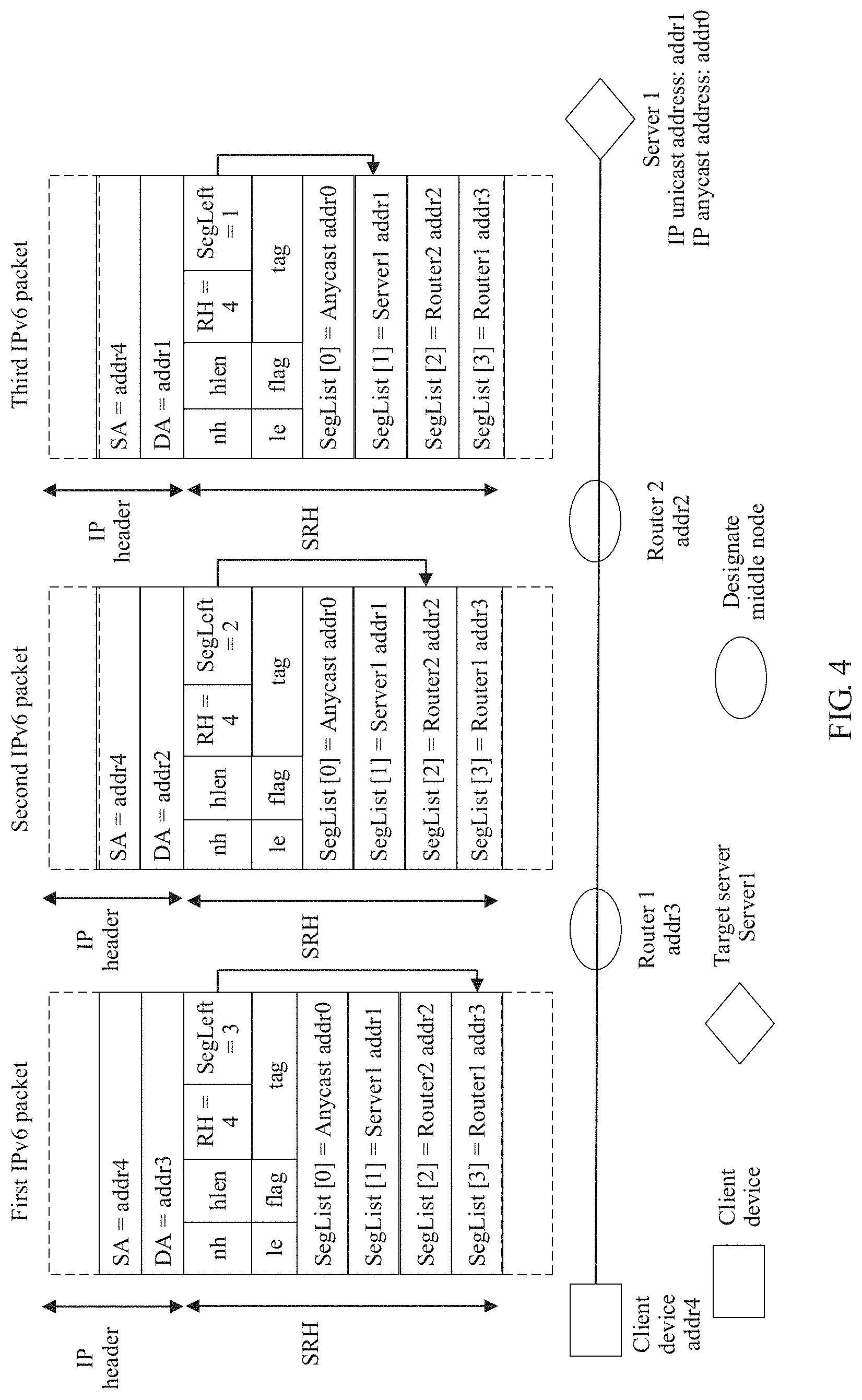
[0028] FIG. 4 is a schematic flowchart of forwarding with a designate middle node according to an embodiment of the present invention;
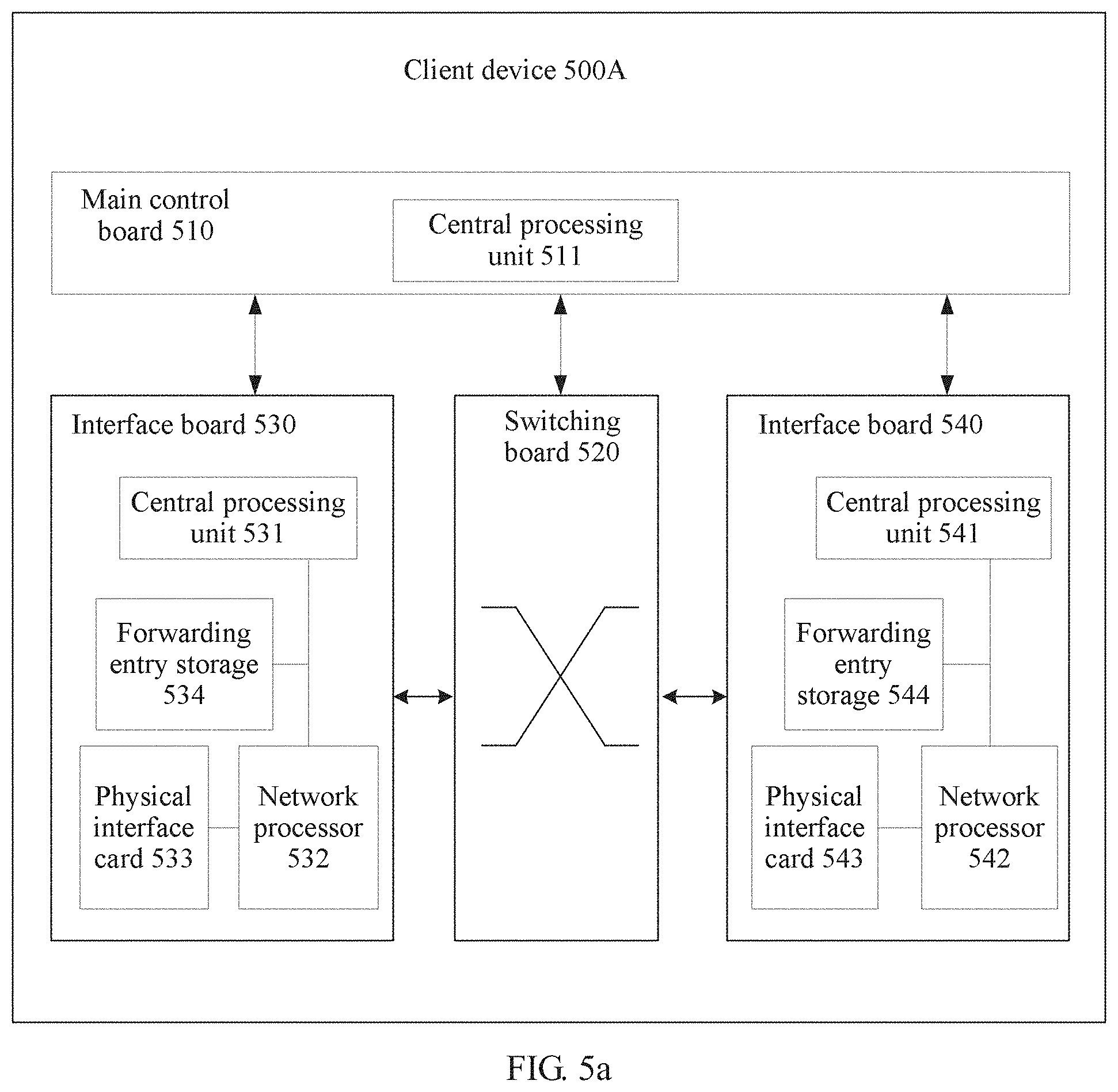
[0029] FIG. 5a is a schematic structural diagram of a client device according to an embodiment of the present invention;
[0030] FIG. 5b is a schematic structural diagram of another client device according to an embodiment of the present invention; and
[0031] FIG. 5c is a schematic structural diagram of still another client device according to an embodiment of the present invention;
DESCRIPTION OF EMBODIMENTS
[0032] To enable a person skilled in the art to better understand solutions in the present invention, the following describes embodiments of the present invention in more detail with reference to accompanying drawings and implementations. Apparently, the described embodiments are some rather than all of the embodiments of the present invention. All other embodiments obtained by a person of ordinary skill in the art based on the embodiments of the present invention without creative efforts shall fall within the protection scope of the present invention.
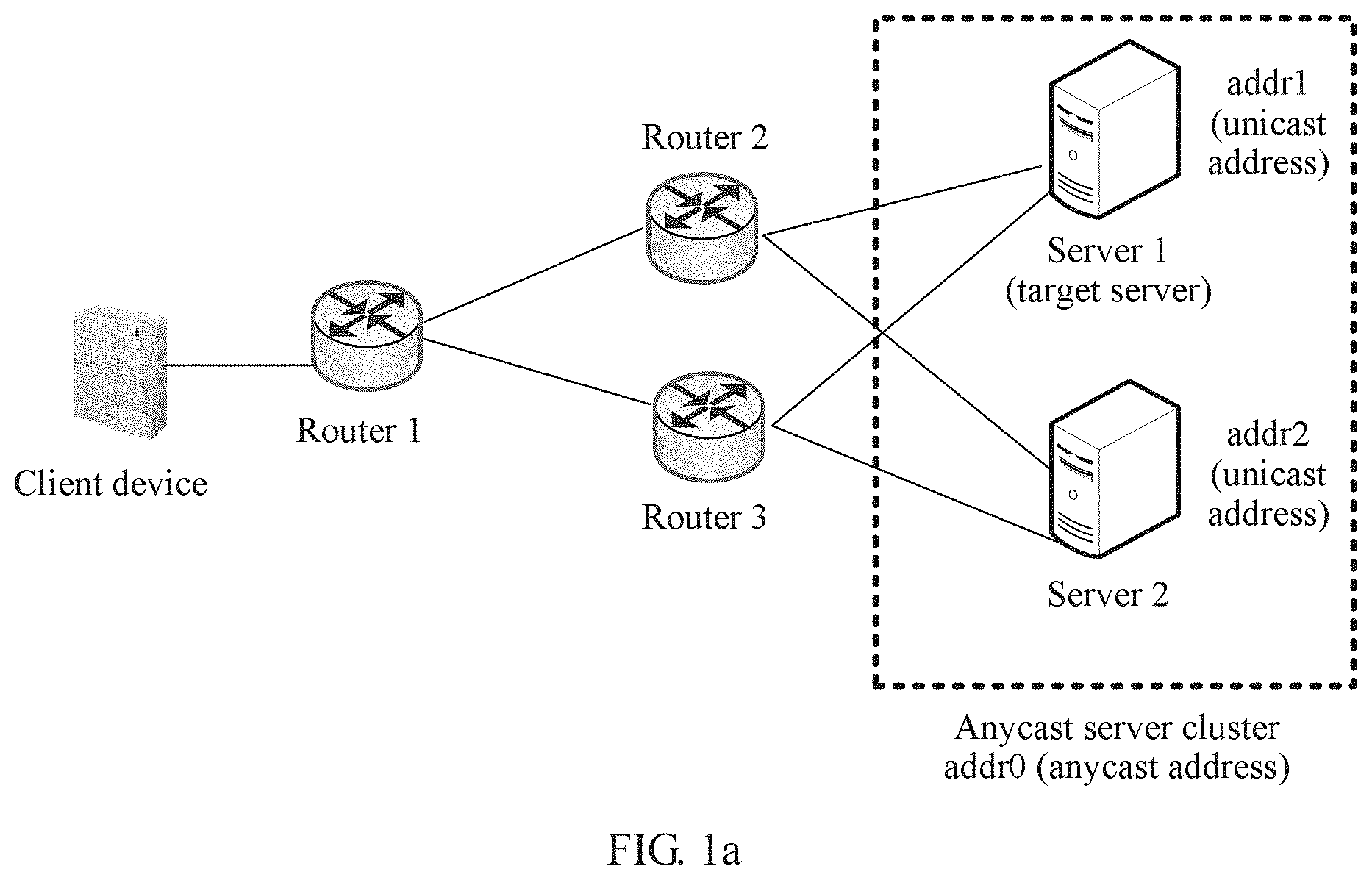
[0033] Before the technical solutions of the embodiments of the present invention are described, an application scenario related to the embodiments of the present invention is explained first. The present invention is applied to an IP anycast service network. The IP anycast service network includes a client device, an anycast server cluster, and a routing device (for example, a router or a switch). As shown in FIG. 1a, a client device accesses a server 1 and a server 2 in the anycast server cluster by using a routing network including a router 1, a router 2, and a router 3. An IP anycast address addr0 is used to identify the anycast server cluster and is shared between the server 1 and the server 2. An IP unicast address addr1 is used to identify the server 1, and may be, for example, an IP address of a network interface on the server 1. An IP unicast address addr2 is used to identify the server 2, and may be, for example, an IP address of a network interface on the server 2.
[0034] An IPv6 anycast address and an IPv6 unicast address use same address space. Except a reserved subnet anycast address defined in IETF RFC 2526 and a subnet-router anycast address defined in RFC 4291, the IPv6 anycast address has no obvious feature. When a unicast address is assigned to a plurality of interfaces (on a same device or different devices), whether the unicast address is an IP anycast address needs to be indicated through explicit configuration.
[0035] The IPv6 anycast address is usually configured on a plurality of interfaces to represent a group of servers that provide a same service externally. When the IP anycast address is used as a destination address, a "nearest" device is selected by using a routing algorithm for access. In this way, a distributed service is implemented, and advantages of load balancing and high reliability are achieved.
[0036] For an IPv6 anycast service, because the IPv6 anycast address is essentially an IPv6 unicast address, an IPv6 ping/tracers IP detection packet may be used to detect the IPv6 anycast address. A method for detecting the IPv6 anycast address is the same as a method for detecting a common unicast address. The client device may detect, by using the IPv6 anycast address as a destination IP address, whether the IPv6 anycast service is reachable. For example, as shown in FIG. 1a, the client device generates a routing entry whose destination IP is addr0 by using a dynamic routing protocol (or through static route configuration), and instructs the routing device (the routers 1, 2, and 3) to forward, to the server 1, an IP detection packet sent by the client device. If the server 1 works normally, the IPv6 anycast service is reachable. In this case, because the routing entries whose destination IPs are addr0 on the router 1, the router 2, and the router 3 all point to the server 1, whether the server 2 is reachable from the client device cannot be detected for a user as expected.
[0037] After a fault occurs on the server 1, a routing entry whose destination IP is addr0 is regenerated through route reconvergence, and the routing device is instructed to forward, to the server 2, an IP detection packet sent by the client device. If the server 2 works normally, the IPv6 anycast service is reachable. Therefore, provided that any server in the anycast server cluster works normally, the anycast service is reachable in ping/tracert detection. In this way, the anycast service has an advantage of high reliability. However, in this case, because the routing entries whose destination IPs are addr0 on the router 1, the router 2, and the router 3 all point to the server 2 (in other words, the packet may finally reach the server 2 after being forwarded based on outbound interfaces in the routing entries), whether the server 1 is reachable from the client device cannot be detected for a user as expected.
[0038] Therefore, in the existing ping/tracert detection method in which an IP anycast address is used as a destination address, a ping/tracert IP detection packet cannot be accurately sent to a designate server as required. Further, it cannot be learned whether a designate server in the anycast server cluster is faulty.
[0039] It should be noted that the client device in this application is a device that supports IP anycast. For example, the client device may be a PC, a laptop, or a PAD in a broadband access network, a router or a switch in a routing network, a sensor or an IoT gateway in an internet of things (Internet of Things, IoT) network, or a base station or a mobile phone in a mobile network. The anycast server cluster in this application may include at least two servers. FIG. 1a shows two devices only for example, which does not constitute any limitation. Certainly, the anycast server cluster may alternatively be another network device cluster that supports the IP anycast service, for example, a router or switch cluster. The server, the router, and the switch may be physical devices, or may be virtual devices implemented based on a virtualization technology (for example, a virtual server, a virtual router, and a virtual switch).
[0040] The foregoing describes a possible application scenario related to the present invention. Before the embodiments of the present invention are described in detail, an IP segment routing technology is briefly described first. IP forwarding is basically characterized by connectionless and hop-by-hop forwarding. A forwarding path of an IP packet is obtained by completely relying on advertisement and convergence of a route (a static route and/or a dynamic route). Generally, a route calculation system selects a "shortest path". However, in some scenarios, the "shortest path" may not meet a user expectation, and some difficulties may be encountered in implementing traffic engineering (Traffic Engineering, TE). To overcome the above limitations of the IP forwarding mechanism to some extent, IP source routing is proposed. The IP source routing supports direct addition of information about a forwarding path to an IP packet.
[0041] In IPv4, to support source routing, a loose source routing (LSRR) option and a strict source routing (SSRR) option are defined in RFC 791. However, practicability is limited by a maximum space of 40 bytes of an IPv4 option.
[0042] In IPv6, to support source routing, a routing header is defined in Request For Comments (RFC) 2460 published by the Internet engineering task force (Internet Engineering Task Force, IETF), and a new source routing mechanism may be added by defining a new routing type (Routing Type). In addition, a routing header whose route type is 0 (type 0) is defined in RFC 2460. The type 0 routing header is basically equivalent to the LSRR in IPv4, but is not limited by the 40-byte space of the IPv4 option.
[0043] However, after further analysis, the IETF finds that the type 0 routing header in IPv6 has a serious security problem. Therefore, a definition of the type 0 routing header is abandoned in RFC 5095, but an IPv6 routing header mechanism is not abandoned.
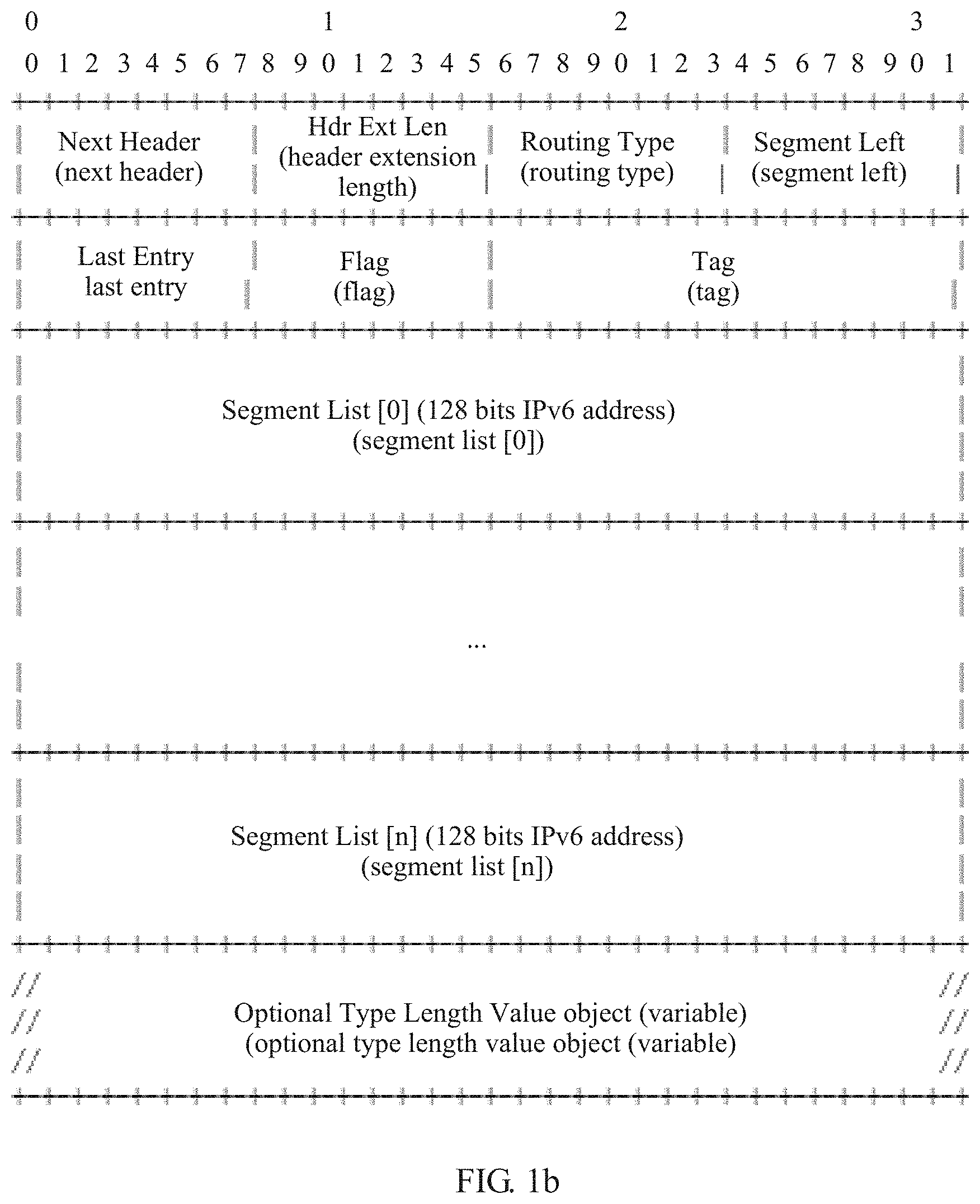
[0044] The IPv6 routing header is a source routing mechanism in a loose mode. With further development of an IP network, increasing attention is paid to the source routing idea. For this reason, the established a SPRING working group to implement related standardization work. The SPRING working group refers to a newly designed source routing mechanism as segment routing (Segment Routing, SR). A data plane uses two modes: MPLS and IPv6. Segment routing in the IPv6 mode (referred to as SR IPv6) is implemented by defining a new IPv6 routing header (referred to as an SRH). Refer to draft-ietf-6man-segment-routing-header-07 (the draft is defined by the 6man working group). As shown in FIG. 1b, an SRH extension header includes a next header (Next Header) field, a segment left (Segment Left) field, and a segment list (Segment List [n]) field. The next header field indicates a protocol header carried behind an SRH. The segment list field carries an IP address of each node (except a source node) that needs to be included on a forwarding path, and is expressed in an array form. An index value of the array ranges from 0 to n, and n is a positive integer. n+1 represents a quantity of designate nodes that need to be included on the forwarding path except the source node. The segment left field indicates the index of the array.
[0045] The following describes a processing procedure of the SRH extension header by using an example. After receiving an IP packet, when determining that a destination IP address carried in an IP packet header is equal to a local IP address of the network node, the network node continues to determine whether a value of the segment left field (referred to as a segment left value for short) is greater than 0. If the segment left value is greater than 0, the segment left value is subtracted by 1, and the network node replaces the destination IP address in the IP packet header with an IP address corresponding to Segment List [the segment left value subtracted by 1], and performs corresponding packet processing by searching a forwarding information base (Forwarding Information Base, FIB) table by using the updated destination IP address.
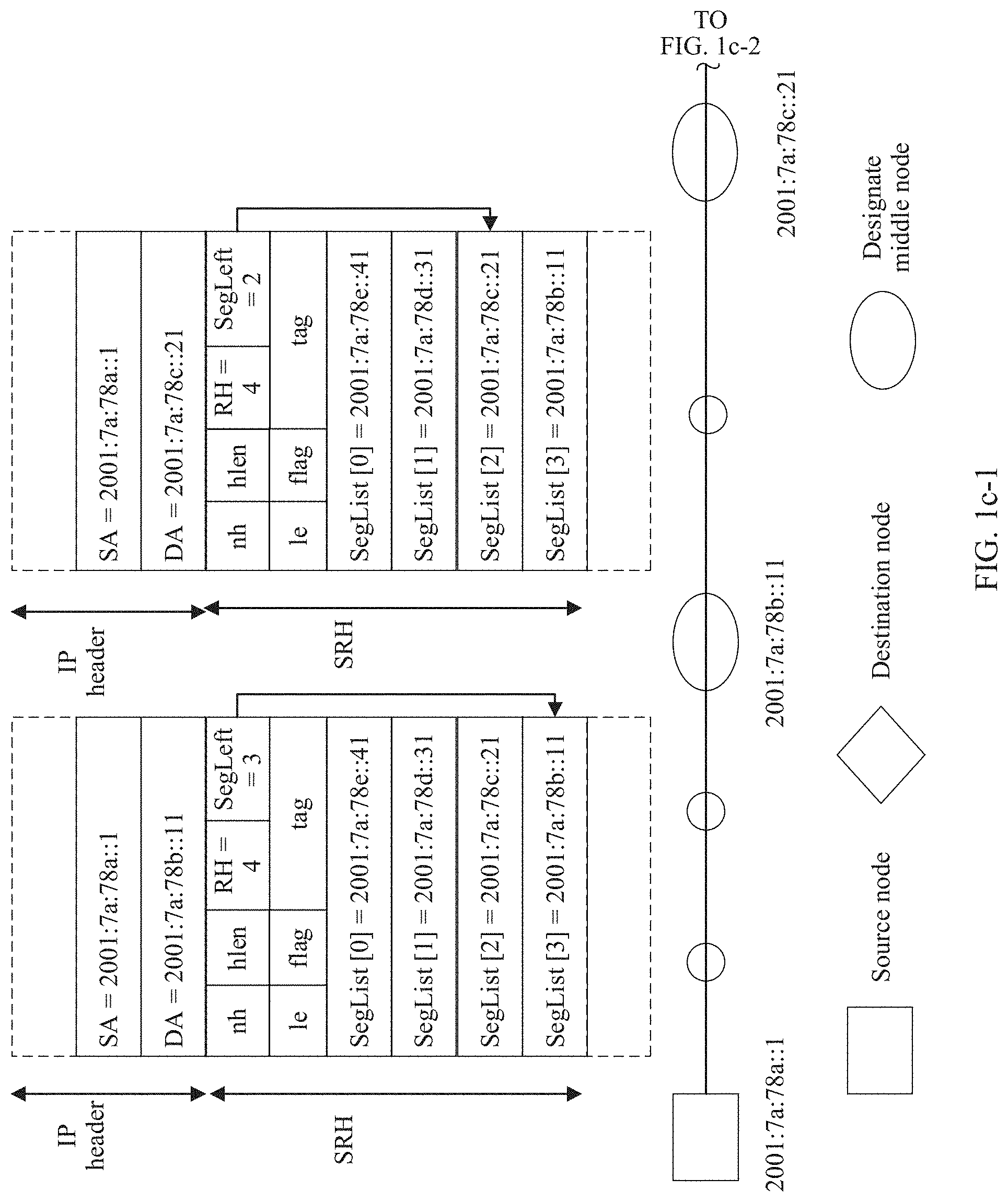
[0046] A forwarding procedure of an IPv6 packet that carries an SRH is described in detail by using a network scenario shown in FIG. 1c-1 and FIG. 1c-2 as an example. For example, a packet is sent from a source node (whose IPv6 address is 2001:7a:78a::1) to a destination node (whose IPv6 address is 2001:7a:78e::41) through three designate middle nodes (the nodes may be network routing and switching devices such as a router and a switch) and several non-designate middle nodes. The designate middle node refers to a node that is designated in advance as needing to be included on a path from the source node to the destination node. The non-designate middle node refers to a node that is not designated in advance as needing to be included on the path from the source node to the destination node, but a node that is determined by searching an IP routing and forwarding table as needing to be included on the path. It is assumed that IP addresses of the three designate middle nodes are 2001:7a:78b::11 (a first designate middle node), 2001:7a:78c::21 (a second designate middle node), and 2001:7a:78d::31 (a third designate middle node). The source node sends, to the first designate middle node, a first IPv6 packet that carries an SRH extension header. A source address field in the IPv6 packet header is the IPv6 address of the source node (SA=2001:7a:78a::1), and a destination address field is the IPv6 address of the first designate middle node (DA=2001:7a:78b::11). The SRH extension header includes Segment Left (referred to as SegLeft for short, whose value is 3) and Segment List (referred to as SegList for short). An index of the SegList array ranges from 0 to 3: SegList [3] to SegList [0], which sequentially represent IPv6 addresses of nodes that need to be included on the forwarding path. SegList [3] is the IPv6 address of the first designate middle node. SegList [2] is the IPv6 address of the second designate middle node. SegList [1] is the IPv6 address of the third designate middle node. SegList [0] is the IPv6 address of the final destination node.
[0047] After receiving the first IPv6 packet, the first designate node finds that the DA carried in the first IPv6 packet is the IPv6 address of the first designate node, and continues to parse out SegLeft carried in the SRHI extension header. Then, if determining that SegLeft (whose value is 3) is greater than 0, the first designate node subtracts SegLeft by 1 (to obtain 2), and refreshes the value of the DA field to the IPv6 address (the IPv6 address of the second designate middle node) in SegList [SegLeft]=SegList [2]. The first designate node obtains a matched entry by searching a FIB table by using the refreshed IPv6 address of the second designate middle node. Further, the first designate node generates a second IPv6 packet, and sends the second IPv6 packet to the second designate middle node based on the matched entry. A source address field in an IPv6 packet header of the second IPv6 packet is the IPv6 address of the source node (SA=2001:7a:78a::1), and a destination address field is the IPv6 address of the second designate middle node (DA=2001:7a). 78c::21). SRH extension header includes Segment Left (referred to as SegLeft for short, whose value is 2).
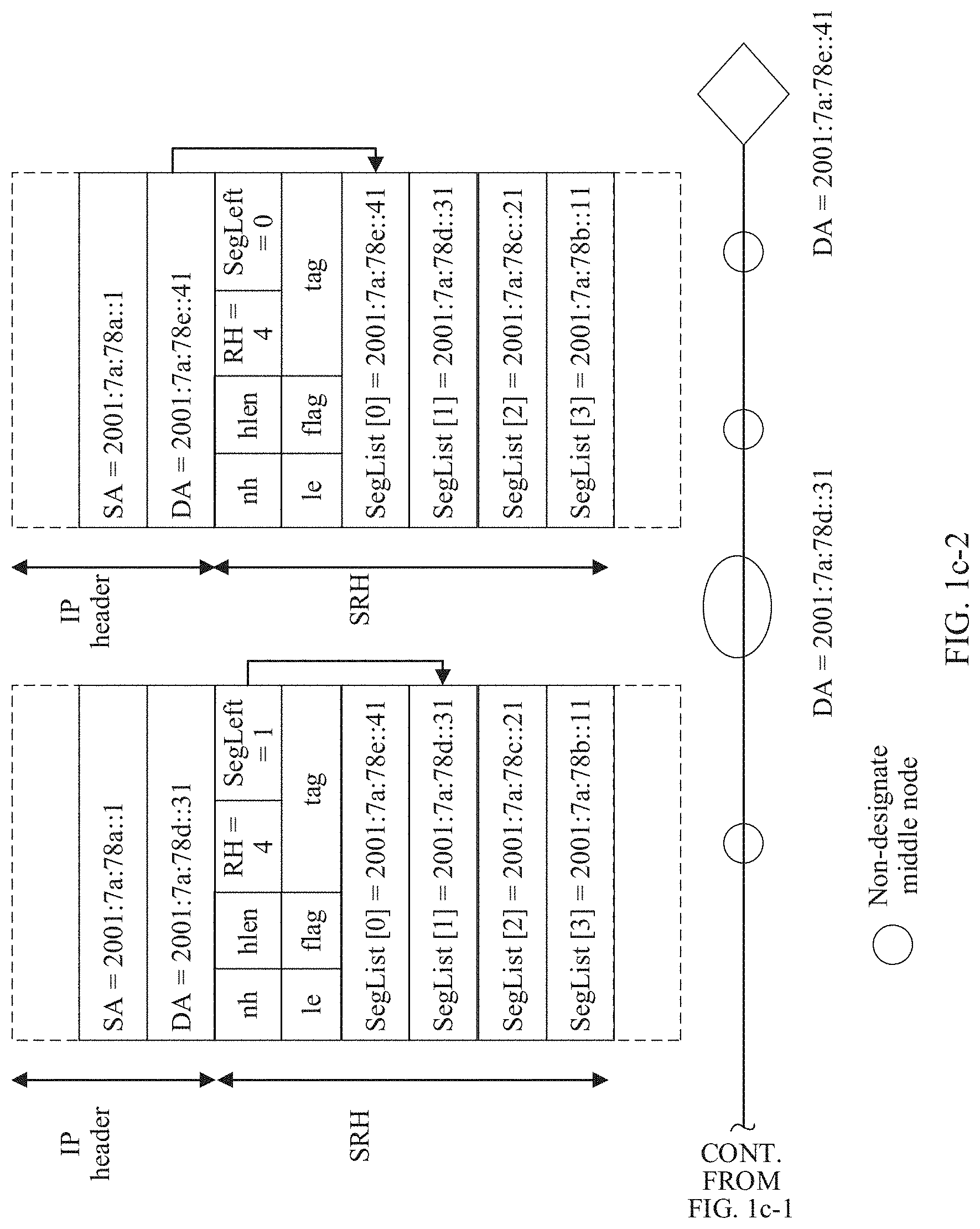
[0048] After the second designate middle node receives the second IPv6 packet, the second designate middle node performs processing by using a method the same as above (for brevity, details are not described herein again), generates a third IPv6 packet, and sends the third IPv6 packet to the third designate middle node. A source address field in an IPv6 packet header of the third IPv6 packet is the IPv6 address of the source node (SA=2001:7a:78a::1), and a destination address field is the IPv6 address of the third designate middle node (DA=2001:7a:78d::31). An SRH extension header includes SegLeft whose value is 1.
[0049] After the third designate node receives the third IPv6 packet, the third designate middle node performs processing by using a method the same as above (for brevity, details are not described herein again), generates a fourth IPv6 packet, and sends the fourth IPv6 packet to the final destination node. A source address field in an IPv6 packet header of the fourth IPv6 packet is the IPv6 address of the source node (SA=2001:7a:78a::1), and a destination address field is an IPv6 address of the final destination node (DA=2001:7a:78e::41). An SRH extension header includes SegLeft whose value is 0.
[0050] After receiving the fourth IPv6 packet, the final destination node finds that the DA carried in the fourth IPv6 packet is the IPv6 address of the final destination node, and continues to parse out SegLeft carried in the SRH extension header. Then, if determining that SegLeft (whose value is 0) is equal to 0, the final destination node does not process the SRH, and continues to process a remaining part of the fourth IPv6 packet.
[0051] The foregoing describes the possible application scenario related to the present invention and the segment routing technology, and based on this, the following further describes the embodiments of the present invention in detail.
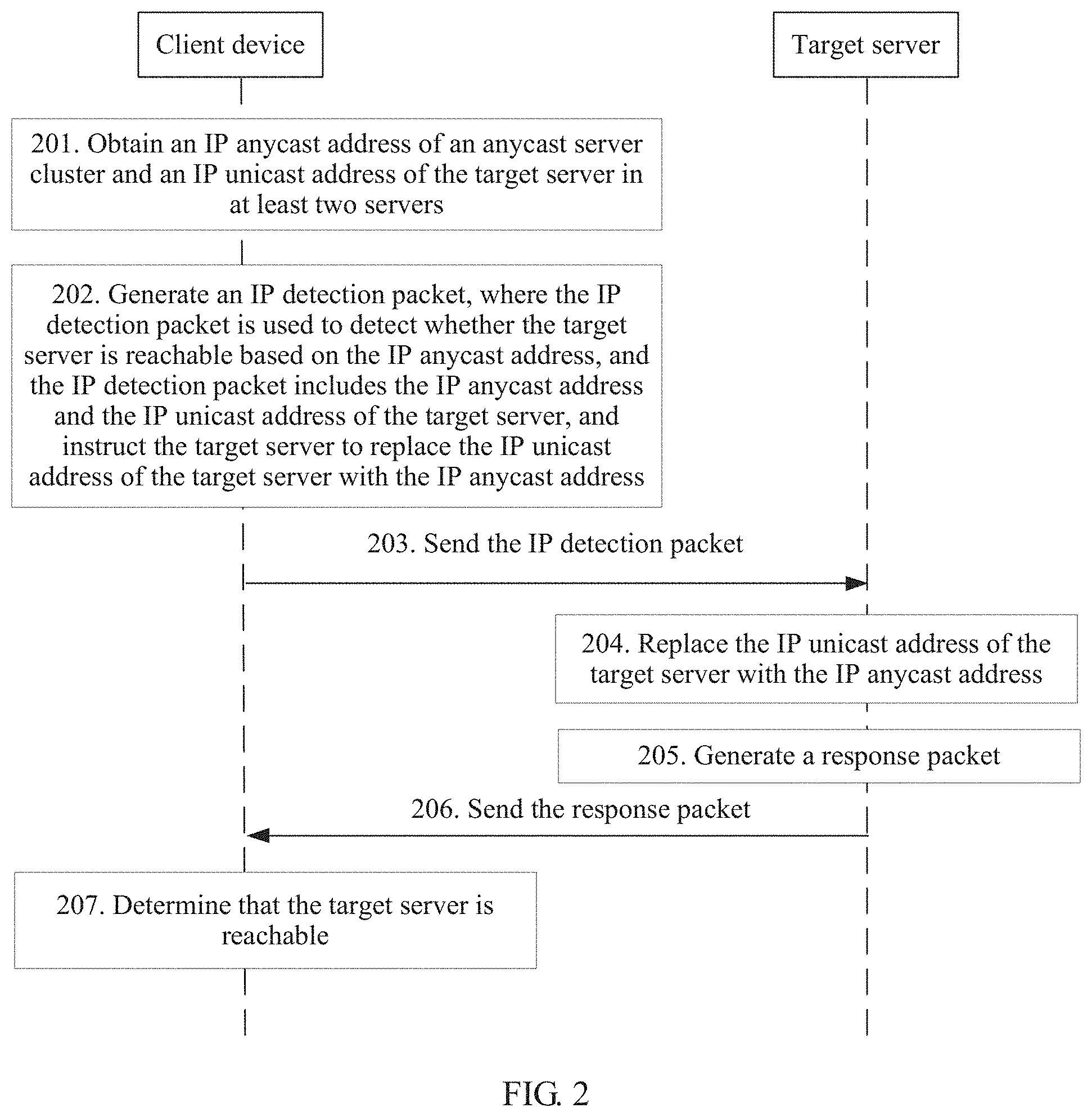
[0052] FIG. 2 is a schematic flowchart of a packet sending method according to an embodiment of the present invention. The method is applied to an anycast service-based network, the network includes a client device and an anycast server cluster, and the anycast server cluster includes a target server.
[0053] The solution provided in this embodiment of the present invention includes parts 201, 202, 203, 204, 205, 206, and 207. The following separately describes the parts.
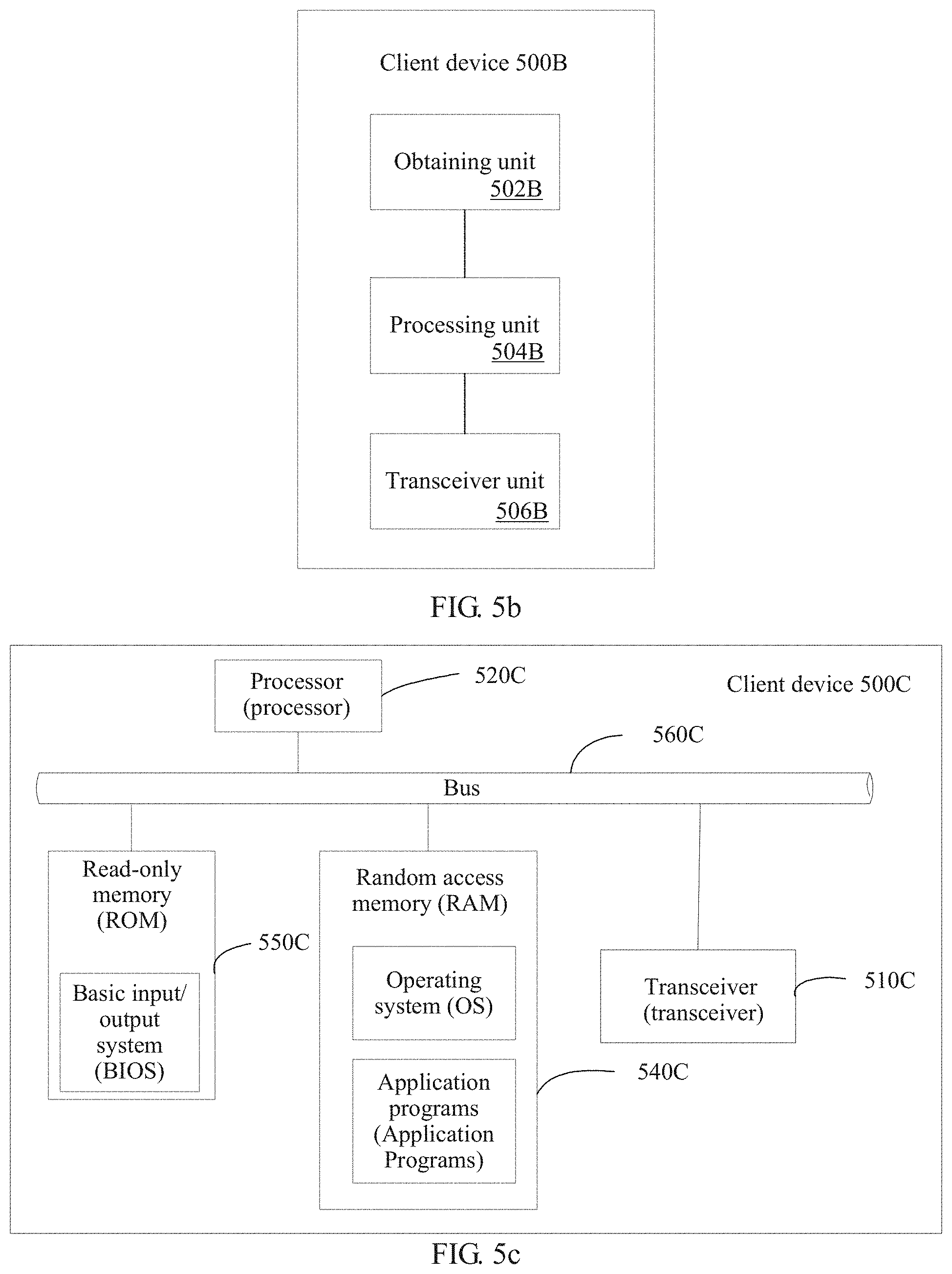
[0054] 201. The client device obtains an IP anycast address of the anycast server cluster and an IP unicast address of the target server.
[0055] The IP anycast address of the anycast server cluster and the IP unicast address of the target server may be configured on the client device by a network administrator by using a command line, or may be obtained from a message that is sent by another control management device and that is received by the client device.
[0056] In a specific implementation, a command line in the following form is executed on a detection initiating device (the client device):
TABLE-US-00001 ping ip -exh <addr0><server1-addr> or tracert ip -exh <addr0><server1-addr>
[0057] -exh <addr0> is an optional parameter added to indicate that an extension field is carried in an IP detection packet. The extension field may be an extension header. <addr0> is an anycast address encapsulated in the extension field. <server1-addr> is a non-anycast IP address that is on a server (for example, a server 1) in a detected anycast server cluster and that is used to identify the server 1, for example, an IP address of an interface on the server or a management IP address of the server.
[0058] A to-be-detected server in the anycast server cluster may be flexibly designated as required by configuring a command line or by receiving a configuration parameter sent by the control management device.
[0059] In another specific implementation, if the client device further obtains an IP unicast address of at least one designate middle node on a forwarding path from the client device to the target server, a command line in the following form is executed on a detection initiating device (the client device):
TABLE-US-00002 ping ip -exh <addr0><server1-addr> -designate_middlenodes <node1, ..., nodeN> or tracert ip -exh <addr0><server1-addr> -designate_middlenode <node1, ..., nodeN>
[0060] -designate_middlenodes is an optional parameter added to indicate that an IP detection packet needs to pass through N designate middle nodes: a node 1, . . . , and a node N in sequence. N is a positive integer greater than or equal to 1.
[0061] It should be noted that -exh is only an example to indicate that a new extension field needs to be added to the packet, and does not constitute any limitation. For example, if the extension field is an SRH extension header, -exh may be -srh. Similarly, -designate_middlenode is only an example to indicate that an extension field needs to be added to the packet, and does not constitute any limitation.
[0062] It should be further noted that ip in the command line may be IPv4 or IPv6, and no limitation is imposed herein.
[0063] A middle node that needs to be included on a to-be-detected path is designated by configuring a command line or receiving a configuration parameter sent by the control management device, so that the middle node that needs to be included on the to-be-detected path and a to-be-detected server in the anycast server cluster may be flexibly designated as required.
[0064] 202. The client device generates an IP detection packet, where the IP detection packet is used to detect whether the target server is reachable based on the IP anycast address, and the IP detection packet includes the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address.
[0065] The IP detection packet is a packet used to perform IP reachability detection, for example, a ping or tracert packet. The ping or tracert packet is encapsulated in a payload part of the IP packet.
[0066] In a specific implementation, when the path from the client device to the target server does not include a designate middle node, a destination IP address field (a destination IP address field in an IP packet header) in the IP detection packet carries the IP unicast address of the target server. The IP detection packet carries the IP anycast address by carrying a Segment Routing Header (SRH), and instructs the target server to replace the IP unicast address of the target server with the IP anycast address.
[0067] Specifically, a segment list field in the segment routing header SRH in the IP detection packet carries the IP anycast address, and a value 1 of a segment left SegLeft field in the SRH instructs the target server to replace the IP unicast address of the target server with the IP anycast address. A specific procedure is described in detail by using an example in the following part of FIG. 3. It should be noted that the value of the SegLeft field is set to 1 plus a quantity of designate middle nodes. When no middle node is designated, a quantity of designate middle nodes is 0, and the value of the SegLeft field is 0+1=1.
[0068] The IP detection packet carries the SRH to carry the IP anycast address, and the value 1 of SegLeft is used to instruct the target server to replace the IP unicast address of the target server with the IP anycast address, so that the IP detection packet can be sent to the IP anycast address of a server in the anycast server cluster simply and accurately.
[0069] In another specific implementation, when the path from the client device to the target server includes a designate middle node, the value of the SegLeft field in the SRH is 1 plus a quantity of designate included middle nodes. Each time the IP detection packet passes through one middle node, the value of SegLeft is subtracted by 1. When the IP detection packet arrives at the target server, the value of SegLeft is 1, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address. A specific procedure is described in detail in the following part of FIG. 4.
[0070] The IP detection packet carries the SRH to carry the IP anycast address, the IP unicast address of the designate middle node, and the IP unicast address of the target server, and the value 1 of SegLeft is used to instruct the target server to replace the IP unicast address of the target server with the IP anycast address, so that the IP detection packet can be sent to the IP anycast address of a server in the anycast server cluster simply and accurately by using the designate middle node.
[0071] 203. The client device sends the IP detection packet to the target server.
[0072] The IP detection packet carries the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address. This helps accurately detect IP anycast address reachability of a designate anycast server.
[0073] 204. The target server receives the IP detection packet, learns through parsing that a destination IP address carried in an IP header of the encapsulated detection packet is a local IP unicast address of the target server, and replaces the IP anycast address with the IP unicast address of the target server according to the instruction of replacing the IP anycast address with the IP unicast address of the target server.
[0074] 205. The target server continues to perform protocol processing on the IP detection packet to generate a response packet.
[0075] 206. The target server sends the response packet to the client device.
[0076] 207. When receiving the response packet within a predetermined time interval, the client device determines that the target server is reachable based on the IP anycast address.
[0077] In a possible embodiment, when the response packet is not received within the predetermined time interval, the client device determines that the target server is unreachable based on the IP anycast address, for example, a fault occurs.
[0078] Whether the target server is reachable based on the IP anycast address (for example, whether a fault occurs) can be accurately determined based on whether the response packet to IP detection can be received within the predetermined time interval.
[0079] The foregoing parts 201 to 207 are described by using the network scenario shown in FIG. 1a as an example. If the client device (the detection initiating device) needs to detect whether the server 1 in the anycast server cluster works normally, the client device initiates IPv6 ping detection. The IPv6 ping detection may be implemented in two manners. In one manner, a middle node is designated. In the other manner, no middle node is designated.
[0080] A packet forwarding procedure in which no middle node is designated is first described in detail with reference to FIG. 3. The client device executes a command line in the following form: [0081] ping ipv6 -srh <addr0><addr1>
[0082] -srh <addr0> is used to indicate that an SRH extension header is carried in an IP detection packet, and an anycast address addr0 is carried in a segment list field in the SRH. For example, as shown in FIG. 3, a value of a segment left field is set to 1, and addr0 is carried in a Segment List [0] field. A destination address field in an IPv6 packet header carries addr1. addr1 is a non-anycast IP address that is on the server 1 in the detected anycast server cluster and that is used to identify the server 1. A next header field in the SRH indicates the IGMP protocol. To be specific, a ping packet may continue to be encapsulated in the IPv6 packet. add1 is an IP unicast address that is on the server 1 in the detected anycast server cluster and that is used to identify the server 1.
[0083] The client device generates the IPv6 packet used to perform ping detection. Because a segment left value in the SRH in the IPv6 packet is 1, greater than 0, it means that when an IP address of the target server is addr1, the client device continues to parse the SRH, subtracts the segment left value in the SRH by 1, and replaces the destination IP address in the IPv6 packet header with an IP address corresponding to Segment List [the segment left value subtracted by 1] (=Segment List [0]=addr0), to be specific, replaces addr1 in the IPv6 packet header with addr0.
[0084] The client device sends the IPv6 packet to the server 1. In a network including R1, R2, and R3, the IPv6 packet is sent to the server 1 through R1 and R2 by searching for a routing and forwarding entry corresponding to the destination IP address addr1.
[0085] After receiving the IPv6 packet, the server 1 finds, through parsing, that a DA (addr1) carried in the IPv6 packet is an IPv6 address of the server 1, and continues to parse out SegLeft carried in the SRH extension header. A value of SegLeft is 1, greater than 0. Therefore, it means that when the IP address of the target server is addr1, the server 1 continues to parse out the SRH, subtracts the segment left value in the SRH by 1, and replaces the destination IP address in the IPv6 packet header with an IP address corresponding to Segment List [the segment left value subtracted by 1] (=Segment List [0]=addr0), to be specific, replaces addr1 in the IPv6 packet header with addr0.
[0086] The server 1 continues to perform protocol processing on the ping detection packet, generates a response packet, and sends the response packet to the client device. After receiving the response packet, the client device determines that the target server is reachable.
[0087] Through FIB table search based on addr1 used as a destination address and forwarding by the router 1 and the router 2, the ping detection packet is sent to the server 1. When the server 1 is faulty, the server 1 cannot receive and process the IPv6 packet, nor generate the response packet and send the response packet to the client device. Therefore, when the client device fails to receive the response packet of the server 1 within a time interval or a period, it is determined that the server 1 is unreachable, and a fault may occur.
[0088] It should be noted that the segment list array may carry addr1 (as shown in FIG. 3), or may not carry addr1, and a same function may be implemented in both cases.
[0089] Next, another packet forwarding procedure in which a middle node is designated is described in detail with reference to FIG. 4. The client device executes a command line in the following form: [0090] ping ipv6 -srh <addr0><addr1> -designate_middlenode <addr3, addr2>
[0091] -srh <addr0> is used to indicate that an SRH extension header is carried in an IP detection packet, and an anycast address addr0 is carried in a segment list field in the SRH. -designate_nodes <addr3, addr2> is used to indicate that two designate middle nodes: addr3 (the router 1) and addr2 (the router 2) need to be sequentially included in ping detection. For example, as shown in FIG. 4, a value of a segment left field is set to 3 (that is, the SRH needs to carry four addresses) as 1 plus a quantity (2) of designate middle nodes is equal to 3, addr0 is carried in a Segment List [0] field, addr1 is carried in a Segment List [1] field, addr2 is carried in a Segment List [2] field, and addr3 is carried in a Segment List [3] field. A destination address (DA) field in an IPv6 packet header carries addr3. addr3 is an IP address of the first middle node Router1. A next header field in the SRH indicates the IGMP protocol. To be specific, a ping packet may continue to be encapsulated in the IPv6 packet.
[0092] The client device generates a first IPv6 packet that is used to perform ping detection and that is to be sent to the router 1. After receiving the packet, the router 1 performs SRH forwarding processing, generates a second IPv6 packet, and sends the second IPv6 packet to the second middle node Router 2. The router 2 performs SRH forwarding processing, generates a third IPv6 packet, and sends the third IPv6 packet to the destination node (the target server server)). A principle of SRH forwarding processing procedures on the router 1 and the router 2 is consistent with that of the forwarding procedure in FIG. 1c-1 and FIG. 1c-2. For the procedures, refer to FIG. 1c-1 and FIG. 1c-2. For brevity, details are not described again.
[0093] After receiving the third IPv6 packet, the server 1 finds, through parsing, that a DA (addr1) carried in the third IPv6 packet is an IPv6 address of the server 1, and continues to parse out SegLeft carried in the SRH extension header. A value of SegLeft is 1, greater than 0. Therefore, it means that when the IP address of the target server is addr1, the server 1 continues to parse out the SRH, subtracts the segment left value in the SRH by 1, and replaces the destination IP address in the IPv6 packet header with an IP address corresponding to Segment List [the segment left value subtracted by 1] (=Segment List [0]:=addr0), to be specific, replaces addr1 in the IPv6 packet header with addr0.
[0094] Subsequent processing of the server 1 is consistent with the foregoing part in FIG. 3. For the subsequent processing, refer to FIG. 3. For brevity, details are not described again.
[0095] It should be noted that, for details about the SRH extension packet header in the present invention, refer to the document draft-ietf-6man-segment-routing-header-07 published by the internet engineering task force (Internet Engineering Task Force, IETF). Content of a related part in the document is incorporated herein by reference, appearing as entirely copied. For brevity, details are not described herein.
[0096] It should be further noted that IP addresses present in this specification refer to IP unicast addresses unless otherwise specified.
[0097] FIG. 5a is a possible schematic structural diagram of the client device in the foregoing embodiments. The client device 500A is applied to an anycast service-based network, the network includes a client device and an anycast server cluster, the anycast server cluster includes at least two servers, and the at least two servers have a same IP anycast address. The client device 500A includes a main control board 510, an interface board 530, a switching board 520, and an interface board 540. The main control board 510 is configured to complete functions such as system management, device maintenance, and protocol processing. The switching board 520 is configured to complete data exchange between interface boards (the interface board is also referred to as a line card or a service board). The interface board 530 and the interface board 540 are configured to provide various service interfaces (for example, an ethernet interface and a POS interface) and forward a data packet. The main control board 510, the interface board 530, the interface board 540, and the switching board 520 are connected to a platform backboard by using a system bus for interworking. A central processing unit 531 on the interface board 530 is configured to control and manage the interface board, and communicate with a central processing unit 511 on the main control board 510. The central processing unit 511 on the main control board 510 is further configured to obtain the IP anycast address of the anycast server cluster and an IP unicast address of a target server, and generate an IP detection packet. The IP detection packet is used to detect whether the target server is reachable based on the IP anycast address. The IP detection packet includes the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address.
[0098] In a possible embodiment, when a path from the client device to the target server does not include a designate middle node, a destination IP address field in the IP detection packet carries the IP unicast address of the target server, a segment list field in an IP segment routing header SRH in the IP detection packet carries the IP anycast address, a value of a segment left SegLeft field in the IP SRH is 1, and the value of the SegLeft field instructs the target server to replace the IP unicast address of the target server with the anycast address.
[0099] In another possible embodiment, when a path from the client device to the target server includes a designate middle node, the central processing unit 511 on the main control board 510 further obtains an IP unicast address of at least one designate middle node on the forwarding path from the client device to the target server. A destination IP address field in the IP detection packet carries an IP unicast address of a first designate middle node, and the first designate middle node is a first designate middle node on the forwarding path from the client device to the target server. A segment list field in an IP segment routing header SRH in the IP detection packet carries the IP anycast address, the IP unicast address of the target server, and the IP unicast address of the at least one designate middle node, a value of a SegLeft field in the IP SRH is 2 plus a quantity of designate middle nodes, and the value of the SegLeft field instructs the target server to replace the IP unicast address of the target server with the IP anycast address.
[0100] The central processing unit 511 on the main control board 510 queries a local routing table by using a destination IP address of the IP detection packet to find the interface board 530 on which an outbound interface is located, and then delivers the IP detection packet to the central processing unit 531.
[0101] The central processing unit 531 performs internal adaptation processing (for example, interface index conversion) on the IP detection packet by querying a forwarding entry storage 534, and then delivers the IP detection packet to a network processor 532.
[0102] The network processor 532 sends the IP detection packet out from a physical interface card 533 after completing link layer encapsulation based on information such as the outbound interface.
[0103] The physical interface card 533 receives, within a predetermined time interval, a response packet sent by the target server, and sends the response packet to the network processor 532. The network processor 532 sends, by using the central processing unit 531, the response packet upward to the main control board 510 based on a result of searching the forwarding entry storage 534. In this case, the central processing unit 511 determines that the target server is reachable based on the IP anycast address.
[0104] When the central processing unit 511 on the main control board 510 receives, within the predetermined time interval, no response packet sent by the target server, the central processing unit 511 determines that the target server is unreachable based on the IP anycast address.
[0105] It should be understood that an operation on the interface board 540 is consistent with an operation on the interface board 530 in this embodiment of the present invention. For brevity, details are not described. It should be understood that the client device 500A in this embodiment may correspond to the client device in the embodiments corresponding to FIG. 1a to FIG. 4. The main control board 510, and the interface board 530 and/or the interface board 540 in the client device 500A may implement functions of and/or steps implemented by the client device in the embodiments corresponding to FIG. 1a to FIG. 4. For brevity, details are not described herein again.
[0106] It should be noted that, there may be one or more main control boards. When there are a plurality of main control boards, the plurality of main control boards may include a primary main control board and a secondary main control board. There may be one or more interface boards, and a forwarding device with a stronger data processing capability provides more interface boards. There may be one or more physical interface cards on the interface board. There may be no switching board, or there may be one or more switching boards. When there are a plurality of switching boards, load balancing and redundancy backup may be jointly implemented by the plurality of switching boards. In a centralized forwarding architecture, a forwarding device may not need a switching board, and an interface board is responsible for a service data processing function of an entire system. In a distributed forwarding architecture, a forwarding device may include at least one switching board, and data is exchanged between a plurality of interface boards by using the switching board, to provide a large-capacity data exchange and processing capability. Therefore, a data access and processing capability of the forwarding device in the distributed architecture is stronger than that of the device in the centralized architecture. Optionally, in another form of the forwarding device 500A, there may be only one card. In other words, there is no switching board, and functions of the interface board and the main control board are integrated on the one card. In this case, a central processing unit on the interface board and a central processing unit on the main control board may be combined into one central processing unit on the card, to perform functions of the two central processing units after combination. A device in this form (for example, a network device such as a low-end switch or router) has a relatively weak data exchange and processing capability. A specific architecture to be used depends on a specific networking deployment scenario. This is not limited herein.
[0107] FIG. 5b is another possible schematic structural diagram of the client device in the foregoing embodiments. The client device 500B is applied to an anycast service-based network, the network includes a client device and an anycast server cluster, the anycast server cluster includes at least two servers, and the at least two servers have a same IP anycast address. The client device 500B includes a processing unit 504B, an obtaining unit 502B, and a transceiver unit 506B.
[0108] The obtaining unit 502B is configured to obtain the IP anycast address of the anycast server cluster and an IP unicast address of a target server. The processing unit 504B is configured to generate an IP detection packet. The IP detection packet is used to detect whether the target server is reachable based on the IP anycast address, and the IP detection packet includes the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address. The transceiver unit 506B is configured to send the IP detection packet to the target server.
[0109] In a specific implementation, when a path from the client device to the target server does not include a designate middle node, the obtaining unit 502B is further configured to obtain the IP anycast address and the IP unicast address of the target server by using a user-configured command line. Alternatively, the obtaining unit 502B is further configured to receive a message sent by a control management device, and obtain the IP anycast address and the IP unicast address of the target server from the message.
[0110] Correspondingly, a method for carrying related information by carrying an SRH in the IP detection packet is consistent with that described in the foregoing part 202. Refer to related content, and details are not described again.
[0111] In another specific embodiment, when a path from the client device to the target server includes a designate middle node, the obtaining unit 502B is further configured to obtain an IP unicast address of at least one designate middle node on the forwarding path from the client device to the target server. The obtaining unit 502B is further configured to obtain the IP unicast address of the at least one designate middle node by using a user-configured command line. Alternatively, the obtaining unit 502B is further configured to receive a message sent by the control management device, and obtain the IP unicast address of the at least one designate middle node from the message.
[0112] Correspondingly, a method for carrying related information by carrying an SRH in the IP detection packet is consistent with that described in the foregoing part 202. Refer to related content, and details are not described again.
[0113] When the transceiver unit 506B receives, within a predetermined time interval, a response packet sent by the target server, the processing unit 504B determines that the target server is reachable based on the IP anycast address.
[0114] When the transceiver unit 506B receives, within the predetermined time interval, no response packet sent by the target server, the processing unit 504B determines that the target server is unreachable based on the IP anycast address.
[0115] The client device 500B in this embodiment of the present invention may correspond to the client device in the foregoing packet sending method embodiments, and modules and the other operations and/or functions of the client device 500B are separately used to implement steps and methods that are implemented by the client device in the embodiments corresponding to FIG. 1a to FIG. 4. For brevity, details are not described herein again.
[0116] FIG. 5c is a possible schematic structural diagram of the client device in the foregoing embodiments. The client device 500C is applied to an anycast service-based network, the network includes a client device and an anycast server cluster, the anycast server cluster includes at least two servers, and the at least two servers have a same IP anycast address. The client device 500C includes a transceiver 510C, a processor 520C, a random access memory 540C, a read-only memory 550C, and a bus 560C. The processor 520C is separately coupled to the transceiver 510C, the random access memory 540C, and the read-only memory 550C by using the bus 560C. When the forwarding device 500C needs to be run, a bootloader in a basic input/output system or an embedded system that is built into the read-only memory 550C is used to lead a system to start, and lead the forwarding device 500C to enter a normal running state. After the forwarding device 500C enters the normal running state, an application program and an operating system are run in the random access memory 540C, to implement the following functions.
[0117] The processor 520C is configured to obtain the IP anycast address of the anycast server cluster and an IP unicast address of a target server, and generate an IP detection packet. The IP detection packet is used to detect whether the target server in the at least two servers is reachable based on the IP anycast address. The IP detection packet includes the IP anycast address and the IP unicast address of the target server, and instructs the target server to replace the IP unicast address of the target server with the IP anycast address. The transceiver 510C is configured to send the IP detection packet to the target server.
[0118] The forwarding device 500C in this embodiment of the present invention may correspond to the client device in the embodiments corresponding to FIG. 1a to FIG. 4. In addition, the processor 520C, the transceiver 510C, and the like in the client device 500C may implement functions of and/or steps and methods implemented by the client device in the embodiments corresponding to FIG. 1a to FIG. 4. The processor 520C is configured to perform all operations of the processing unit 504B and the obtaining unit 502B of the client device in FIG. 5b, and the transceiver 510C is configured to perform all operations of the transceiver unit 506B of the client device in FIG. 5b. For brevity, details are not described herein again.
[0119] It should be noted that, in this embodiment, the client device may alternatively be implemented based on a common physical server and a Network Function Virtualization (NFV) technology, and the client device is a virtual client device (for example, a virtual host, a virtual router, or a virtual switch). The virtual client device may be a Virtual Machine (VM) that runs a program used to send a packet, and the virtual machine is deployed on a hardware device (for example, a physical server). The virtual machine is a complete computer system that is simulated by using software, that has functions of a complete hardware system, and that runs in a completely isolated environment. After reading this application, a person skilled in the art may obtain, on a common physical server by using the NFV technology, a plurality of virtualized forwarding devices with the foregoing functions. Details are not described herein.
[0120] It should be understood that, based on this application, a person skilled in the art can combine optional features, steps, or methods that are described in the embodiments of this application without creative efforts, and this belongs to the embodiments disclosed in this application. For brevity, descriptions of different combinations are not repeatedly provided.
[0121] The term "and/or" in this specification describes only an association relationship for describing associated objects and represents that three relationships may exist. For example, A and/or B may represent the following three cases: Only A exists, both A and B exist, and only B exists. In addition, the character "/" in this specification generally indicates an "or" relationship between the associated objects.
[0122] It should be understood that sequence numbers of the foregoing processes do not mean execution sequences in the embodiments of the present invention. The execution sequences of the processes should be determined based on functions and internal logic of the processes, and should not be construed as any limitation on the implementation processes of the embodiments of the present invention.
[0123] A person of ordinary skill in the art may be aware that, in combination with the examples described in the embodiments disclosed in this specification, units and algorithm steps may be implemented by electronic hardware or a combination of computer software and electronic hardware. Whether the functions are performed by hardware or software depends on particular applications and design constraint conditions of the technical solutions. A person skilled in the art may use different methods to implement the described functions for each particular application, but it should not be considered that the implementation goes beyond the scope of the present invention.
[0124] It may be clearly understood by a person skilled in the art that, for the purpose of convenient and brief description, for a detailed working process of the foregoing system, apparatus, and unit, refer to a corresponding process in the foregoing method embodiments, and details are not described herein again.
[0125] In the several embodiments provided in this application, it should be understood that the disclosed system, apparatus, and method may be implemented in other manners. For example, the described apparatus embodiment is merely an example. For example, the unit division is merely logical function division and may be other division in actual implementation. For example, a plurality of units or components may be combined or integrated into another system, or some features may be ignored or not performed. In addition, the displayed or discussed mutual couplings or direct couplings or communication connections may be implemented by using some interfaces. The indirect couplings or communication connections between the apparatuses or units may be implemented in electronic, mechanical, or other forms.
[0126] The units described as separate parts may or may not be physically separate, and parts displayed as units may or may not be physical units, may be located in one position, or may be distributed on a plurality of network units. Some or all of the units may be selected based on actual requirements to achieve the objectives of the solutions of the embodiments.
[0127] In addition, functional units in the embodiments of the present invention may be integrated into one processing unit, or each of the units may exist alone physically, or two or more units are integrated into one unit.
[0128] When the functions are implemented in the form of a software functional unit and sold or used as an independent product, the functions may be stored in a computer readable storage medium. Based on such an understanding, the technical solutions of the present invention essentially, or the part contributing to the prior art, or some of the technical solutions may be implemented in a form of a software product. The computer software product is stored in a storage medium, and includes several instructions for instructing a computer device (which may be a personal computer, a server, a network device, or the like) to perform all or some of the steps of the methods described in the embodiments of the present invention. The foregoing storage medium includes: any medium that can store program code, such as a USB flash drive, a removable hard disk, a read-only memory (ROM, Read-Only Memory), a random access memory (RAM, Random Access Memory), a magnetic disk, or an optical disc.
[0129] The foregoing descriptions are merely specific implementations of the present invention, but are not intended to limit the protection scope of the present invention. Any variation or replacement readily figured out by a person skilled in the art within the technical scope disclosed in the present invention shall fall within the protection scope of the present invention. Therefore, the protection scope of the present invention shall be subject to the protection scope of the claims.
* * * * *
D00000

D00001

D00002

D00003

D00004

D00005

D00006

D00007

D00008

D00009

XML
uspto.report is an independent third-party trademark research tool that is not affiliated, endorsed, or sponsored by the United States Patent and Trademark Office (USPTO) or any other governmental organization. The information provided by uspto.report is based on publicly available data at the time of writing and is intended for informational purposes only.
While we strive to provide accurate and up-to-date information, we do not guarantee the accuracy, completeness, reliability, or suitability of the information displayed on this site. The use of this site is at your own risk. Any reliance you place on such information is therefore strictly at your own risk.
All official trademark data, including owner information, should be verified by visiting the official USPTO website at www.uspto.gov. This site is not intended to replace professional legal advice and should not be used as a substitute for consulting with a legal professional who is knowledgeable about trademark law.