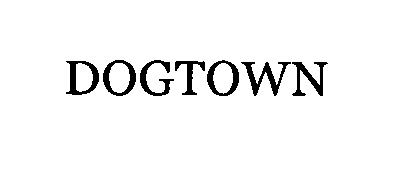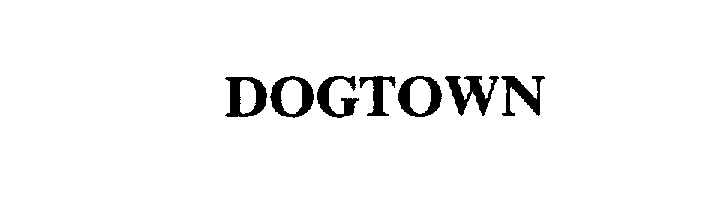MUIR, JAMES
USPTO Trademark & Patent Filings
Trademark applications and grants for Muir, James. Muir, James has 7 trademark applications. The latest application filed is for "DOGTOWN"
- Company Aliases
- Muir, James
- james muir
- Muir; James - Ottawa CA
- Muir; James - Kanata CA
- MUIR; James - Ottawa CA
| Entity Type | INDIVIDUAL |
| Address | 2567 WALNUT AVENUE VENICE, CALIFORNIA UNITED STATES 90291 |
Trademarks Patents
| NCAGE Code | 37RL0 | MUIR JAMES!DBA DESERT PUMP |
| CAGE Code | 37RL0 | MUIR, JAMES DESERT PUMP |
| DUNS | 032520285 | MUIR, JAMES |
uspto.report is an independent third-party trademark research tool that is not affiliated, endorsed, or sponsored by the United States Patent and Trademark Office (USPTO) or any other governmental organization. The information provided by uspto.report is based on publicly available data at the time of writing and is intended for informational purposes only.
While we strive to provide accurate and up-to-date information, we do not guarantee the accuracy, completeness, reliability, or suitability of the information displayed on this site. The use of this site is at your own risk. Any reliance you place on such information is therefore strictly at your own risk.
All official trademark data, including owner information, should be verified by visiting the official USPTO website at www.uspto.gov. This site is not intended to replace professional legal advice and should not be used as a substitute for consulting with a legal professional who is knowledgeable about trademark law.